Setting Up RapidIdentity with Central Authentication Service (CAS)
The Central Authentication Service (CAS) is a single sign-on protocol service that allows potentially untrusted websites to authenticate users against a central, trusted authentication service without ever exposing the user's credentials to the website. A CAS Client is called a Service, and in the RapidIdentity CAS implementation, every Service that needs to interact with the server must be registered.
Registering a CAS Service means giving it a unique name and optionally providing protocol-specific configuration including ticket lifetimes, URL matching rules, a proxy policy, and defining which attributes (if any) should be released to the Service.
To set up RapidIdentity to work with a CAS Service, begin in Configuration > Security > Identity Providers > Federation Partners.
- Click Add Federation Partner and choose the CAS option from the drop-down menu.
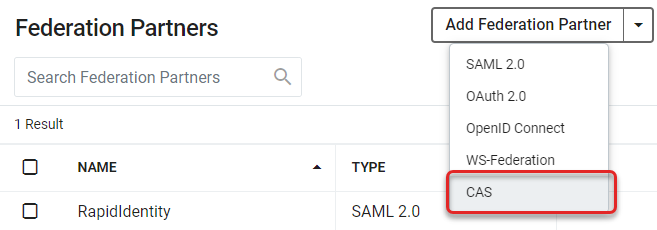
- This will open the Federation Partners > Central Authentication Service (CAS) configuration screen. There are multiple sections on this screen with fields that make up CAS Configuration for RapidIdentity. First, give the service a name. Descriptions are optional but recommended.
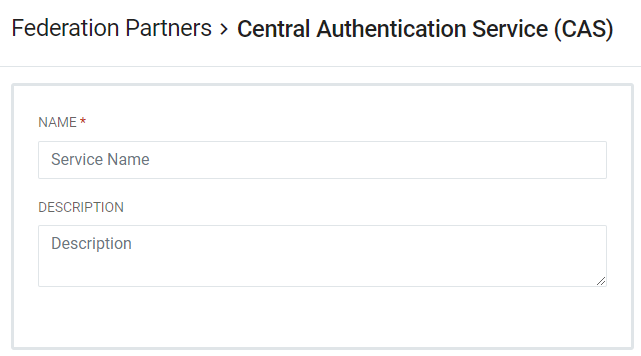
- The CAS protocol revolves around the issuing of tickets with various types: Ticket-Granting, Service, Proxy-Granting, and Proxy. The Ticket Lifetime fields show the default ticket lifetimes set by RapidIdentity by ticket type. These values can be changed or added to.
Tickets are tied together in a way that, for example, when a user logs out and their Ticket-Granting ticket is destroyed, all of the tickets which were ultimately issued by that Ticket-Granting ticket are also destroyed. Likewise, when a Proxy-Granting ticket is destroyed, all Proxy-Granting and Proxy tickets issued by it are also destroyed. If a CAS Service is deleted, all tickets issued to that Service are destroyed. RapidIdentity has a cleanup job that runs every 10 minutes and is in charge of destroying expired tickets.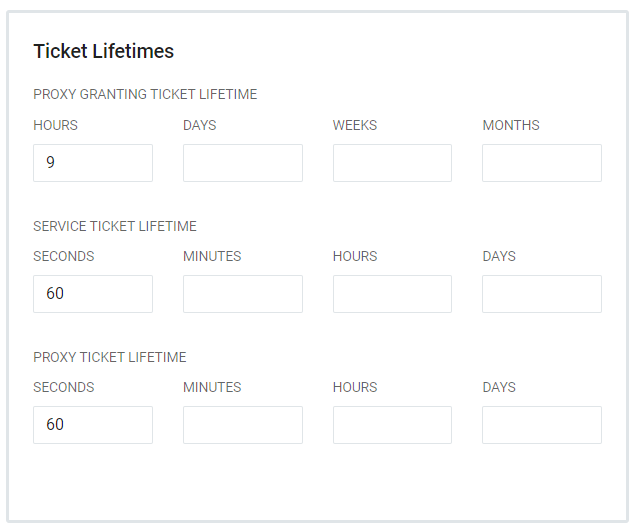
| Ticket Type | Description | Default Lifetime |
| Proxy Granting | Issued to a particular CAS Service upon successful validation of a Service or Proxy ticket. These are used by the server to issue Proxy Tickets and will only be issued if the CAS Service has been configured to allow proxying. | 9 Hours |
| Service | Issued to a particular CAS Service and invalidated by the server in exchange for user attributes and/or a Proxy-Granting Ticket. | 60 Seconds |
| Proxy | Issued to a particular CAS Service after a Proxy-Granting ticket is successfully validated. | 60 Seconds |
- The Username Attribute field has multiple options that are determined by the Type of Username Attribute chosen. These fields are LDAP attribute value definitions and their required settings.
