- 02 Sep 2025
- 4 Minutes to read
- Print
- DarkLight
Phish Wire - September 2 2025
- Updated on 02 Sep 2025
- 4 Minutes to read
- Print
- DarkLight
.png)
In late August, there were notable records of phishing activity involving scams related to Microsoft support, Adobe file sharing, and Paperless Post deliveries. The tactics used included MFA relay kits and the leverage of CloudFlare infrastructure to avoid detection. During this time, there was also a continued focus on targeting personal accounts, such as Amazon and Yahoo, on work devices. Here are some examples and highlights.
tgcj86gcjyp[.]z13[.]web[.]core[.]windows[.]net
hdbn46dhu[.]z13[.]web[.]core[.]windows[.]net
vtgg97gvy[.]z13[.]web[.]core[.]windows[.]net
asdfdgfcb17ygkjhmb[.]z13[.]web[.]core[.]windows[.]net
sfgd9jthg[.]z13[.]web[.]core[.]windows[.]net
hdbn46dhu[.]z13[.]web[.]core[.]windows[.]net
asfzdxgc7jh[.]z13[.]web[.]core[.]windows[.]net
adsdgfc12dgfc[.]z13[.]web[.]core[.]windows[.]net
erf86efgf[.]z13[.]web[.]core[.]windows[.]net
softviewt[.]de/desk/
darkgreen-crocodile-418773[.]hostingersite[.]com
lexinfoinvite[.]online
xed[.]draigoodro[.]com[.]de
peachpuff-turtle-958085[.]hostingersite[.]com
underclothes[.]primesicilia[.]it[.]com
lph5gcy[.]8izfv5f65u[.]workers[.]dev
ekenewrthanmoupasdertghumused[.]net
comforthcruisebookcrise[.]one
Microsoft Spearphish and Support Scams
On August 17th, a staff member in Texas clicked on the Microsoft phishing email below.
This scheme provides the victim with several options for logging in with various accounts, such as Outlook, AOL, Office 365, and Yahoo. It also attempts to steal the target's one-time password (OTP) to bypass multi-factor authentication. Additionally, the scheme features a fake Cloudflare challenge to avoid detection by traditional scanners.
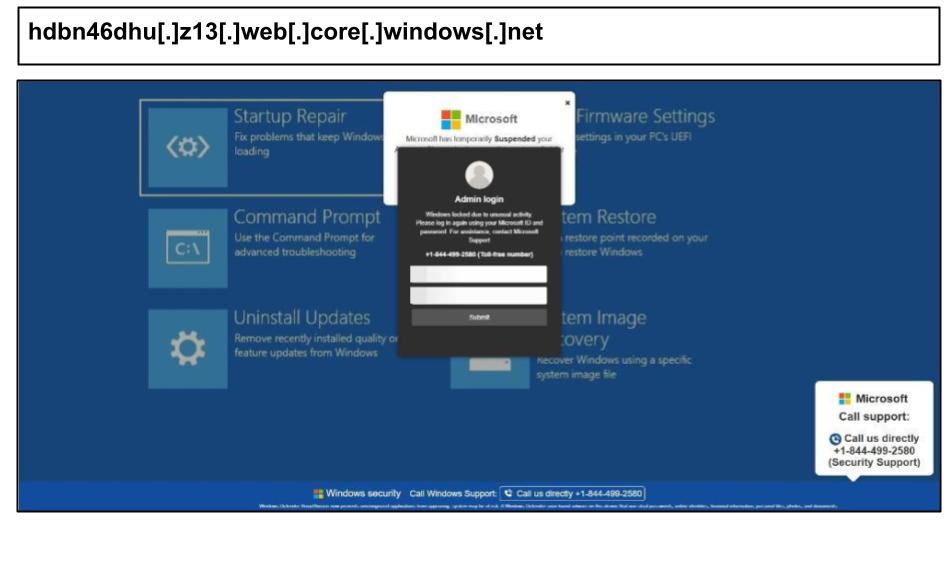
On August 18th, three administrators from the same organization clicked on a series of Microsoft support scams that were similar to others observed earlier in the month.
