- 19 Jul 2023
- 8 Minutes to read
- Print
- DarkLight
Release 2023.07.0 - What's New
- Updated on 19 Jul 2023
- 8 Minutes to read
- Print
- DarkLight
Release 2023.07.0 - What's New
RapidIdentity 2023.07.0 new features, enhancements and notable issue resolutions.
Notable Enhancements and New Features
Ability to Configure the Timezone in Connect Jobs
The ability to set a Timezone when scheduling a Connect Job has been added in Connect > Jobs > Details > Schedule
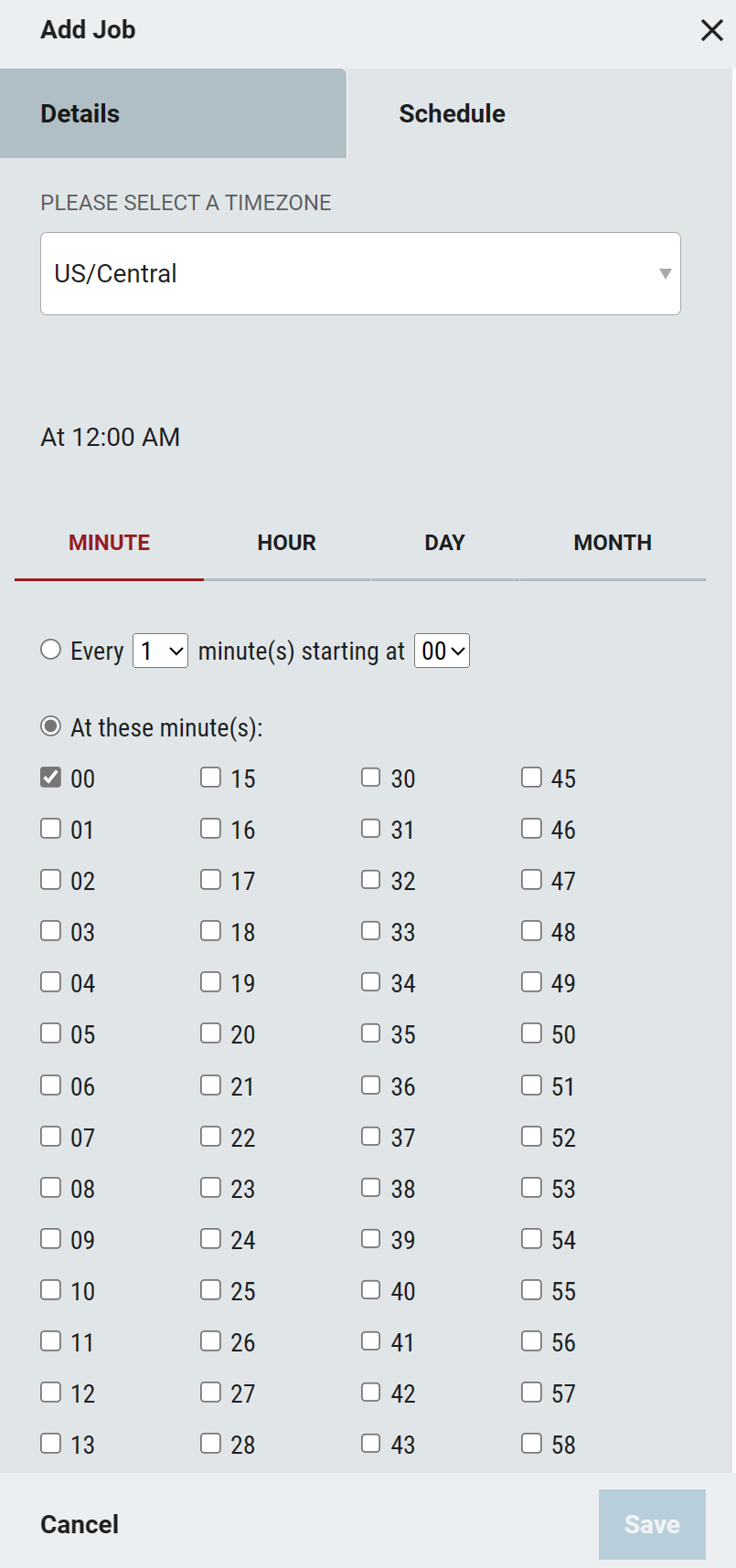
If not specified, the Etc/GMT timezone will be used
Directory Schema Updates
A series of attributes have been added to extend the options available around User based fields. For a complete list of attributes, please refer to this article.
New additions to the Directory Schema are designated with a note stating: Introduced in amazon-ricloud-2023-07-01
Improved Support for External Authentication Realms
To reduce onboarding friction, Active Directory can be used as an External Authentication Realm in RapidIdentity. This will allow users to authenticate with RapidIdentity using their current password, which can be synced with Active Directory. The User Experience when utilizing an External Authentication Realm with Active Directory is explained below.
When using an external authentication realm, RapidIdentity should comply with the external authentication realm’s requirement for the user to reset their password AND RapidIdentity should also comply with the internal realm’s requirement for the user to reset the password. If neither the internal realm or external realm requires the user to reset their password, RapidIdentity should not prompt the user to reset their password. If either the internal realm or external realm requires the user to reset their password, RapidIdentity should prompt the user to reset their password.