- Random - Requires a Length setting. The default is 16 characters.
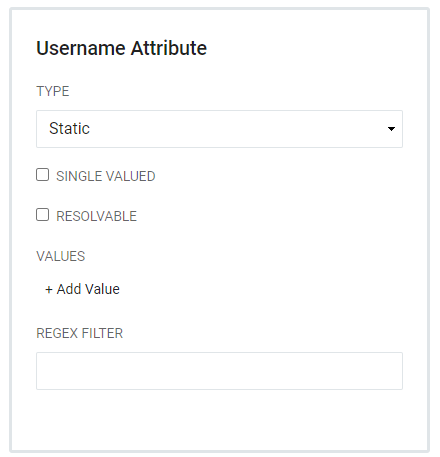
- Static - Allows users to add Values and has the capacity for a Regex filter.
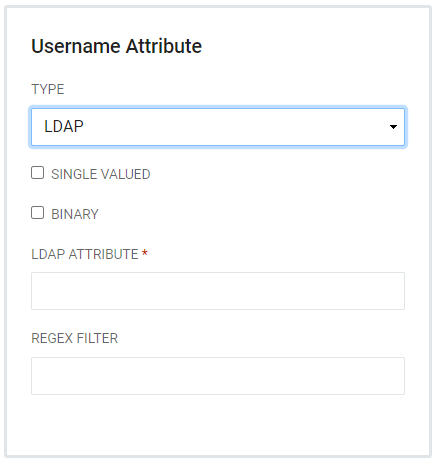
- LDAP - Requires the name of an LDAP Attribute and also has the capacity for a Regex filter.
- Random - Requires a Length setting. The default is 16 characters.
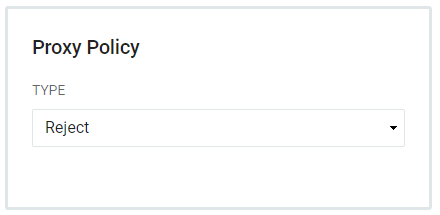
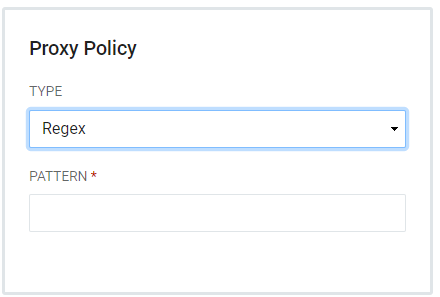
- Proxy Policies instruct the registry application to determine whether it is allowed for proxy authentication. Choose from Reject, Exact, and Regex. By default, a CAS Service will not allow proxying. If proxying is required, then define one of the following Proxy Policies.NoteTake care when allowing a Service to use proxy authentication. Misuse of this feature can leave RapidIdentity open to security leaks or other attacks.
CAS Endpoint URLs Description /idp/profile/cas/login CAS Login /idp/profile/cas/logout CAS Logout /idp/profile/cas/validate Service ticket validation /idp/profile/cas/serviceValidate Service ticket validation (CAS 2.0) /idp/profile/cas/proxyValidate Service/Proxy ticket validation (CAS 2.0) /idp/profile/cas/proxy Proxy ticket service (CAS 2.0) /idp/profile/cas/p3/serviceValidate Service ticket validation (CAS 3.0) /idp/profile/cas/p3/proxyValidate Service/Proxy ticket validation (CAS 3.0) - Reject - Rejects all proxy attempts. This is the default.