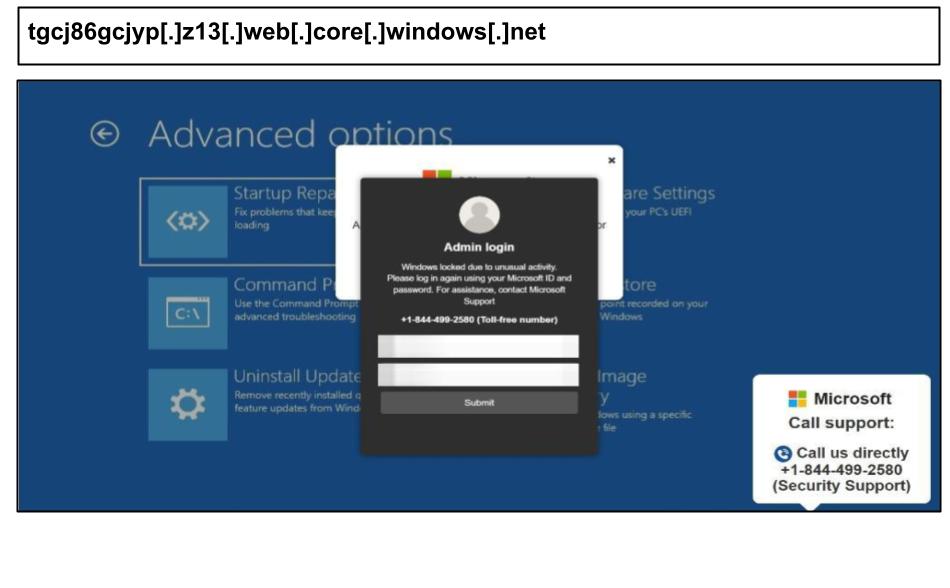
As in previous cases, these pages are tailored to the user's IP address and utilize URL parameters to change the phone number, directing different recipients to various call centers. The pages also disable the device keyboard, which leads many users to believe that calling the support number is their only option for leaving the page. Other similar attacks targeting the organization include:
hdbn46dhu[.]z13[.]web[.]core[.]windows[.]net
vtgg97gvy[.]z13[.]web[.]core[.]windows[.]net
