RapidIdentity Authentication Policies - Best Practices
RapidIdentity Cloud provides dynamic end-user authentication methods to support a secure, seamless digital ecosystem focused on learning outcomes. Authentication can be tailored to the needs of individual end users. Students, teachers, and administrators can each authenticate securely with a single login policy that is appropriate for their needs and risk levels.
Authentication Overview
- Multi-step authentication: A user is required to use two or more of the same factor.
While this option is more secure, it is not the most secure. However, it is more appropriate in K-12 education for younger learners for true MFA.
- Two-factor authentication: user is required to use two different factors.
- Multi-factor (MFA) authentication: user is required to use three different factors. This is the most secure.
- Device authentication depends on the environment being used, and can use Federation or the RapidIdentity Windows Authentication Client to authenticate into RapidIdentity.
Authentication Factors
- Type 1: Something you know (Password, Challenge, PIN, Pictograph)
- Type 2: Something you have (FIDO, TOTP, QR Code, Duo, Email, SMS, PingMe)
- Type 3: Something you are (Kerberos, Biometrics, WebAuthn)
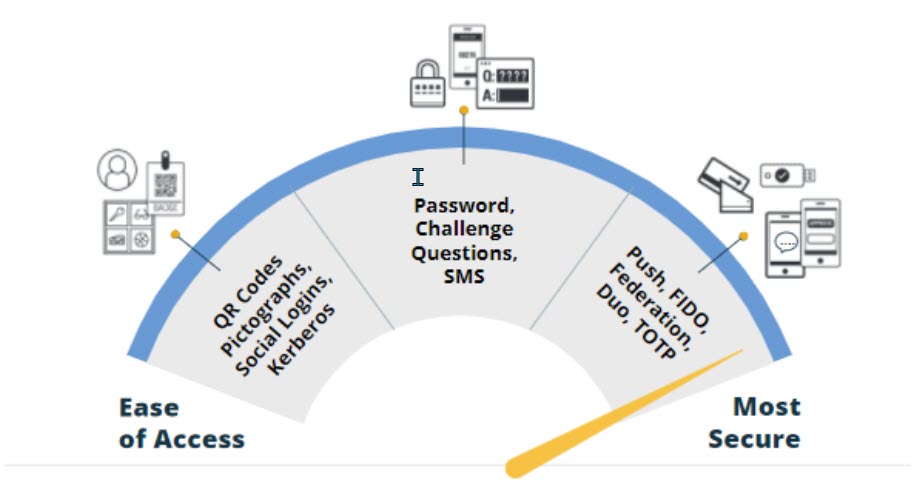
Rationale for Authentication Policies
Passwords: Passwords are a standard practice for system access and can be effective as long as they are strong, secure, and not reused across systems. The challenge facing password use today is the high number of data breaches and end-user passwords that have been compromised but are still in use. Any time a user has the same username and password across multiple systems, it increases susceptibility to account compromise and data breaches. Using alternate authentication methods and two-factor or multi-factor authentication increases your district/institution's security posture.
Alternate Authentication Methods: Alternate authentication methods move away from passwords and allow more secure access to systems. Using a device, security tokens, biometrics, and other methods will grant end users secure entry to a system with a dependency on passwords.
Two-Factor and Multi-Factor Authentication: Multiple authentication methods facilitate user login while confirming user identity for the most secure access to a system. The best practice for multi-factor authentication is to require users to have all three factors: Something they have, know, and are to log in. Two-factor authentication only requires two of the three factors.
Authentication Configuration in RapidIdentity Cloud
End users in RapidIdentity can be assigned one or more specific authentication methods to access RapidIdentity:
- When involving a third-party software, the authentication method must be configured as applicable in both RapidIdentity and the third party as needed. (e.g., Duo, Kerberos)
- Authentication methods are assigned to users within RapidIdentity Identity Store based on user attributes.
- A specific authentication order can be set for end users.
- Any authentication policy can have multiple methods to ensure two-factor or multi-factor authentication.
- Multiple policies can apply to users to ensure there is always a method for the user to get in (for example, if a user doesn't have their phone for SMS, they can fall back to a token, challenge question, or TOTP authentication method).
Supported Authentication Methods in RapidIdentity Cloud
| Method | Description | Considerations |
|---|---|---|
| Duo* | Users authenticate with a preconfigured Duo account | Available when Duo software is in place and configured. |
| Users authenticate through a RapidIdentity email address. | Available if personal emails are stored in RapidIdentity. | |
| Federation | This allows for authentication to an alternate Identity Provider (IdP). | Available when another Identity Provider is necessary (e.g., ADFS, Okta). In this configuration, RapidIdentity is the Service Provider. |
| WebAuthn* | Allows users to authenticate with biometrics set up through Windows Hello. | Requires biometrics set up with Windows Hello, including facial scans, thumbprint keys, or PIN. |
| Kerberos | Users authenticate with their password. | Typically available in AD environments. This will allow end users on a domain-joined computer to use the login token for authentication. |
| Pictograph | Users can authenticate against the default image pool. By default, the user is required to select three images. | Recommended for younger students, such as PreK-12 or students with special needs. |
| PingMe | Users authenticate using the RapidIdentity Mobile client application on a mobile device. | Requires mobile devices. This method enables push notifications to the RapidIdentity Mobile Client. |
| Portal Challenge (Questions) | Users authenticate with their RapidIdentity Portal Challenge Questions. | Typically used for password recovery. Can also be used as an authentication method. |
| QR Code | When enabled, a valid, secure QR code must be scanned. | QR codes must be printed or photographed and can be scanned to gain access to the system. Recommended for Elementary students or students with special needs. |
| SMS | Users authenticate with a code sent to their mobile device through SMS. | Requires mobile devices. Recommended for teachers and staff members who are able to use SMS authentication. |
| TOTP | Users enter a Time-Based One-Time Password (TOTP) code generated by an app on a device (e.g., Google Authenticator, RapidIdentity Mobile app, or Microsoft Authenticator). | One of the easiest and most user-friendly methods for authentication. Requires a third-party vendor application. |
Device Authentication
With education's diverse and constantly changing user base, ease of access can be leveraged to get people used to a passwordless environment, where they can grow from - literally. As a student progresses through grades and gains more user access/risk, they could go from authentication methods that focus on ease of access (e.g., QR Code, Pictograph, etc.) to more secure methods (e.g., TOTP or FIDO tokens based on their grade level or whether they are logging in from a campus IP address). These are just two examples of contextual policies that should be considered.
In 2020 many major public learning institutions started seriously pursuing university, district, and even statewide MFA programs to pro-actively increase security posture and ensure consistent pricing for cyber security insurance. Many are following the strategy of forming or leveraging an existing committee of diverse department stakeholders. In addition to this they also provide multiple workflows, and opt-in options for end users. This has become a major focus as the requirements for MFA are extending to teachers, and users that may not have institution issued resources to leverage. A teacher refusing to use her own cell phone to download an app administered by her employer is a common occurrence, and justifiably so, but many times it is a case by case basis.
While 95% enjoy the ease of access of using a mobile device for secure authentication. Instead of leaving the 5% unsecured, or forcing them to enroll, these institutions have provided contextual based workflows where users can leverage a mobile device with a third-party or RapidIdentity App, or personal email account to perform a multi-factor login.