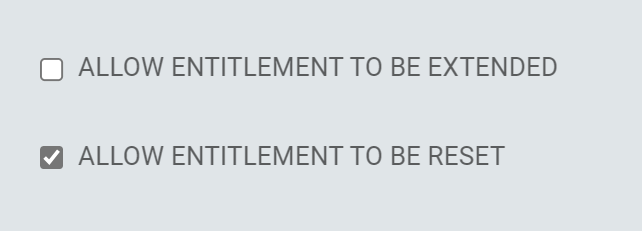
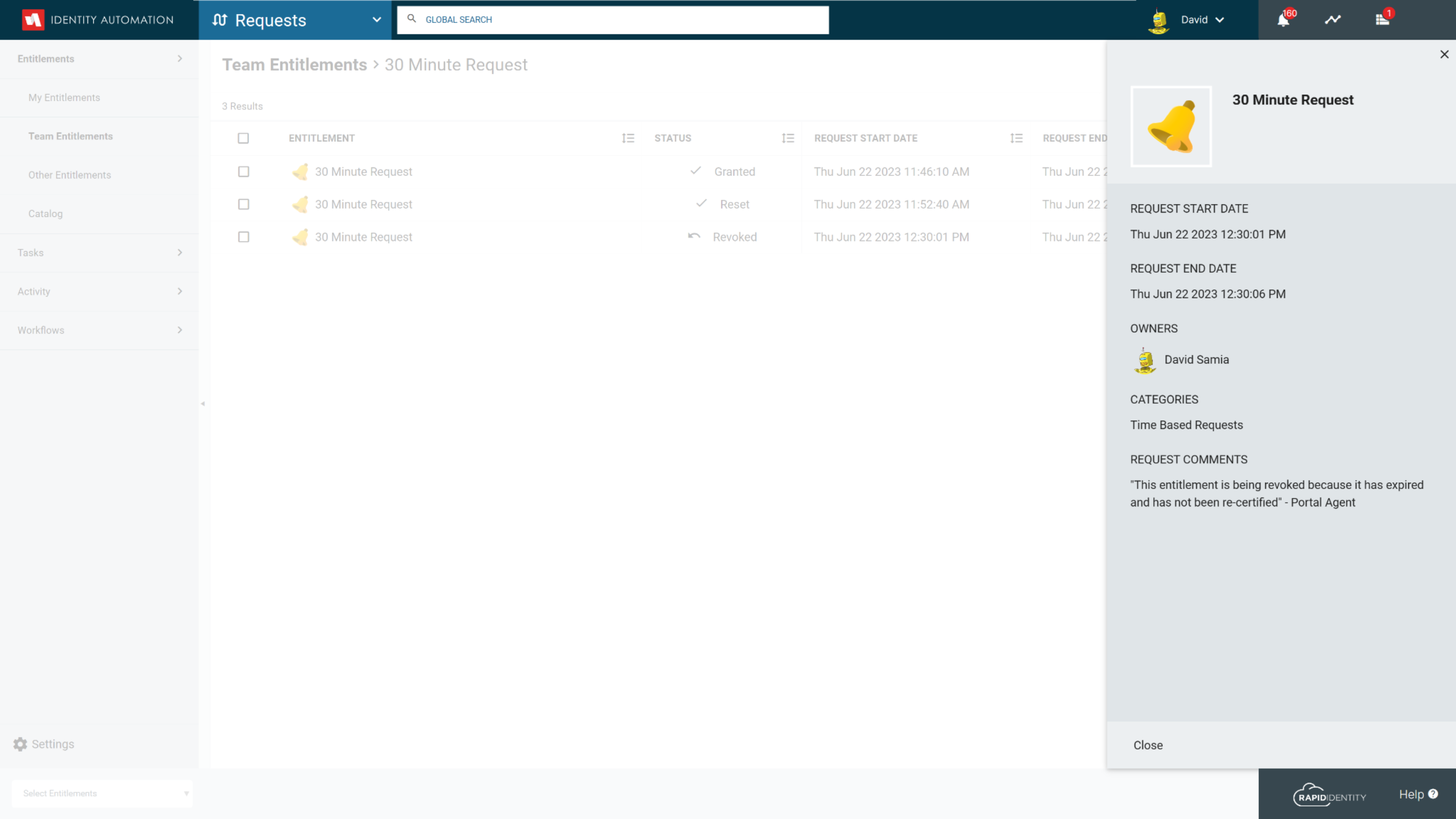
New Entitlement Option to Extend or Restart the Time
A new Allow Entitlement to be Reset option has been added to the Entitlement Configuration in Requests for Time-based entitlements.
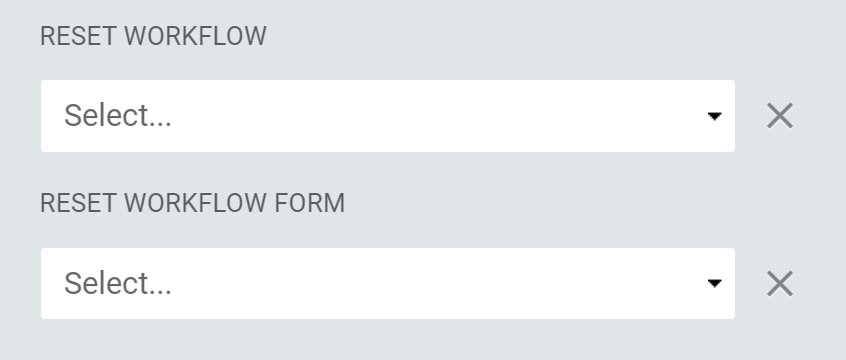
When an Entitlement Expiration Type is set to Time-based the option to Allow Entitlement to be Reset becomes visible and, if checked, an appropriate Reset Workflow and Reset Workflow Form can be selected.
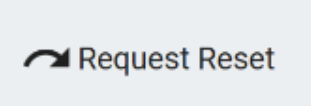
To Request an Entitlement Reset, select the entitlement and click the Request Reset button from the bottom Action Menu.
Reset requests, grants, denials and expirations are included in the history of the user's Entitlement.
New ISAPI Filter for SSO with Internal Applications
To enable MFA and SSO with RapidIdentity Cloud and internal IIS web applications, a new RapidIdentity ISAPI filter can be installed in the web application's IIS server to authenticate users with RapidIdentity before accessing the application.
With the RapidIdentity ISAPI filter installed in the application's IIS web server, users attempting to access the application will be required to authenticate with RapidIdentity if they do not already have an authenticated browser session with RapidIdentity. When the user has an authenticated browser session with RapidIdentity, they will be passed directly into the application.
Use the following instructions to install the RapidIdentity ISAPI Filter and configure RapidIdentity Cloud to use the ISAPI Filter:
Install the RapidIdentity ISAPI Filter
Instructions for installing the ISAPI Filter are here
Configure RapidIdentity Cloud for the ISAPI Filter
A new configuration section called Authentication has been added under General > Settings for administrators to configure the Service Identity and Key that has been created for the ISAPI Filter.