On August 19th, an administrator at a Kentucky school reported a similar attack, noting that the phone number changed based on a different geography.
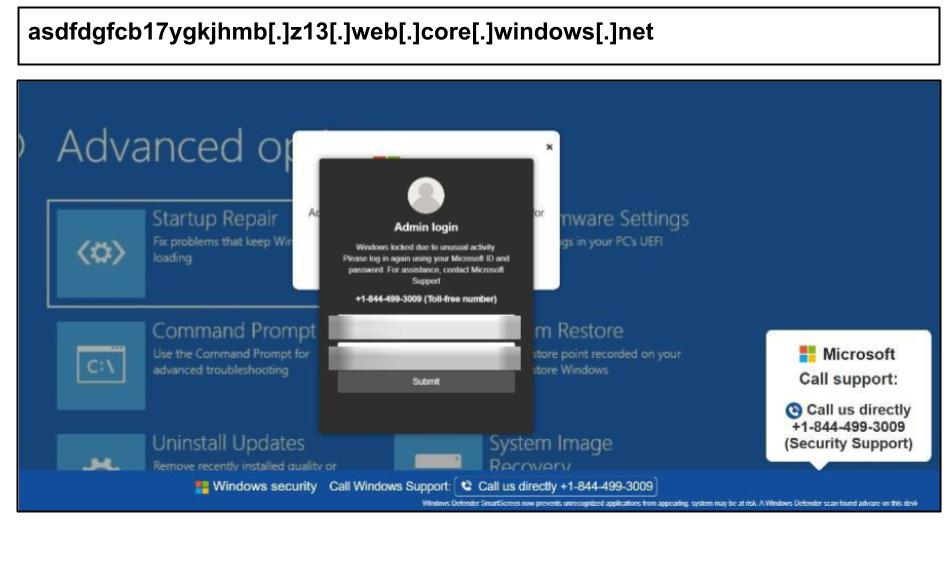
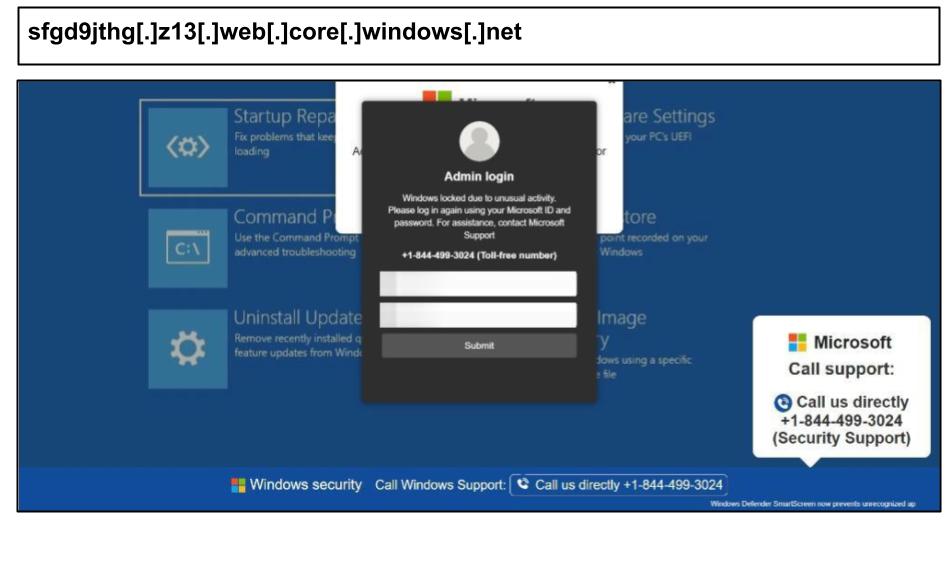
Other clusters were clicked across the country, such as the examples below, targeting administrators in Colorado and Georgia on August 18th.
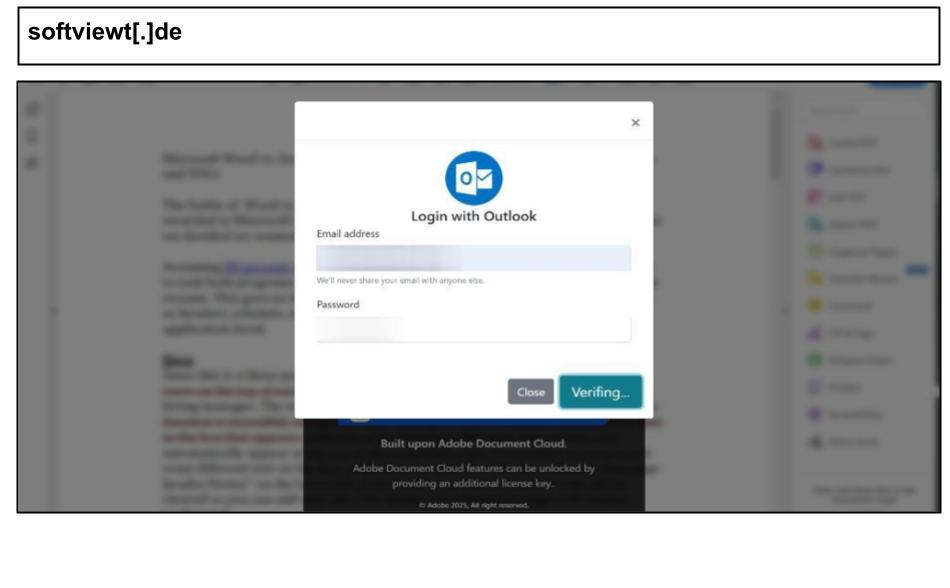
On August 17th, a California staff member clicked on the Adobe Cloud phishing attack below.
