Compromised Accounts in RapidIdentity SafeID
Administrative Privileges Required
You must be a Tenant Administrator to manage users in the Compromised Accounts delegation and MFA Authentication Policies.
Whenever an account has been found compromised by a SafeID breached accounts scan, that user will show up in an automatically created Compromised Accounts delegation in the People module.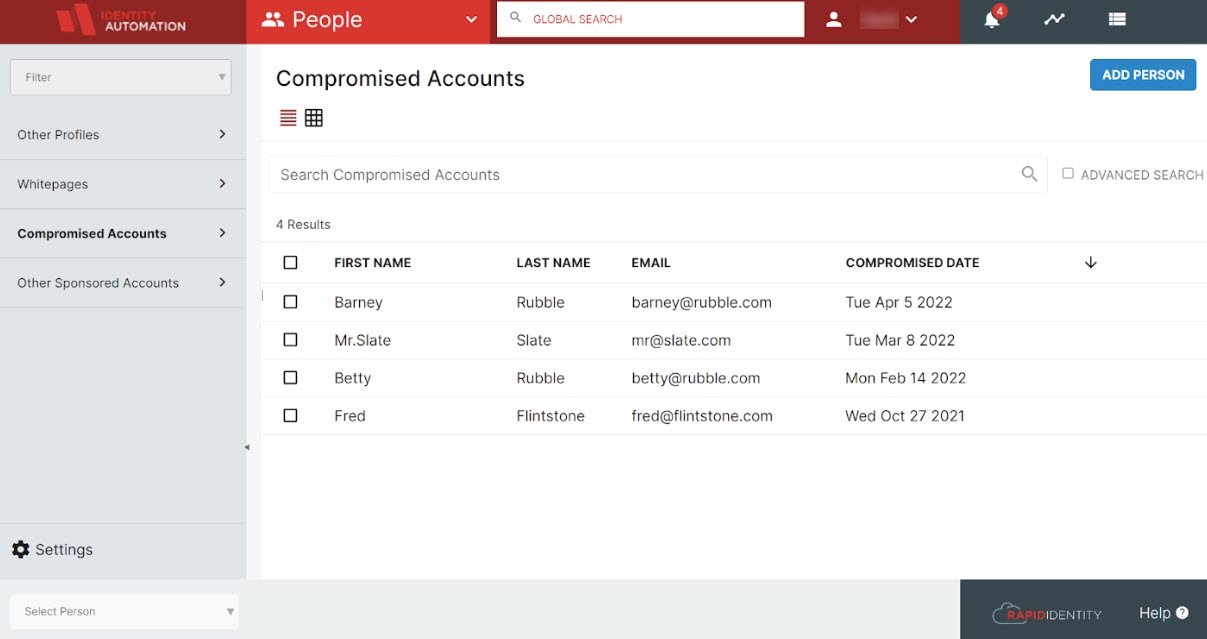
There are four steps that can be taken to secure the compromised account:
Notify the Affected User(s) by Email and/or SMS
In the Compromised Accounts delegation, select the user(s) and choose to Send Email or Send SMS depending on the desired method for that user. The instructions configured within the theme will show in the message that is sent.