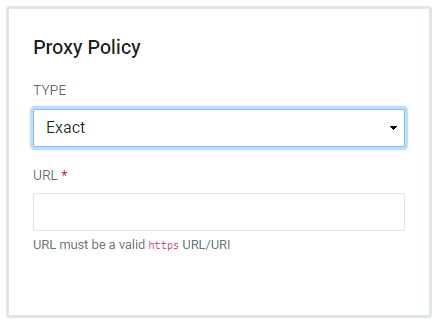
- Exact - Allows proxying. The Proxy Callback URL presented must exactly match the URL defined for the CAS Service.
- Regex - Allows proxying. The Proxy Callback URL must match a regular expression pattern defined for the CAS Service.
- Reject - Rejects all proxy attempts. This is the default.
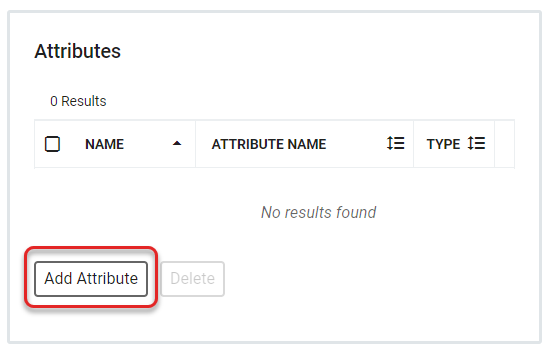
- The Attributes section allows you to add attributes to the partner to be used during authentication to define the attribute to be passed through to the service by RapidIdentity. This will open a sidebar with fields for attribute preferences.
EXAMPLES: a CAS Service using protocol version 2.0 or 3.0 will receive an identifier for the authenticated User when validating Service/Proxy tickets using the /serviceValidate and /proxyValidate endpoints. By default, the user identifier will be the authenticated user's RapidIdentity "username" attribute value. If this is not appropriate, RapidIdentity can release another value. This can be defined on a per-CAS Service to be a random value, a static value with or without resolvable tokens, or an LDAP attribute value. Since the protocol only allows a single value to be returned, if the multiple values are resolved for the authenticated user, the "first" one will be used.
A CAS Service using protocol version 3.0 and validating Service/Proxy tickets using the /p3/serviceValidate and /p3/proxyValidate endpoints has the opportunity to receive custom attributes in addition to the user identifier described above. These are defined on a per-CAS Service basis and a particular CAS Service can be configured to return zero or more single or multi-valued custom attributes. Each attribute must define the name of the attribute exactly as it will appear in the protocol response. Since XML is the default format for the protocol response, the attribute name MUST be valid for an XML element name. Specifically, this means that the name cannot contain spaces or other whitespace characters, must start with a letter or underscore, and cannot start with the letters "xml" in any case combination.
Custom attributes are also defined with a value definition, which indicates how the value(s) are to be computed. This can be a random value, a static value with or without resolvable tokens, or value(s) from an LDAP attribute.
| Field | Description |
| Name | Provide a unique name for this attribute. |
| Description | Add an optional description to further define its purpose. |
| Attribute Value | Choose the type of value definition to be used for this attribute. Note that the three options are Random, Static, and LDAP with the associated settings for each value. |
| Attribute Name | Add an attribute name. |
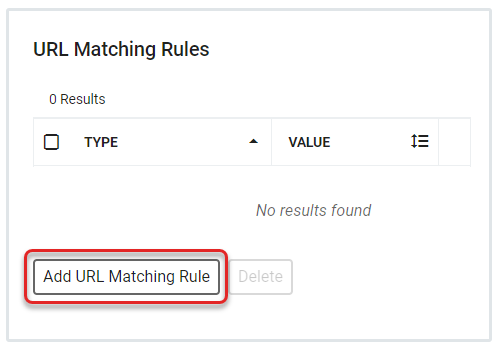
- A CAS Service is generally identified by a URL during protocol operations. Since RapidIdentity will only allow interaction with Services that have been pre-registered, the Service URL must exactly match only one registered CAS Service. This final section defines the URL Matching Rules for the Service. Rules can be set to Exact or Regex, with the same rules and setting requirements as these rules had in Proxy Policies.WarningIf a Service URL comes in which matches more than one CAS Service, the request will fail.
- Click Create in the final sidebar and then click Save on the main screen. The newly set up CAS Federation Partner should now be visible on the Federation Partners main screen.
Unsupported Features
The following optional features (as specified by the CAS specification) are not currently supported by the RapidIdentity CAS implementation: