Bridge Connections Down/Failing Troubleshooting
**This is troubleshooting for Rapid Identity Cloud tenants only.
Common Errors:
- errorMessage : Unable to establish a connection to LDAP
- ERROR isFile(): org.apache.commons.vfs2.FileSystemException: Could not determine the type of file
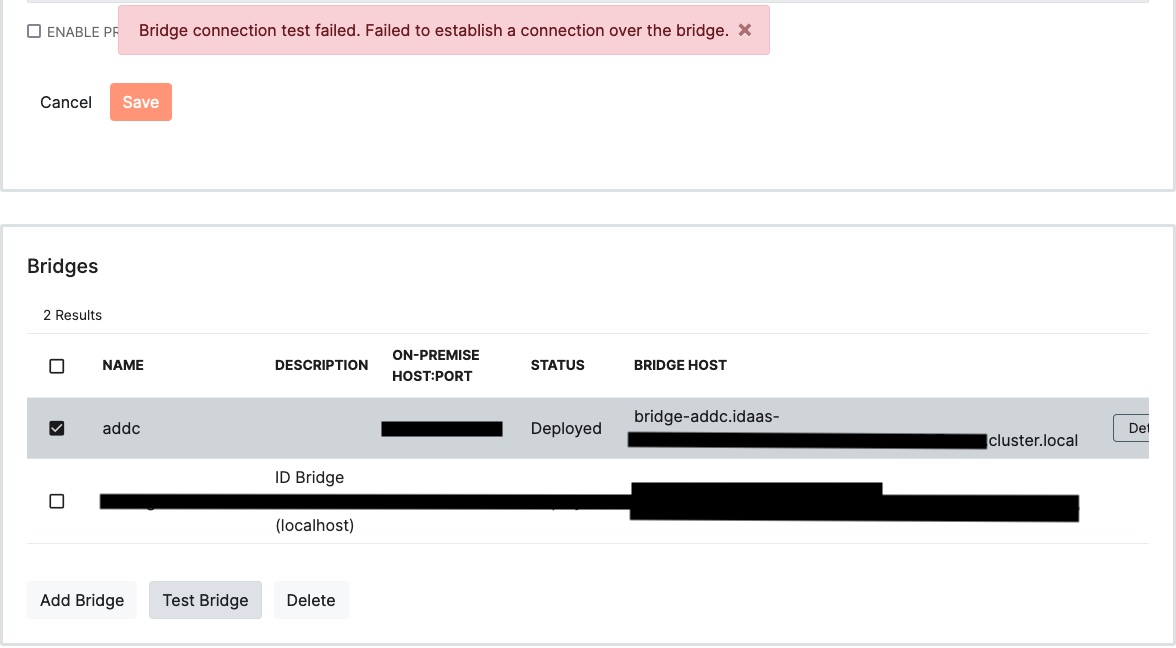
- Bridge connection test failed. Failed to establish a connection over the bridge.
- ERROR openADConnection(): An error occurred while attempting to connect to server bridge
- Your Action Sets that are setup for your bridge will also begin to fail.
- ERROR: Uncaught error while processing System.ComponentModel.Win32Exception (2): The system cannot find the file specified.
- No “HeartBeat” for Bridge at all (It will tell you the last heartbeat connected to bridge).
Test Identity Bridge.
**Log into Tenant, navigate to Configuration > Security > Identity Bridge
Troubleshooting Steps:
-
Check Task Manager to see if there are any chisel.exe processes currently running.
- (there should be one process for each bridge listed in your tenant)
-
If chisel.exe is NOT Present in Task manager, check to see if the file has been removed by an Antivirus or Windows Defender.
- File should be located C:\Program Files\Identity Automation\Identity Bridge Agent\chisel.exe
- If chisel file is missing, check to see if it was quarantined by antivirus, whitelist the program if necessary.
-
If chisel.exe is Present in Task manager, check to see if the network firewall has begun filtering websocket traffic.