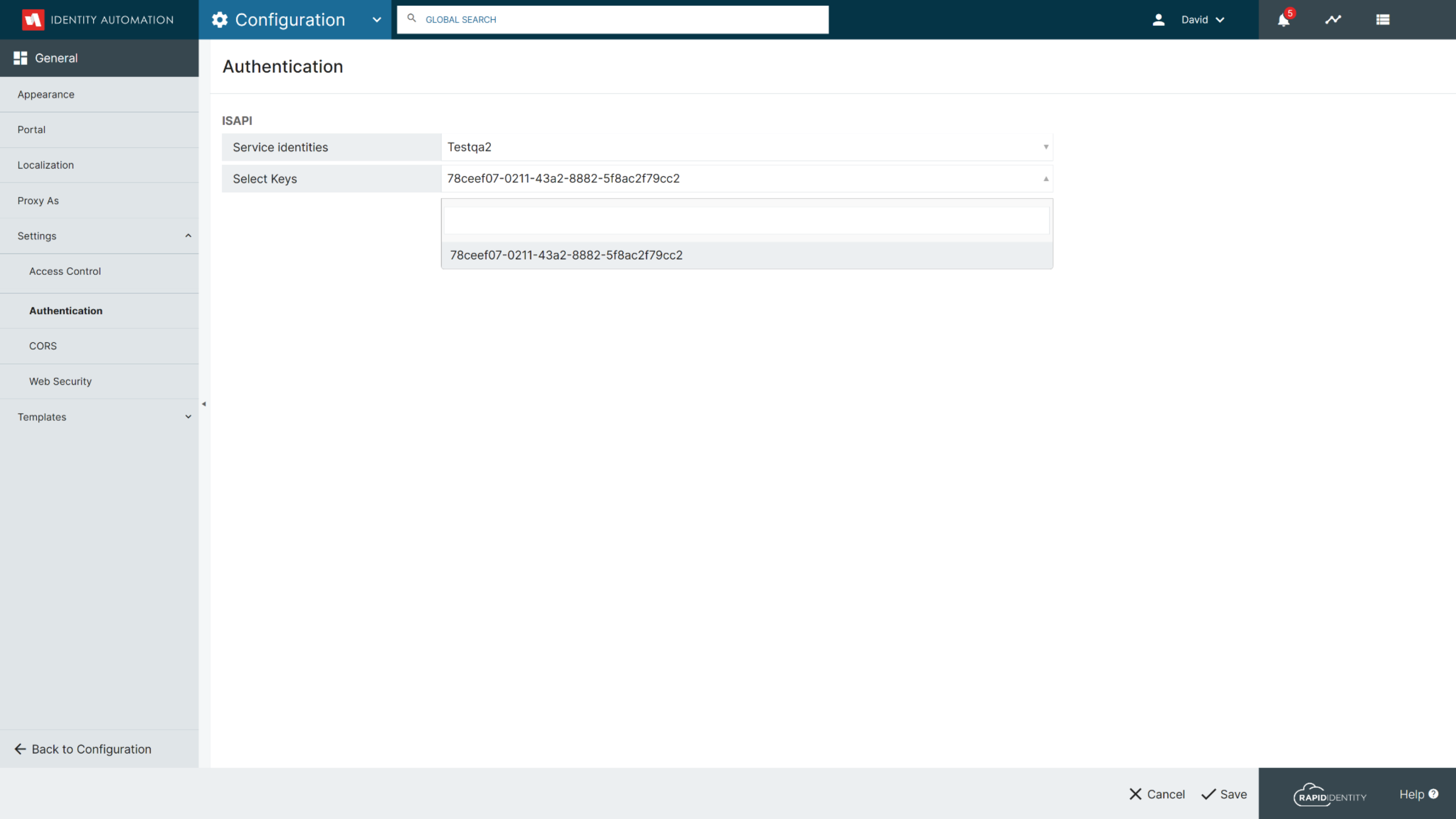
A Service Identity and Key must have already been created in RapidIdentity prior to configuring them for the ISAPI Filter.
For instructions on creating a Service Identity and Key click here
Password Policy Enhancements
In a continuation of the Password Policy Enhancements made recently, the User Experience of this module has also been refreshed. With this release, administrators will enjoy an updated interface that includes expanded details regarding the new Password Policy Features now available in RapidIdentity.
Let's take a look at those new options in more detail:
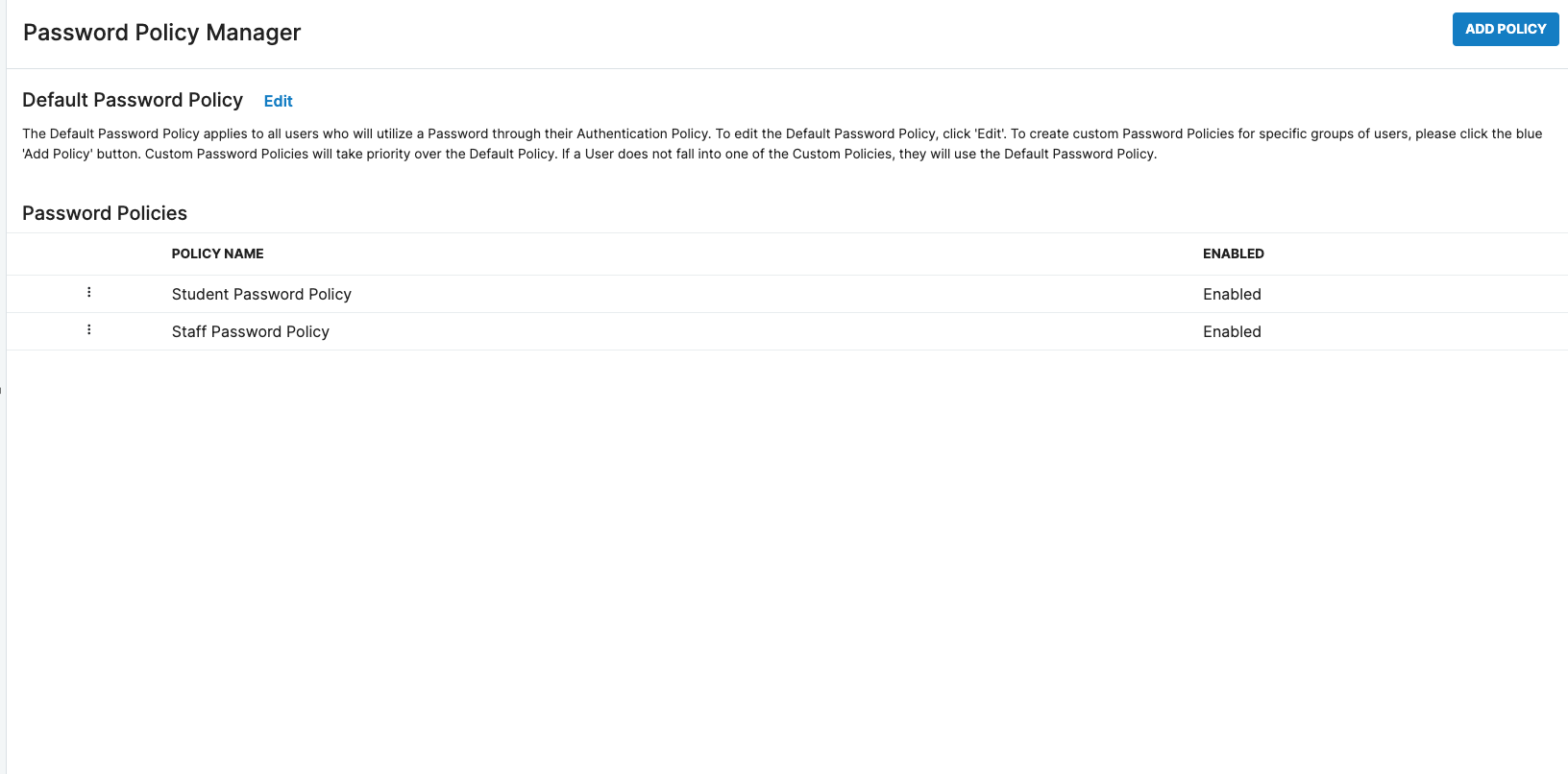
Password Policy Manager
The Password Policy Manager Screen has been redesigned for an enhanced User Experience. The Default Password Policy is listed at the top of the screen, and can be modified using the Edit link.Custom Password Policies are listed in order by priority. New customized policies can be added using the Add Policy button, and they can also be reordered in the list to meet your User's needs.