To configure the two themes, navigate to Configuration > Security > SafeID to find templates that can be used to notify users that their account has been breached via Email and SMS. These themes will serve to feed the actions from the Compromised Accounts delegation.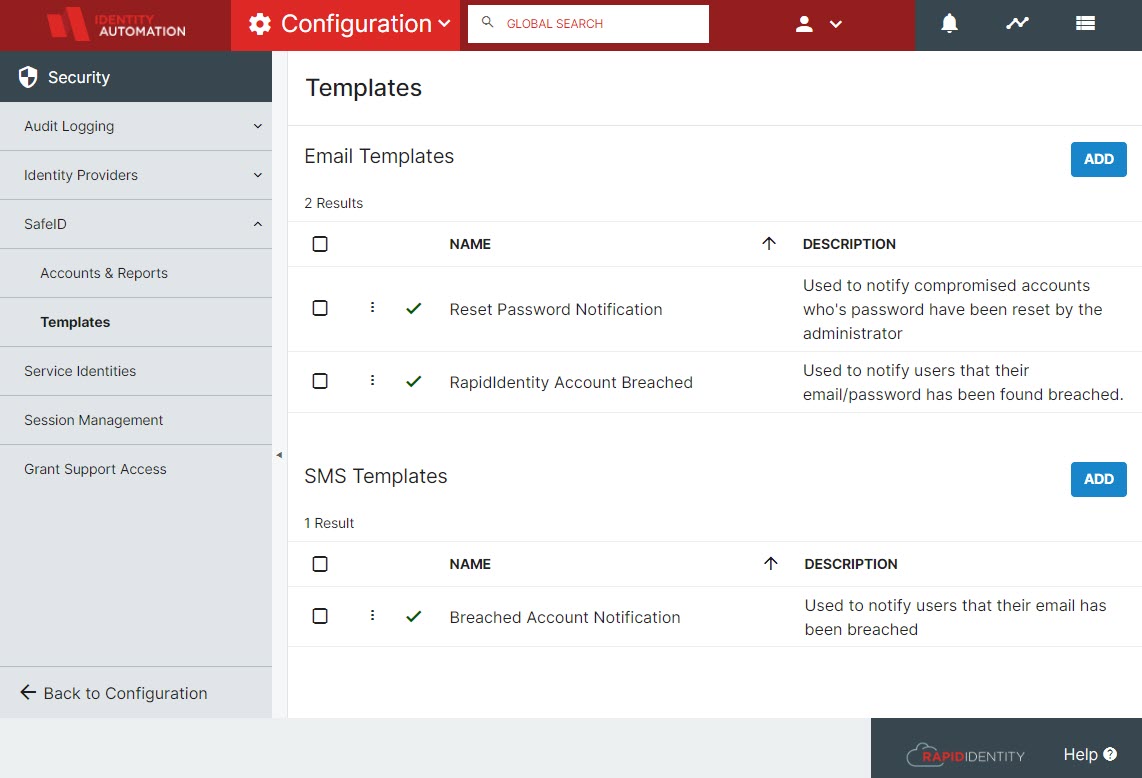
More templates can be set up to address different user types with different messages if needed. In order for the template to be applied, it needs to be Enabled with a green check next to the template Name. To do this, click Edit and check the Enabled box.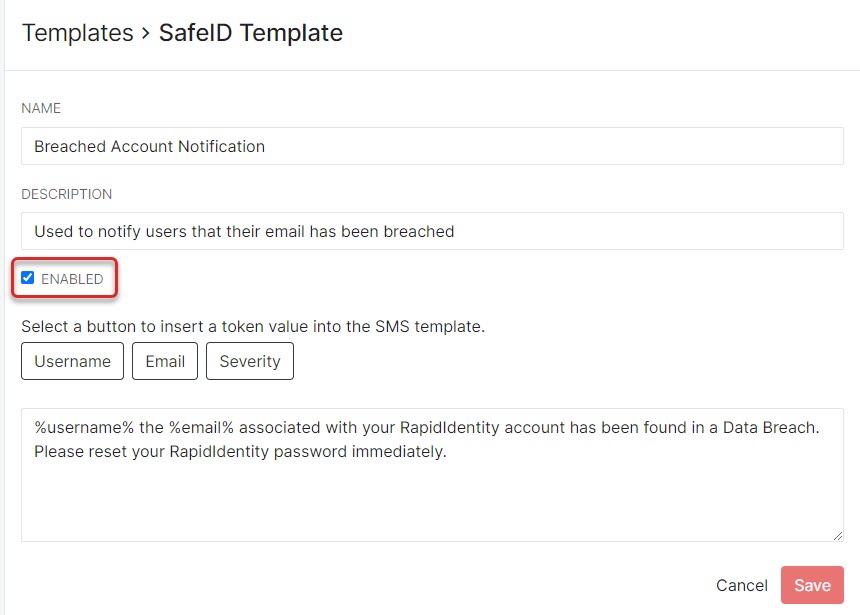
Reset the Affected User's Password
Once a user has been flagged as compromised, any method of changing that user's password will clear the flag. This can be done by the user through Self-Service, Delegations, or Connect. Compromised users who change their passwords through any method will immediately be removed from the Compromised Accounts delegation.
Disable the Affected Account(s)
If the account(s) cannot be resolved for any reason, select the account(s) in the Compromised Accounts delegation. Then click Disable in the bottom action bar.
Enroll the User(s) in MFA
You should also create an Authentication Policy for compromised users, another best practice to prevent breaches.