Once you have completed federating Google for Single Sign on there are some additional settings in the Google Administrator Console that should be reviewed and changed as appropriate to have the best experience with RapidIdentity and Chromebooks
1) Login to Google Admin Console
2) Navigate to Menu -> Devices -> Chrome -> Settings -> Users & Browsers
- To apply the setting to all users and enrolled browsers, leave the top organizational unit selected. Otherwise select a child Organizational Unit
- Under Security, select Enable SAML-based single sign-on for Chrome Devices from the list

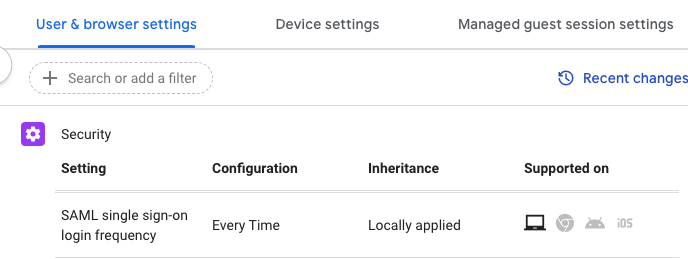
- Under Security, select SAML Single sign-on login frequency from the list and apply your desired Sign-on Frequency options. We recommend Every Time
- If you are going to use WebAuthn Authentication Policies within RapidIdentity with accounts using Chromebooks
- Under Security, select WebAuthn from the list and apply your desired options of FIngerprint and/or Pin.

- Under Security, select WebAuthn from the list and apply your desired options of FIngerprint and/or Pin.
- To Configure the behavior of unlocking from the lock screen:
- Under Security, select SAML single sign-on unlock frequency from the list. To require RapidIdentity for unlocks set this to 0.
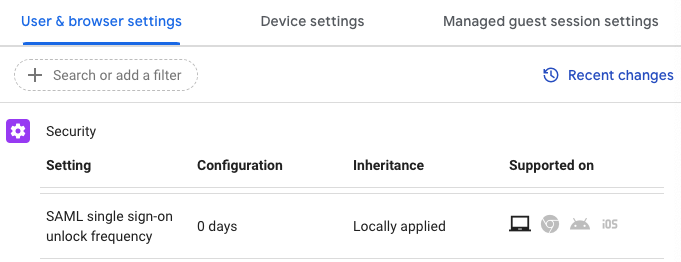
- Under Security, select SAML single sign-on unlock frequency from the list. To require RapidIdentity for unlocks set this to 0.
- Under Security, select Enable SAML-based single sign-on for Chrome Devices from the list
3) Navigate to Menu -> Devices -> Chrome -> Settings -> Device
- To apply the setting to all devices, leave the top organizational unit selected. Otherwise select a child Organizational Unit
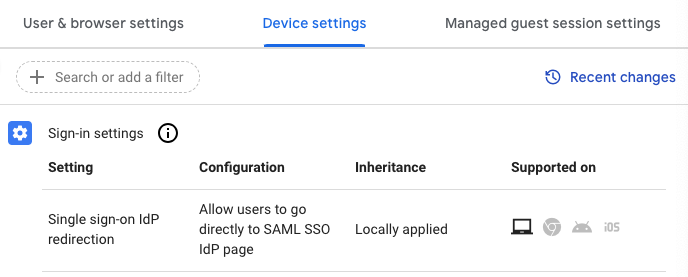
- Under Sign-in Settings, select Single sign-on IdP redirection and set this to Allow users to go directly to SAML SSO IdP Page
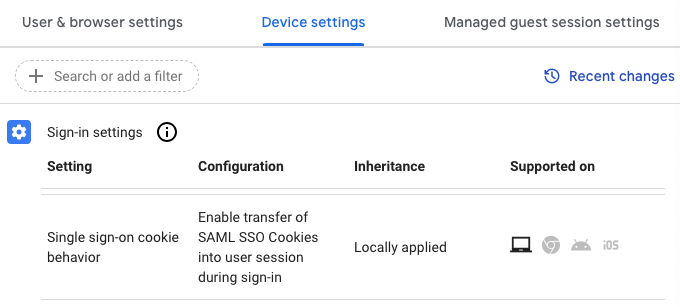
- Under Sign-in Settings, select Single sign-on cookie behavior and set this to Enable transfer of SAML SSO Cookies into user session during sign-in
- If you will be using QR Codes for Authentication Policies within RapidIdentity with accounts using Chromebooks
- Under Sign-in Settings, select Single sign-on camera permissions and set this to https://YOUR-RAPIDIDENTITY-TENET?idp?AuthnEngine#/qr-code
- Under Sign-in Settings, select Single sign-on camera permissions and set this to https://YOUR-RAPIDIDENTITY-TENET?idp?AuthnEngine#/qr-code
- Under Sign-in Settings, select Single sign-on IdP redirection and set this to Allow users to go directly to SAML SSO IdP Page