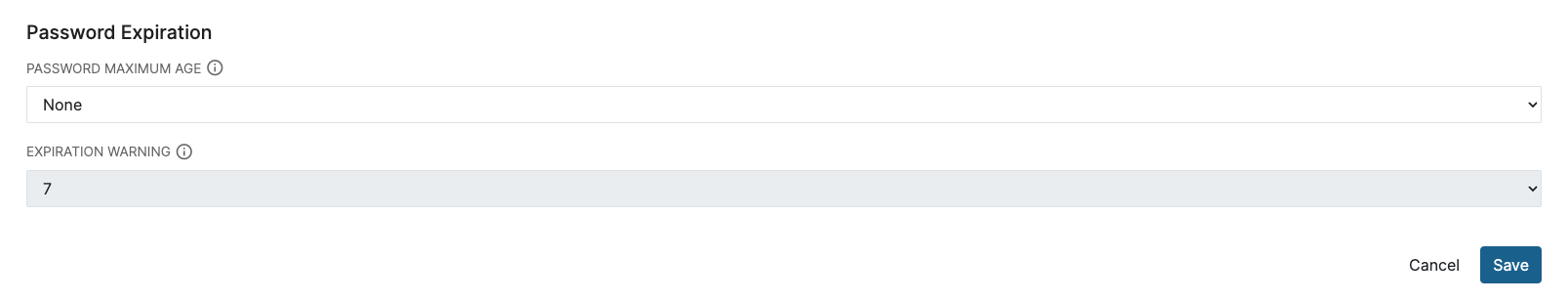
Password Expiration Policy
For a Password Policy, Administrators are now able to determine aPassword Maximum Ageand set a timeline for 'Expiration Warnings'.The
Password Maximum Ageis configured in days, and determines the maximum length of time a User is able to keep the same password. After that amount of time elapses, the User will be required to reset their password.Administrators also are able to set an
Expiration Warning, which determines how many days in advance of a password expiration the User will be notified that they will need to reset their password soon.
 Note:
Note:Existing policies will have Password Expiration automatically set to
Nonewhen RapidIdentity is upgraded with the 2023.07.0 release and administrators can update them as appropriate.Password Reuse Policy
Administrators are now able to determine if a Password History is kept for Users in a specific policy, and set the number of passwords that will be remembered in that history. When configured, users will be unable to reuse a password that currently exists in their Password History.If 'No Restriction' is selected in the 'Passwords Remembered', users in that policy will not be restricted from reusing passwords.
 Note:
Note:Existing policies will have Restrict Password Reuse automatically set to
No Restrictionwhen RapidIdentity is upgraded with the 2023.07.0 release and administrators can update them as appropriate.Enhanced Support for Utilizing Regular Expressions
Regular Expressions, or Regex, is a sequence of symbols or characters expressing a string or pattern to be searched for within a longer piece of text. Within a Password Policy, an Admin can provide a Regex to add restrictions on what words or series of characters can be used within a password.By adding examples of Regular Expressions and how they affect Restricted Passwords, Administrators are enabled to utilize this feature when customizing their Password Policies.
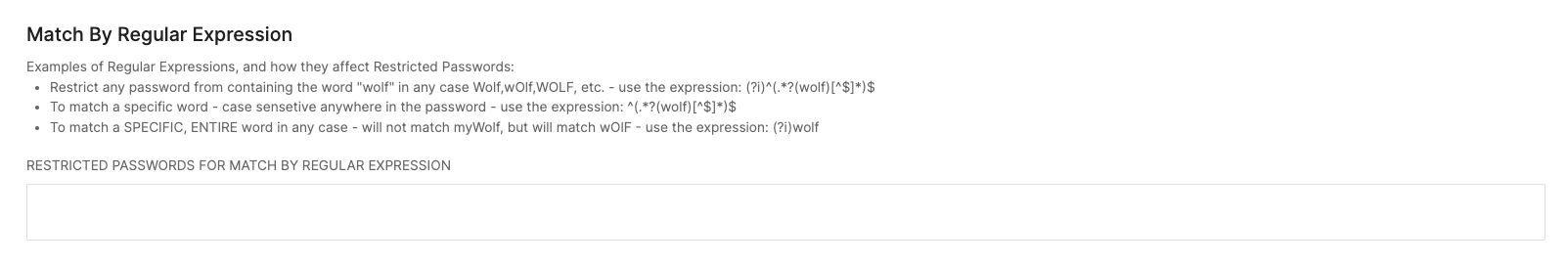
As with any settings that will affect the security of accounts and the User Experience, we recommend referring to the NIST Digital Identity Guidelines.
It is also important to reflect upon the technical capacity of the individuals who are affected by the policy to ensure a positive experience.
People Module Navigation Enhancements
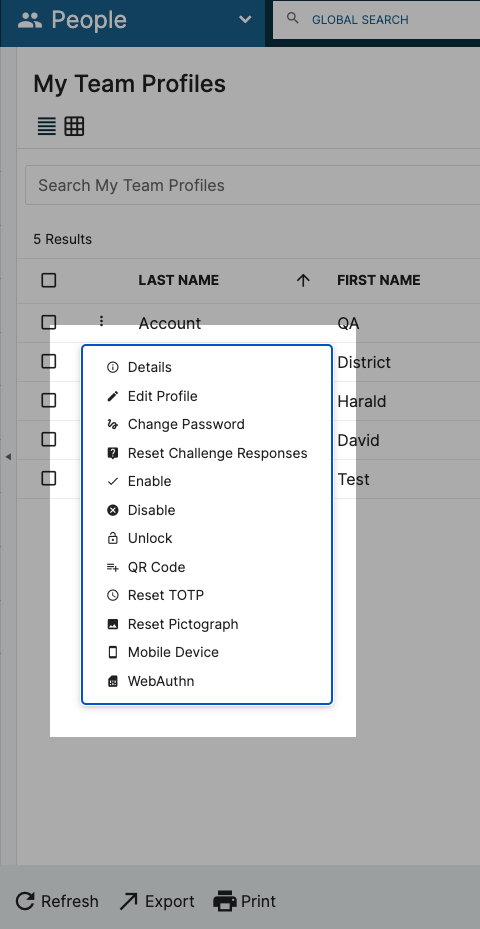
Another Module that has undergone a redesign to improve the User Experience is the People Module. Previously, the Action Options appeared in the bottom Navigation bar. Now, you will be able to access these options from a dropdown menu accessible via a right-click or the kabob icon.