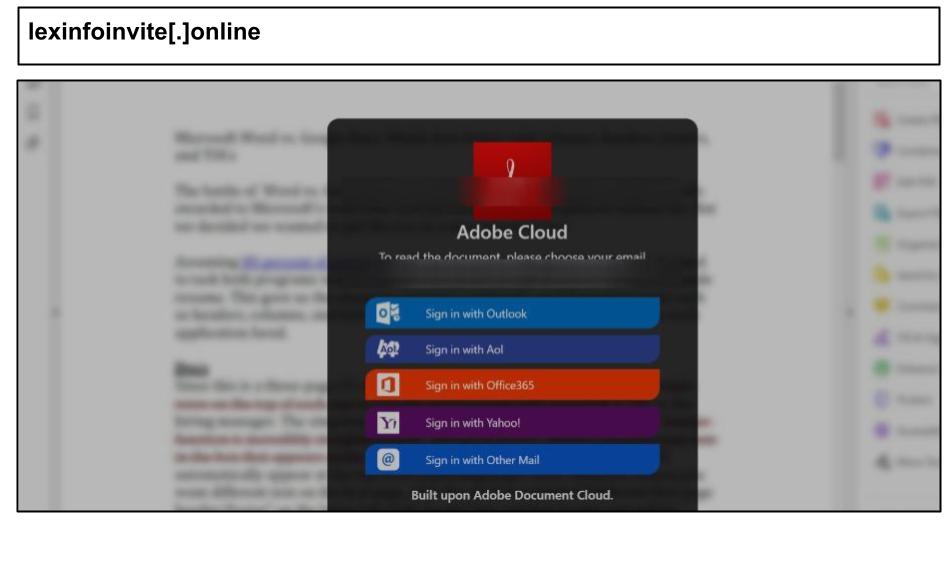
To evade mailbox inspection, the page utilized an Adobe file share and contained nearly 1 million characters to bypass various sandbox inspection tools. On August 18th, a staff member in Kentucky clicked on the following Microsoft spear phishing attack.
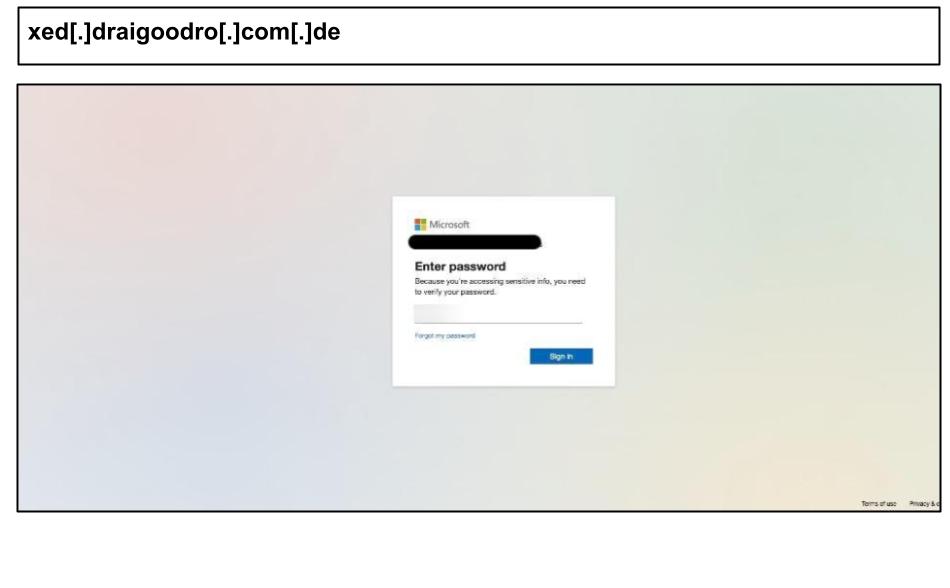
This page incorporates a packed JavaScript loader and an anti-analysis clipboard hook, both of which are commonly found in modern phishing kits. It also features a long, unique ID token for tracking each victim.
On August 18th, two administrators from a Kentucky organization clicked on phishing pages hosted on primesicilia[.]it[.]com.