- ex: ws://bridges.us002-rapididentity.com:80, ws://bridges.us001-rapididentity.com:80, https://ams.ia/us001-rapididentity.com/agents/<chiselID_hexcode>
- Set up DEBUG mode to detect network connectivity issues.
- We have seen this in content aware firewalls like Palo Alto and Fortigate.
-
Check local firewall to make sure that chisel traffic is not being blocked. The ID Bridge will need to communicate over port 636 to the domain controller configured in the Tenant. The ID Bridge server will also need to communicate over port 443 to the AWS cloud.
- Windows tool ldp can help diagnose an issue connecting to the Domain Controller over port 636.
-
Open the agent.log and look for clues: C:\Program Files\Identity Automation\Identity Bridge Agent\agent.log
- You can download the agent.log to attach to a Support Case.
-
Setup DEBUG Mode:
- Open Services.msc
- Locate service named Identity Automation Bridge
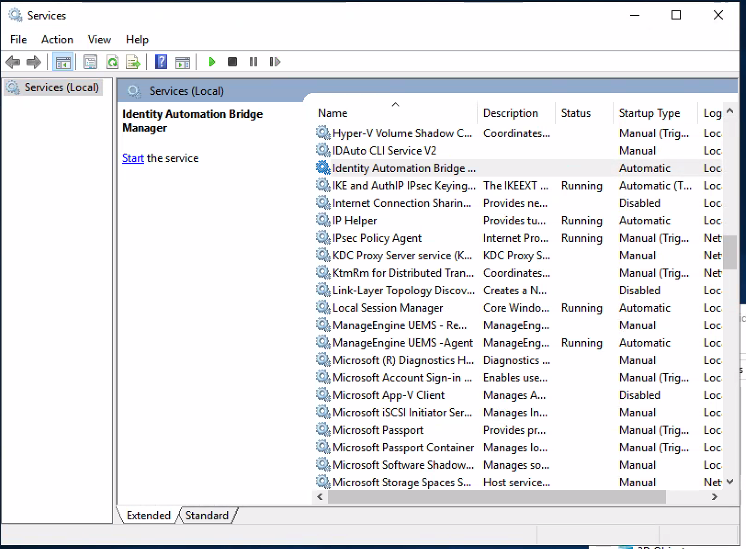
* Stop Identity Automation Bridge service
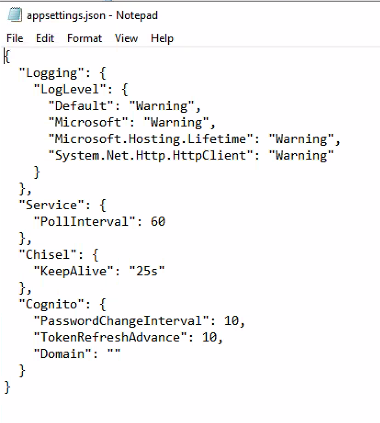
* Open Notepad 'run as Administrator'
* Open file C:\Program Files\Identity Automation\Identity Bridge Agent\appsetting.json
* find/replace "Warning" with "DEBUG", there should be 4 instances, then save.
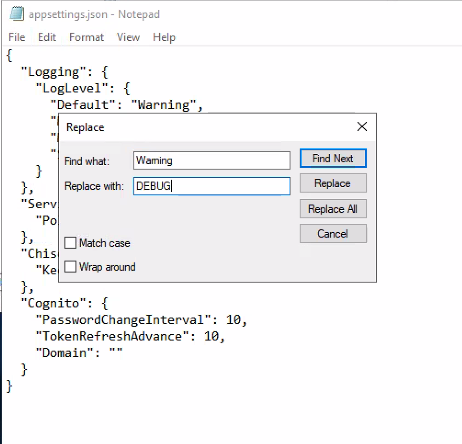
* rename agent.log to agent_[date].log.
* In Services.msc start the Identity Automation Bridge service.
* Run a test of the ID bridge connection from within your tenant (as seen above).