The options have also been streamlined, while maintaining functionality, resulting in a short list to manage. There are three specific Action Item changes to keep in mind:
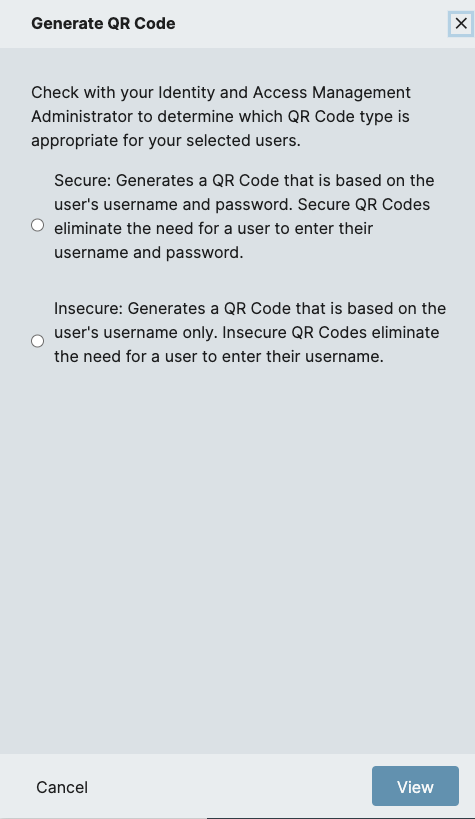
QR Code: Secure and Insecure QR Codes can be generated from this consolidated option.
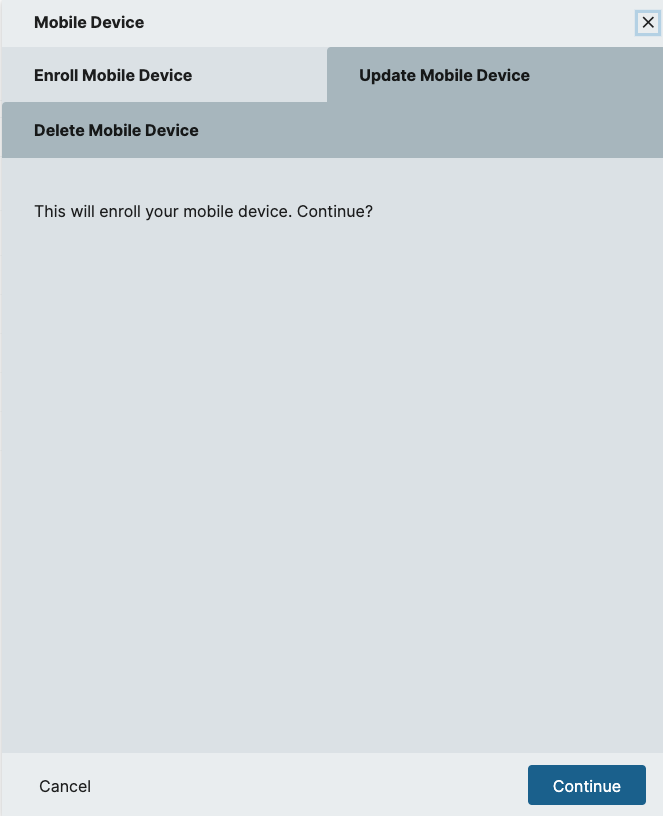
Mobile Device: This sidebar menu contains the ability to Enroll, Update, and Delete a mobile device.
WebAuthn: The options to Add/Manage and Delete a WebAuthn device are all available in this sidebar menu.
PKCE Support added in OAuth/OIDC Authorization Flow
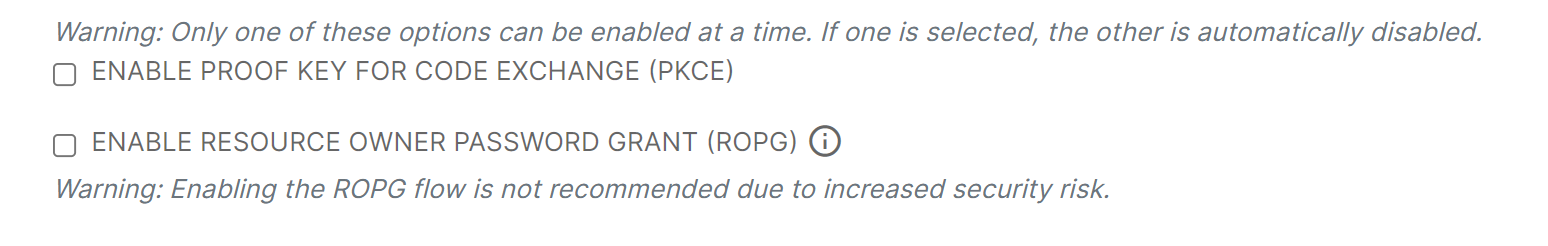
PKCE, "pixy", is an abbreviation for Proof Key for Code Exchange, an extension to the OIDC Authorization flow that enables applications to authenticate users without them needing to have a client secret.
The Authorization Code Flow + PKCE is an OpenId Connect flow specifically designed to authenticate native or mobile application users.
While PKCE was originally designed to protect the authorization code flow in mobile apps, its ability to prevent authorization code injection makes it useful for every type of OAuth client, even web apps that use client authentication.
PKCE is an optional setting on an OIDC Federation Partner configuration that can be enabled by checking the Enable Proof Key for Code Exchange (PKCE) checkbox in the OpenID Connect Configuration section of the Federation Partner configuration page.
To create or update an OIDC Federation Partner navigate to Configuration > Security > Identity Providers > Federation Partners and click Add Federation Partner to create one new or click the ellipses next to an existing one and select Edit to update it
Search Entitlements Catalog
A search bar has been added to the Entitlements Catalog page for users to more easily find the entitlements they're looking for.