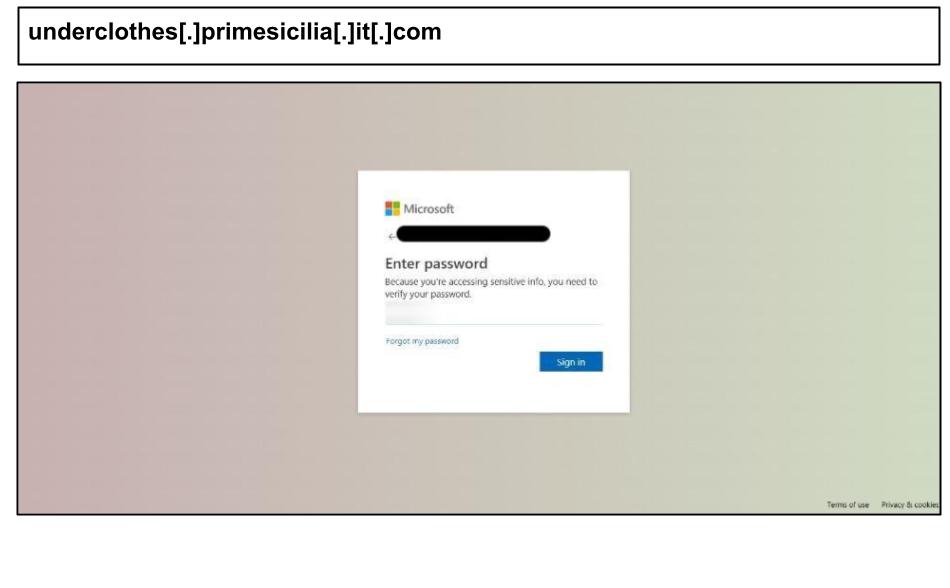
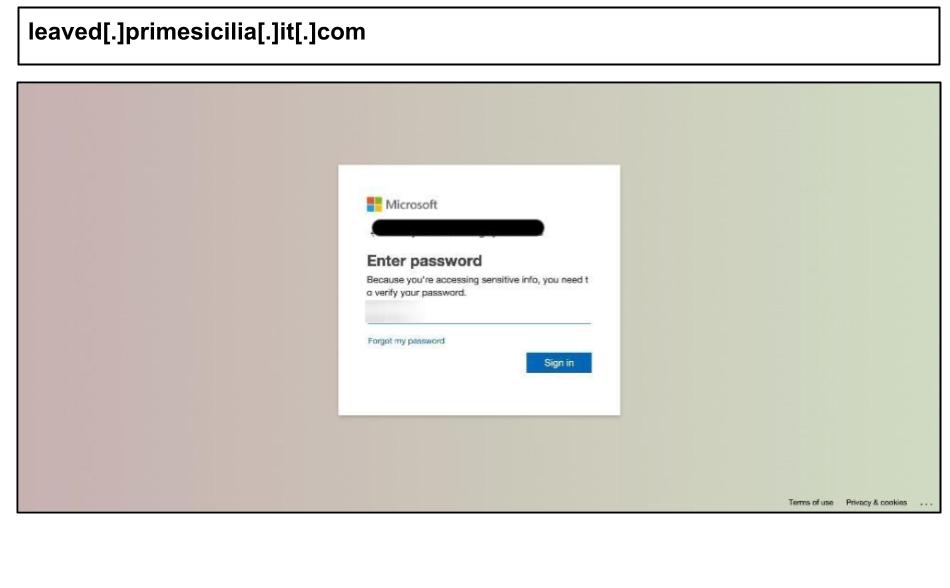
The pages prompt users for 6-digit (MFA codes, allowing for real-time relay or one-time password (OTP) capture. The text is obscured using invisible spans between letters, which makes it difficult for basic scanners to identify phrases like “Enter password” or “Sign in.” Additionally, most graphics are embedded as data URIs, resulting in minimal external requests and further complicating detection efforts.
On August 12th, a staff member at a Massachusetts organization clicked on a phishing site that impersonated Microsoft and Google.
