RapidIdentity Cloud provides dynamic end-user authentication methods to support a secure, seamless digital ecosystem focused on learning outcomes. Authentication can be tailored to the needs of individual end users. Students, teachers, and administrators can each authenticate securely with a single login policy that is appropriate for their needs and risk levels.
Authentication Overview
Multi-step authentication: user is required to use two or more of the same factor.
While this option is more secure, it is not the most secure. However it is more appropriate in K-12 education for younger learners than true MFA.
Two-factor authentication: user is required to use two different factors.
Multi-factor (MFA) authentication: user is required to use three different factors.
Authentication Factors:
- Type I - Something you know (Password, Challenge, PIN, PictoGraph)
- Type II - Something you have (Fido, TOTP, QR Code, Duo, EMail, SMS, PingMe)
- Type III - Something you are (Kerberos, Biometrics, WebAuthN)
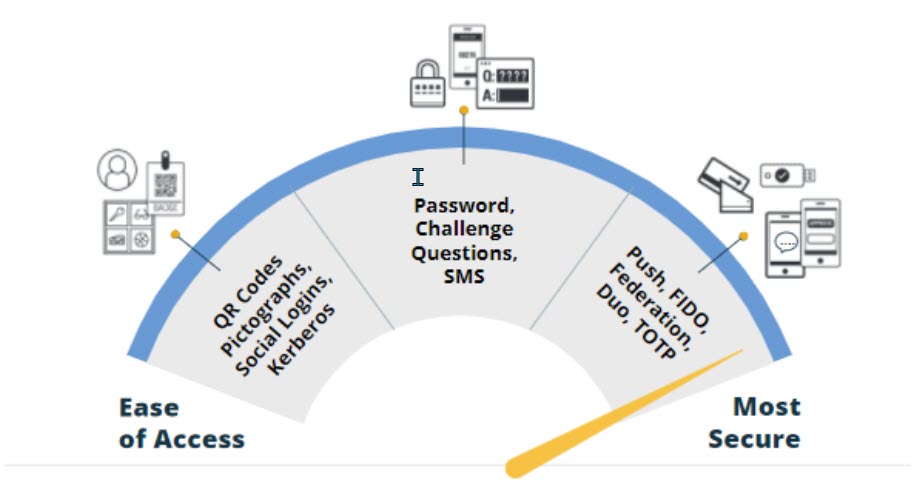
Rationale for Authentication Policies
Passwords - Passwords are a standard practice for system access and can be effective as long as they are strong, secure, and not reused across systems. The challenge facing password use today is the high number of data breaches and end user passwords that have been compromised and are still in use. When a user has the same username and password across multiple systems, it increases the susceptibility to account compromise and data breaches. Utilizing alternative authentication methods and two, or multi-factor, authentication increases your district/institution’s security posture.
Alternate Authentication Methods - Alternate authentication methods move away from passwords and allow more secure access to systems. Using a device, security tokens, biometrics, and other methods will grant end users secure entry to a system with a dependency on passwords.
Two Factor and Multi-Factor Authentication - Multiple authentication methods facilitate user login while confirming user identity for the most secure access to a system. The best practice for multi-factor authentication is to require users to have all three factors: something they have, know, and are to login. Two factor authentication only requires two of the three factors.
Authentication Configuration in RapidIdentity Cloud
End users in RapidIdentity can be assigned one or more specific authentication methods to access RapidIdentity.
- When involving a third-party software, the authentication method must be configured as applicable in both RapidIdentity and the third-party as needed. (i.e. Duo, Kerberos)
- Authentication methods are assigned to users within the RapidIdentity Identity Store based on user attributes.
- A specific authentication order can be set for end users.
- Any authentication policy can have multiple methods to ensure two-factor or multi-factor authentication.
- Multiple policies can apply to users to ensure there is always a method for the user to get in (i.e. if a user doesn’t have their phone for SMS, they can fall back to a token, challenge question, or TOTP authentication method.)
- Note that your security posture is only as strong as the weakest link here. For example, if you allow a user to fail over to password-only authentication, then even if other options require MFA, the overall policy is still single-factor since passwords are a single point of failure.
Supported Authentication Methods in RapidIdentity Cloud
| Method | Description | Considerations |
|---|---|---|
| Duo* | Users authenticate with a preconfigured Duo account | Available when Duo software is in place and configured. |
| Users authenticate through a RapidIdentity email address. | Available if personal emails are stored in RapidIdentity. | |
| Federation | This allows for authentication to an alternate Identity Provider (IdP). | Available when another Identity Provider is necessary (e.g., ADFS, Okta). In this configuration, RapidIdentity is the Service Provider. |
| WebAuthn* | Allows users to authenticate with WebAuthn (e.g. a licensed FIDO U2F security key). | Requires a WebAuthn capable device (e.g. FIDO tokens, a physical token that users must have on their person in order to gain access to the system) |
| Kerberos | Users authenticate with licensed, browser-provided Kerberos tickets automatically. | Typically available in AD environments. This will allow end users on a domain-joined computer to use the login token for authentication. |
| Password | Users authenticate with their password. | The typical default method for authentication. |
| Pictograph | Users can authenticate against the default image pool. By default, the user is required to select three images. | Recommended for younger students, i.e. PreK-12 or students with special needs. |
| PingMe | Users authenticate using the RapidIdentity Mobile client application on a mobile device. | Requires mobile devices. This method enables push notifications to the RapidIdentity Mobile App. |
| Portal Challenge (Questions) | Users authenticate with their RapidIdentity Portal Challenge Questions. | Typically used for password recovery. Can also be used as an authentication method. |
| QR Code | When enabled, a valid, secure QR code must be scanned. | QR codes must be printed or photographed and can be scanned to gain access to the system. Recommended for Elementary students or students with special needs. Note: QR Authentication Codes are generated based on the user ID and password, so the security is tied to the security of the underlying password. |
| SMS | Users authenticate with a code sent to their mobile device through SMS. | Requires mobile devices. Recommended for teachers and staff members who are able to use SMS authentication. SMS is a convenient method that is widely used in the industry, but keep in mind that SMS authentication has some risks that you should consider when evaluating your overall security posture and user education policies. |
| TOTP | Users enter a Time-Based One-Time Password (TOTP) code generated by an app on a device (e.g., Google Authenticator, RapidIdentity Mobile app, or Microsoft Authenticator). | One of the easiest and most user-friendly methods for authentication. May require a hard token or app. |
*Requires third-party vendor software or hard token.