To search, enter any part of the Entitlement Name and press Enter or click the search icon.
Search is performed against any part of the Entitlement Name
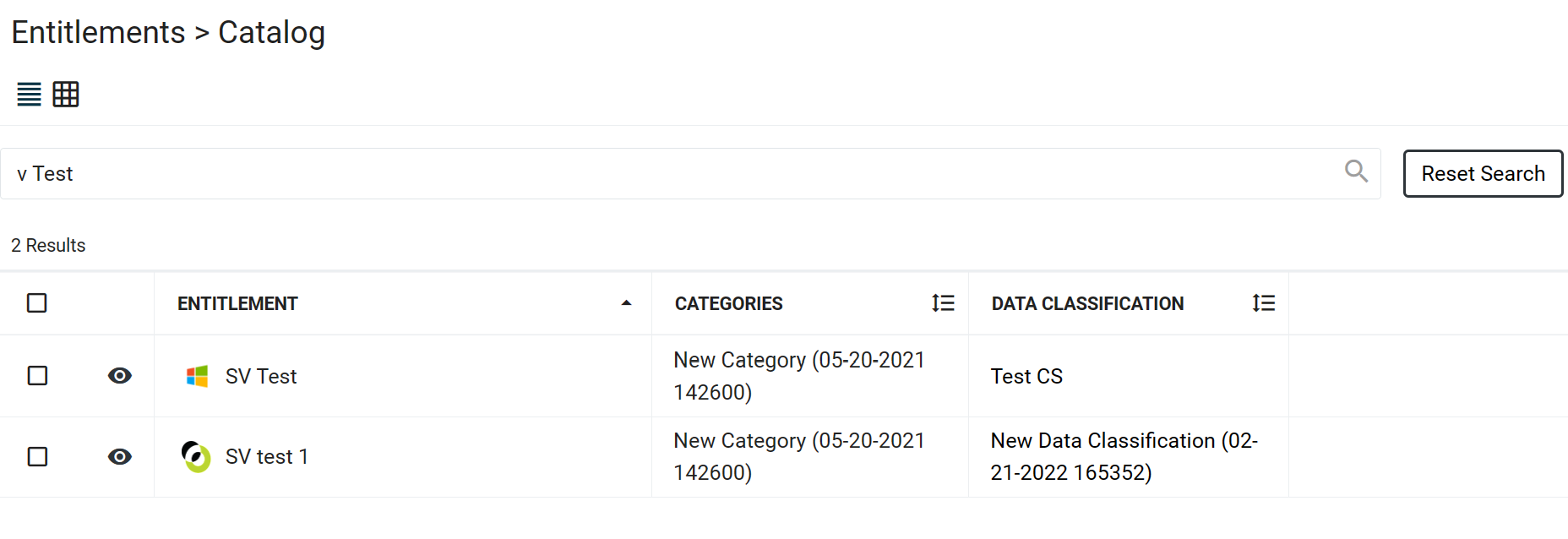
Click the Reset Search button to re-display the full list of entitlements.
ShieldID User Interface Updates
The ShieldID Rules Overview page has been updated to show a description for each rule
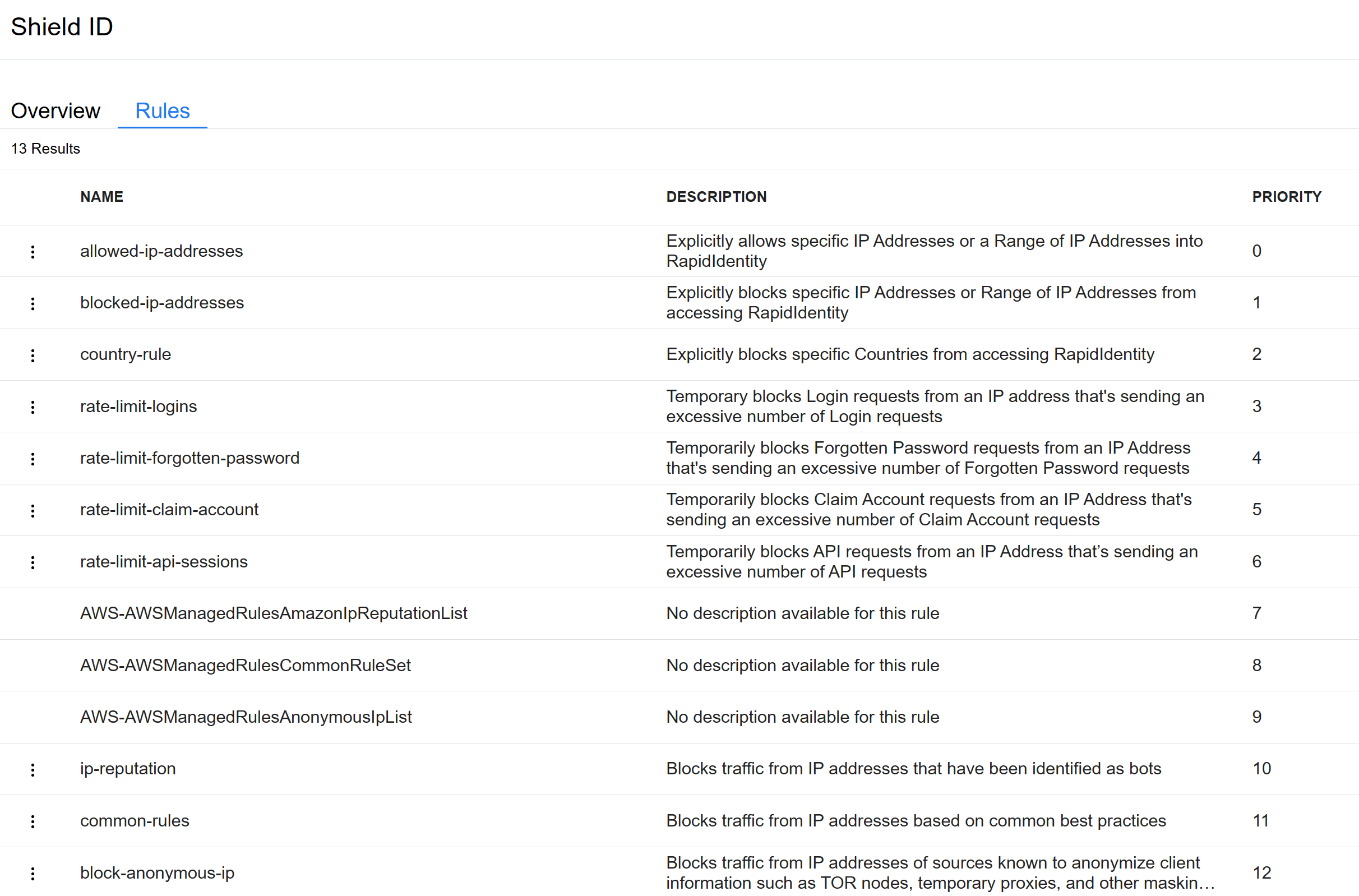
The block-unlisted-countries rule name has been changed to country-rule and a new Rule Condition setting has been added to either
block the countriesorallow the countriesthat are listed.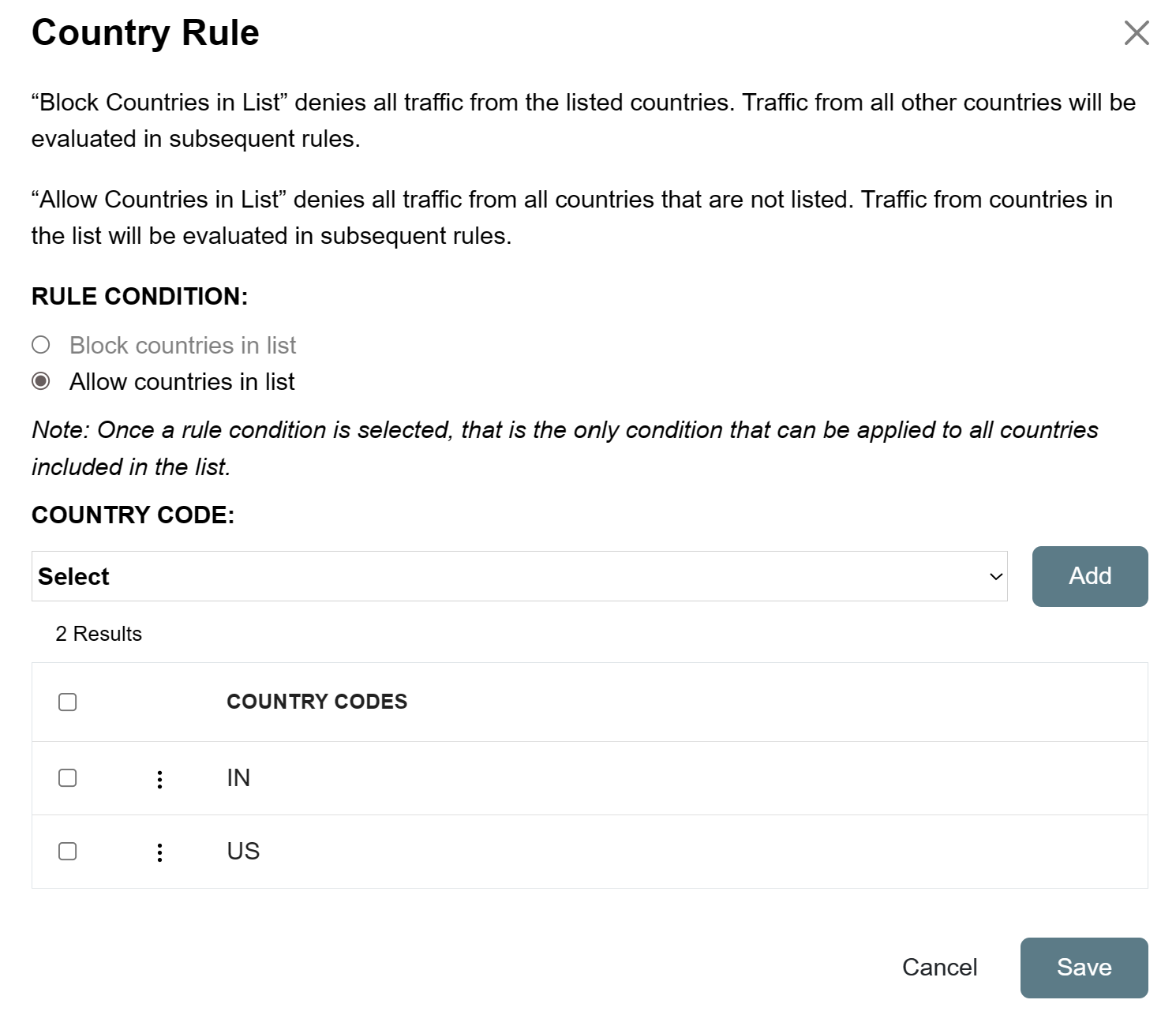
ShieldID is an optional, fee-based service that provides advanced firewall capabilities for RapidIdentity Cloud customers. To purchase ShieldID talk with your Customer Success representative or, click here to contact Identity Automation sales.
Studio OAuth 2.0 REST Target Timeout
A new configuration setting, ACCESS TOKEN TIMEOUT has been added in Studio for OAuth 2.0 REST target applications.
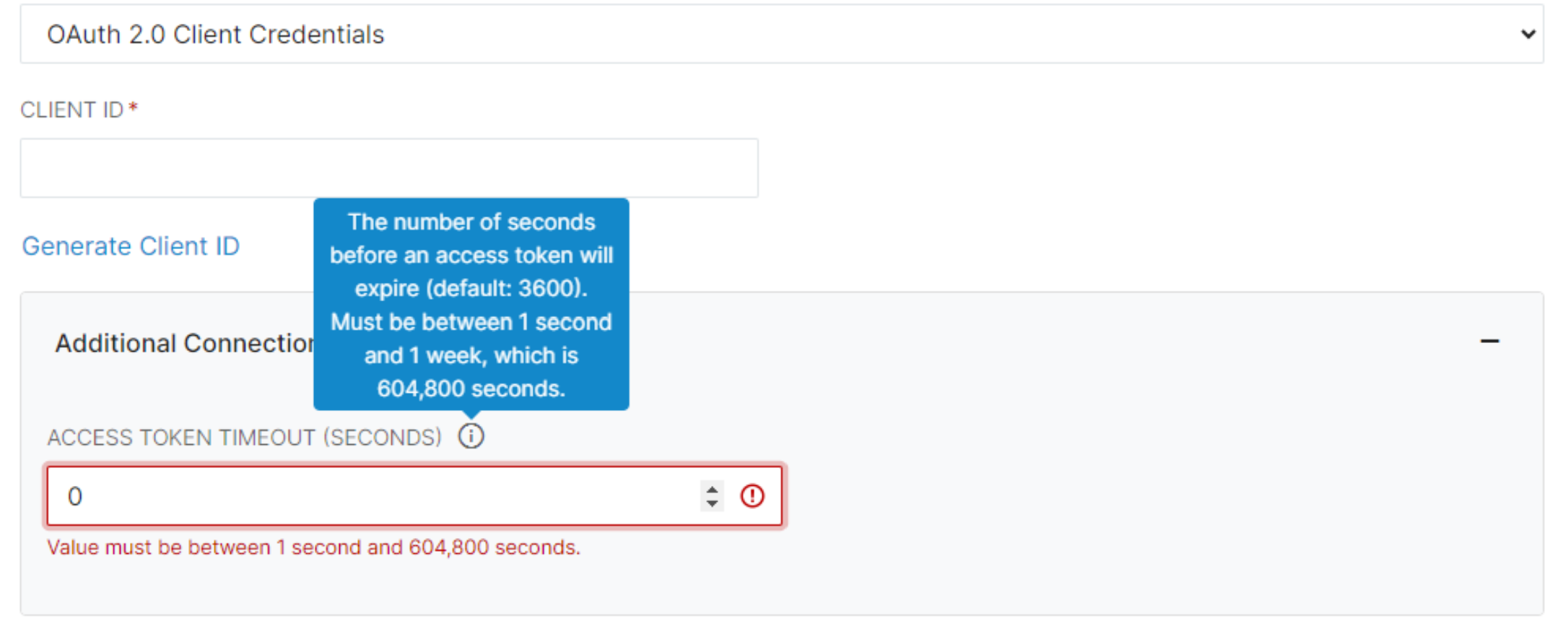
This new configurable setting can be used to extend the default one hour timeout on OneRoster REST API connections using OAuth 2.0 client credentials to accommodate extremely large amounts of rostered information.