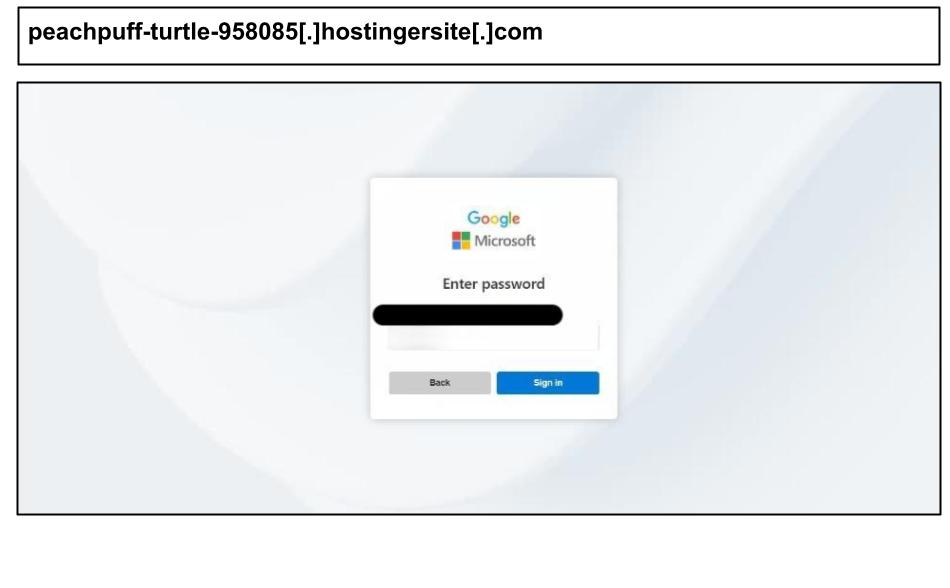
The website is hosted on a throwaway Hostinger subdomain (*.hostingersite.com). This cheap and disposable setup enables attackers to rapidly switch between domains, evading blocks and takedowns. The site also includes at least one image embedded as a base64 data URI directly in the HTML. This self-contained approach minimizes external requests, making it more challenging to detect.
On August 21, another staff member from Kentucky clicked on a Microsoft phishing link that utilized third-party infrastructure, this time from CloudFlare.
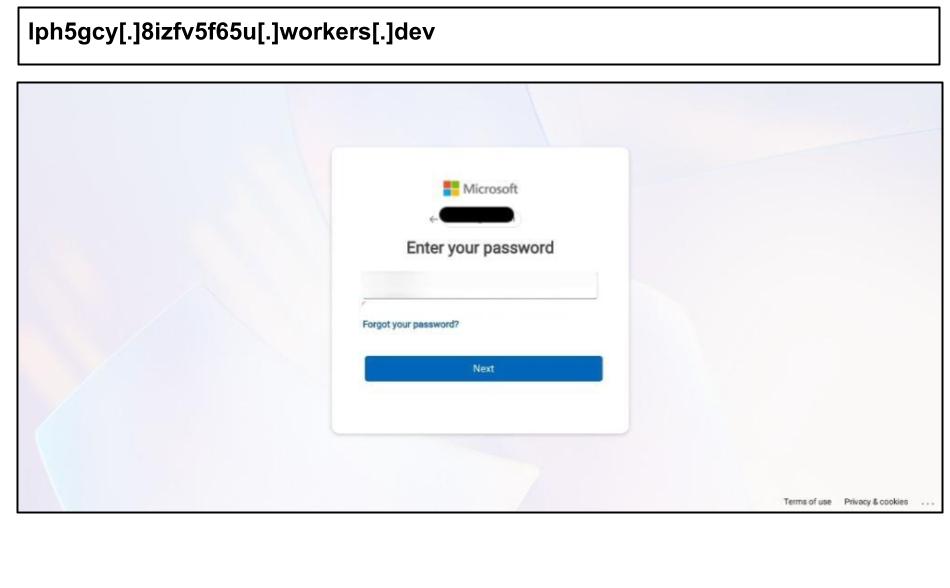
The site operates using Cloudflare Workers, a platform that allows users to quickly deploy a site under a *.workers.dev subdomain, complete with HTTPS, CDN edge delivery, and default Cloudflare IPs. Phishers prefer this option because it eliminates the need for their own hosting or certificates. Additionally, the site benefits from the reputation and performance of a major provider, allowing phishers to quickly rotate through disposable subdomains to evade age and blocklist checks.
During this same period, there was a continued effort to target corporate credentials through Paperless Post deliveries. These also utilized Cloudflare infrastructure, as demonstrated by the two pages that were clicked by staff members in Kentucky.
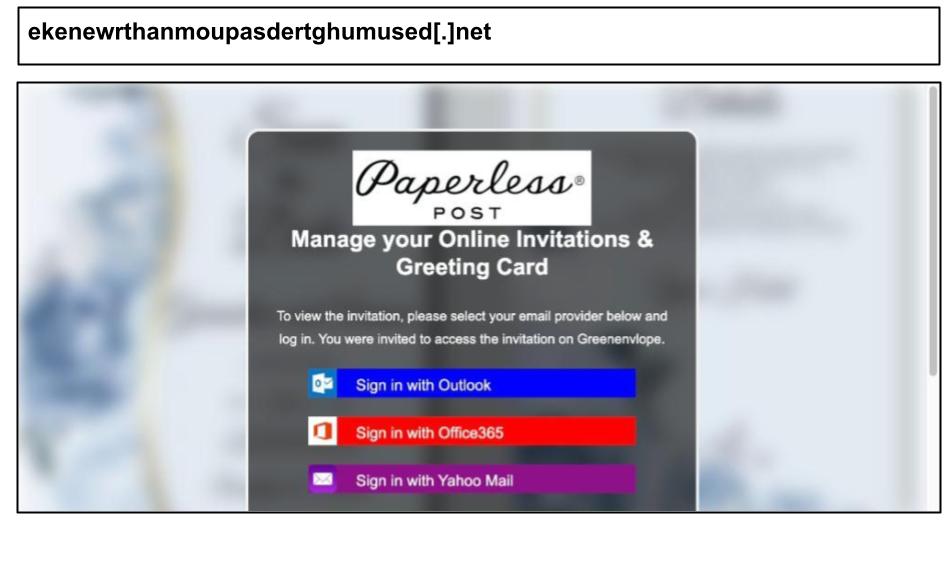
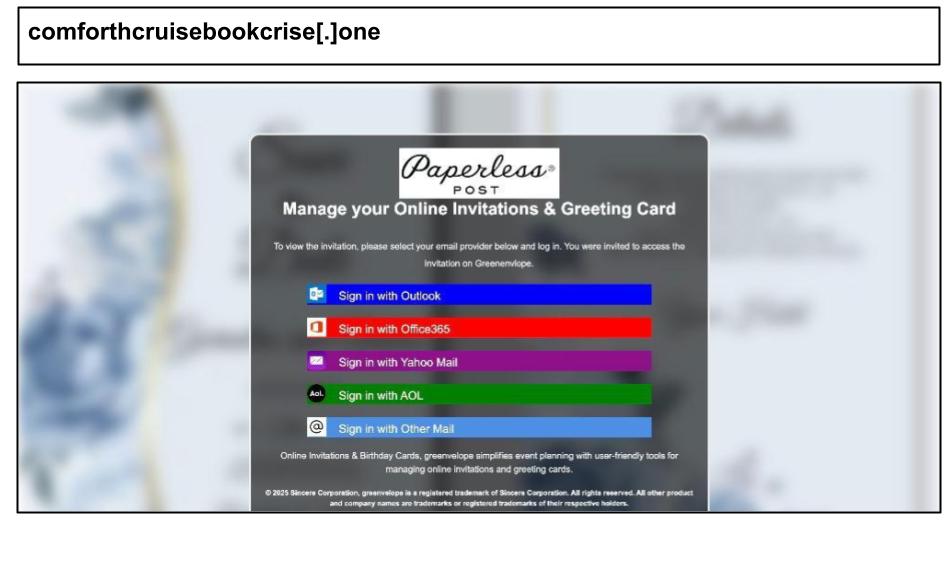
The attacks likely employed the same toolkit, which includes a multi-brand credential harvester. This harvester allows victims to "sign in" using services such as Outlook, Office 365, Yahoo, and AOL, while it tracks the chosen brand through a hidden identifier. The process follows a two-stage flow and prompts for a one-time password (OTP) to phishing for multi-factor authentication (MFA) codes. The first site also incorporates a Cloudflare challenge (challenge script//cdn-cgi/…), likely to mask the actual hosting and leverage Cloudflare’s reputation and TLS security.
E-Commerce Accounts Targeted on Work Devices
During the same timeframe, there was a continued focus on targeting personal accounts accessed from work devices, which again utilized Cloudflare infrastructure. For instance, on August 26th, a staff member at an Illinois organization clicked on a Yahoo phishing link while using their work device.