* Open C:\Program Files\Identity Automation\Identity Bridge Agent\agent.log
- Errors with the network firewall can be seen as this picture:
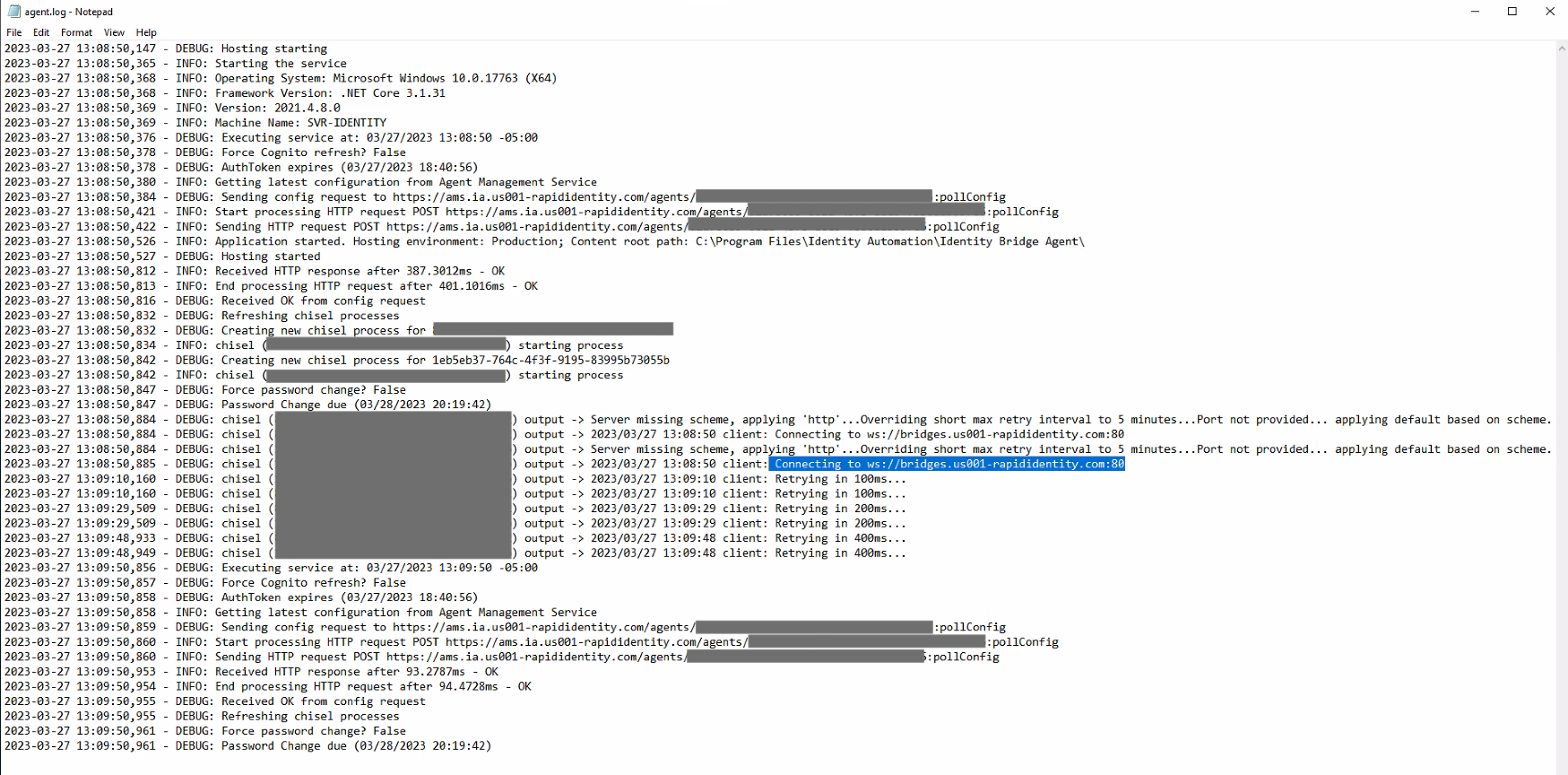
Make sure to change the appsetting.json back to Warning and restart the Identity Automation Bridge Manager service after troubleshooting is complete, so your server doesn't fill up with unneccessary logs.