- 27 May 2022
- 2 Minutes to read
- Print
- DarkLight
RapidIdentity Security
- Updated on 27 May 2022
- 2 Minutes to read
- Print
- DarkLight
This article covers security topics and information relative to RapidIdentity.
Passwords
Accessing Password Changes from Active Directory
RapidIdentity uses a Microsoft API to capture password pages before they are encrypted by the domain controller. For this functionality to work, a custom password filter DLL is "hooked" into the system running Local Security Authority Subsystem Service (LSASS), the service through which password changes are processed. This is the same method used by Google Apps Password Sync (GAPS) password filter and other available password synchronization solutions.
Password changes are protected with 2048-bit RSA Encryption. When password changes are detected by the RapidIdentity password filter, they are encrypted using the RSA algorithm and stored in the idauto-pwdPrivate attribute on the individual user object.The public key (2048-bit) for this encryption resides on a Domain Controller, allowing RapidIdentity Connect to decrypt the idauto-pwdPrivate attribute value for synchronizing to target systems with the private key stored in the RapidIdentity database.
Storing Challenge Questions
Challenge questions and responses are stored as values of the idautoChallengeSet attribute on the user. The question types (ADMIN, HELPDESK, USER-DEFINED) and questions are in plaintext. The answers are encrypted using AES 256-bit encryption.
Storing Properties Flagged as "PASSWORD" Type in RapidIdentity Connect
Within RapidIdentity Connect Action Sets, certain actions allow for a property to be set as a password field. This property can be selected like most any other field. When the Password type is chosen, the data is obfuscated from view.
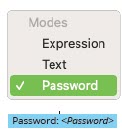
If an administrator needs to utilize a password for an Action Set, the best practice is to configure the password setting to refer to a global variable that is input (with the encrypt() syntax) in a global properties file rather than setting the password directly in the action itself. Passwords stored in global properties files are protected with 256-bit AES encryption.
Enforce Password Policies' Password Strength, Blacklisting, Expiration, and Re-use
In general, policy complexity can be configured within the Portal configuration. Further enforcement capabilities can be configured by setting blacklisted passwords (by text, regular expression matching, or matching specific attributes such as sn, givenName, company, etc.). In addition to custom blacklisting capabilities for restricting passwords, RapidIdentity provides automatic Password screening for compromised passwords. This service is provided by Have I Been Pwned and licensed under a Creative Commons Attribution 4.0 International license. Configuration for Password Policy syntax, restrictions, and screening is done through Configuration > Policies > Password Policy Manager. With regard to password expiration and re-use, those are managed by the underlying LDAP directory and any password policies therein.
RapidIdentity allows Administrators to create and manage multiple Password Policies through Password Policy Manager.
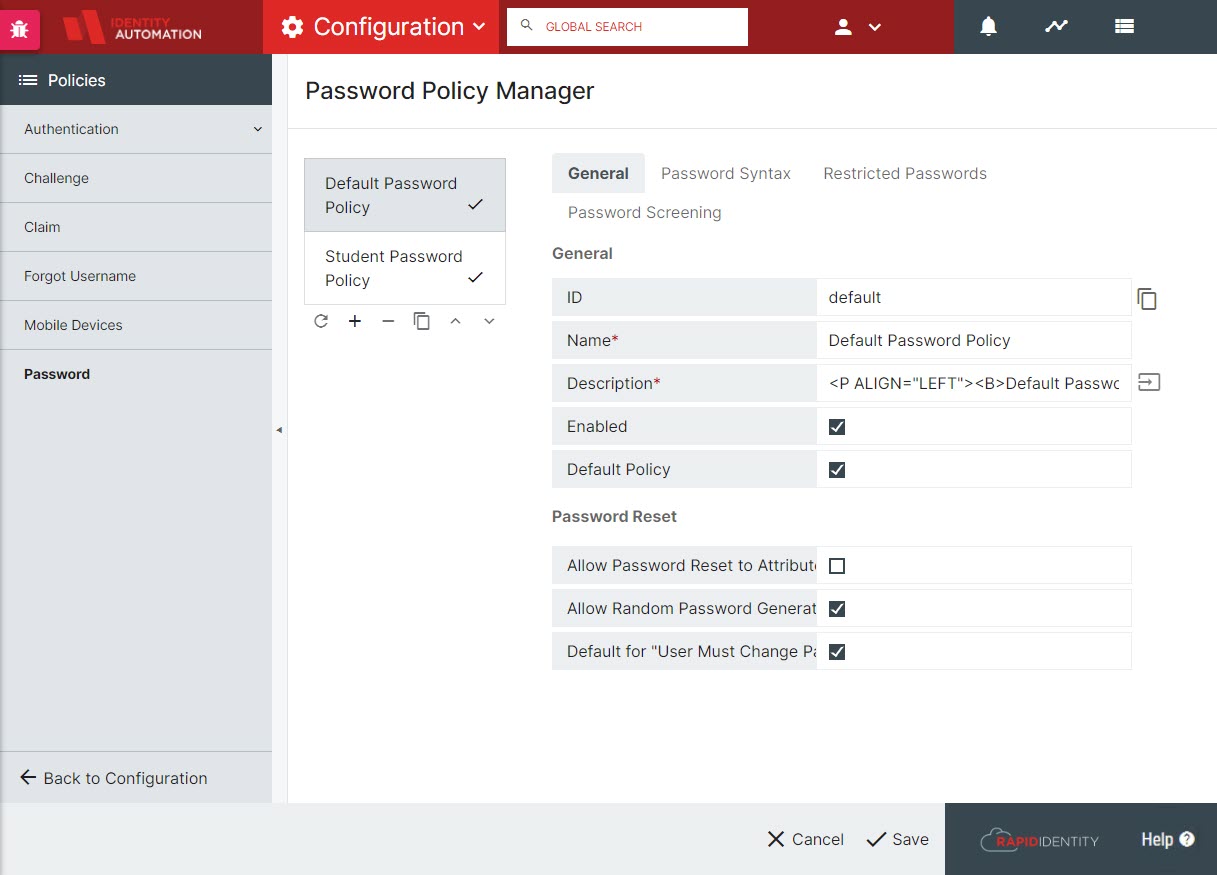
RapidIdentity allows Tenant Administrators to customize complexity requirements and restricted passwords.