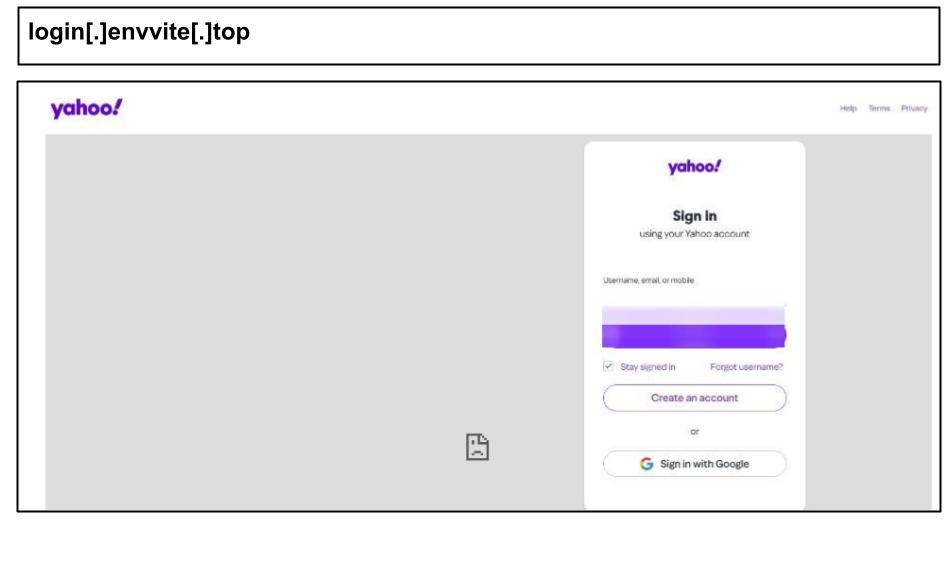
The HTML of the page clearly shows a redirect from a *.workers.dev URL, indicating that the target clicked on a CloudFlare Workers URL. This method leverages the reputation and performance of CloudFlare’s CDNs, similar to other attacks.
On August 27th, a staff member at an organization in Georgia clicked on a phishing attack disguised as an Amazon link while using their work device.
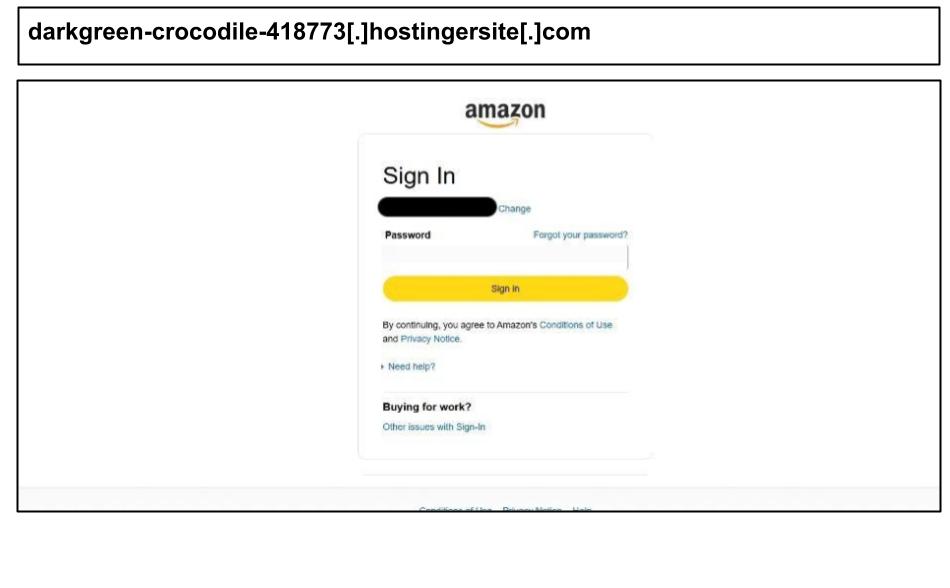
The link contains a unique encrypted code that allows the attackers to individually track each victim, making the scam more difficult for security tools to detect. Additionally, it employs hidden scripts to monitor user activity, and the domain seems to impersonate Hostinger, a well-known hosting service.
Mitigations
Block the specified domains on corporate firewalls and endpoint security solutions.
Educate users about the risks of phishing, even on websites that claim to use multi-factor authentication (MFA).
Remind users of the phishing risks associated with their personal accounts, regardless of whether they access them on corporate devices.
Enforce multi-factor authentication (MFA) for all corporate logins to help reduce the risk of credential compromise.