WebAuthn Support for Biometric Authentication Devices
The default WebAuthn UserVerificationRequirement setting in RapidIdentity has been changed from discouraged to preferred to ensure that WebAuthn devices that are capable of authenticating the user, biometric devices for example, perform that verification.
Existing Authentication Policies using the WebAuthn Authentication Method will not be affected by this change if there are registered WebAuthn devices. In that case, the current discouraged setting will be persisted unless configured otherwise.
For more information regarding UserVerificationRequirement click here
New WebAuth Configuration Settings
A new WebAuthn configuration section has been added under Configuration > Policies > Authentication to enable Tenant Administrators to control the UserVerificationRequirement and EnrollmentVerification settings.
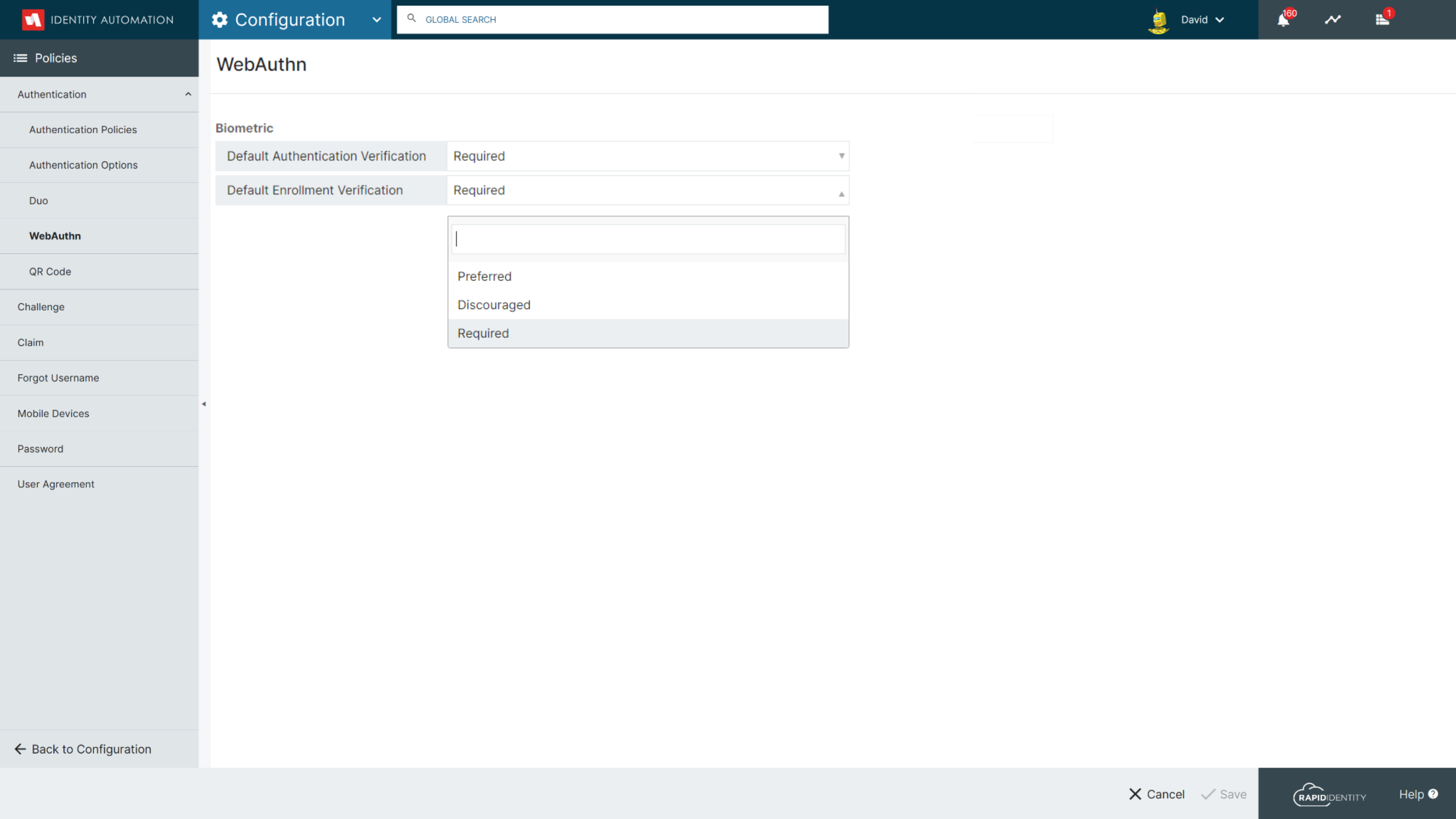
Verification Options
- Required - Only devices capable of user verification will be supported
- Preferred - Instructs the device to verify the user if capable but verification is not required
- Discouraged - Considers the presence of the device to be sufficient
Significant Issues Resolved
- Inability for Membership Managers to update Static Includes has been resolved
- Fixed non-working Export and Print buttons in Grid View for Other Sponsored Accounts
- Connect adminPasswordReset() Action now returns a proper error condition when Password Validation fails