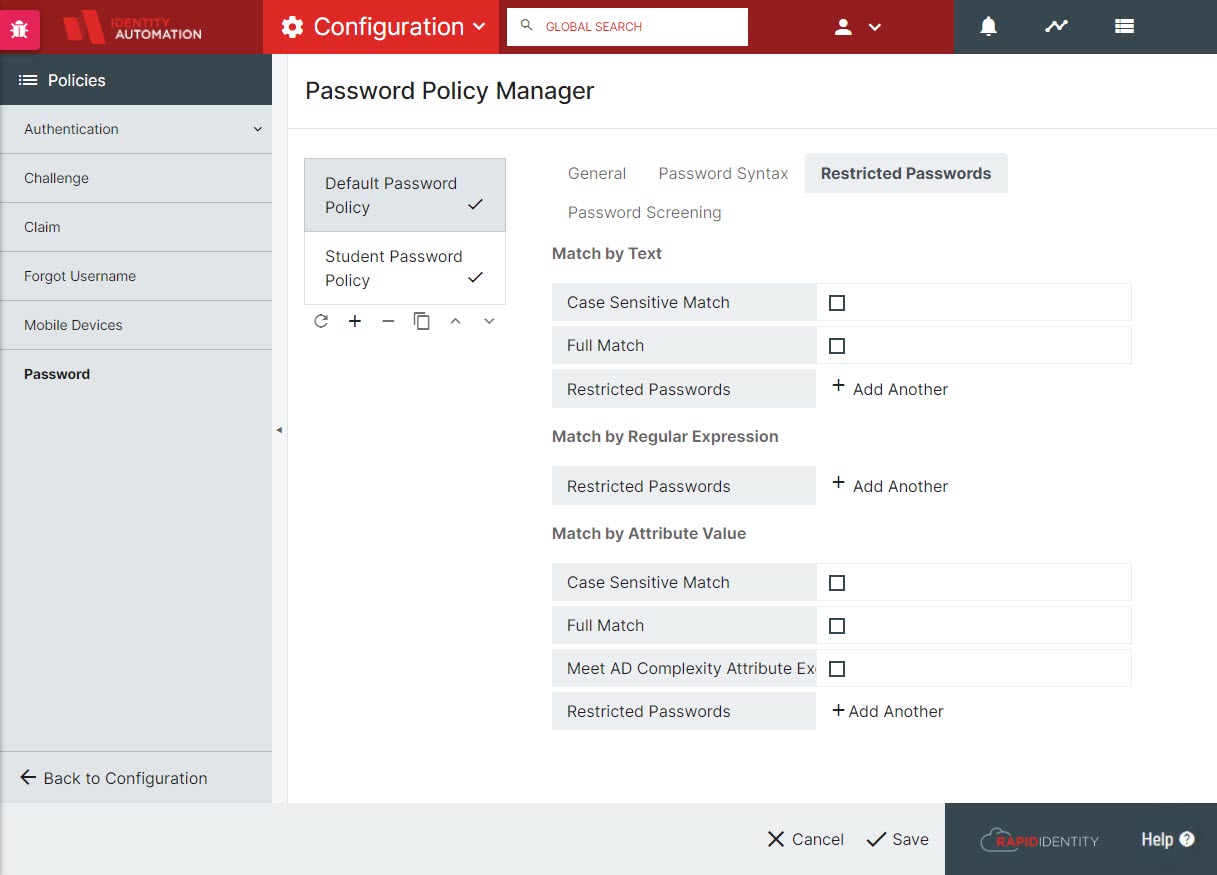
RapidIdentity provides Tenant Administrators the ability to enable Embedded Password Screening and custom messaging for Complexity requirements.