Join Windows 10 machine to Azure AD using hybrid domain join method
We're going to see the steps on how to join Windows 10 or later machines to Azure Active Directory
using hybrid domain join method. If you have an on-premises Active Directory domain services environment
and you want to join your domain joined computers to Azure Active Directory we can accomplish this task by doing hybrid Azure AD join. When we hybrid join a device it means that it is visible in both our on-premises Active Directory and in Azure Active Directory, and then we can manage them from both.
Prerequisites
We have two VMs for this set up. The first is our domain controller (Windows Server 2016), this domain controller is synced with an Azure Active Directory using Azure AD connect tool, and the second VM is our Windows 10 client computer which is joined to our on-premises active directory.
Microsoft Entra ID Free license does not support Intune MDM. In order to Setup Intune MDM, Azure Global Admin user should have Microsoft Entra ID P1 or P2.
Steps for Hybrid join in Intune
To perform below steps you must have access to both an on-premises (Windows Server) administrator and an Azure AD global administrator.
Open Azure AD Connect. To install follow link.
Click on Configure
Click on Configure device options and click Next.
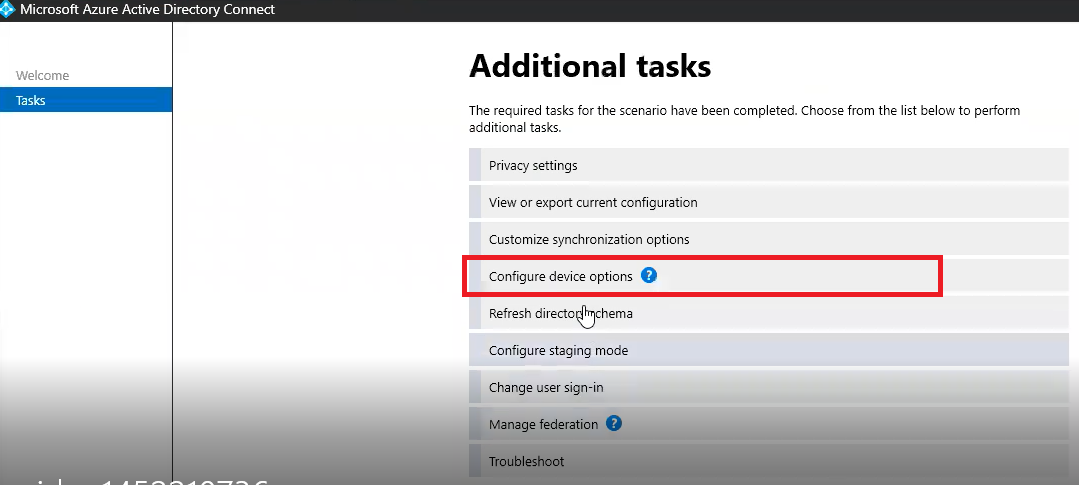
Click on Next
We will now be prompted to enter credentials from a Azure AD tenant’s Global Administrator’s credentials, so already the username is displaying here. So, just need to enter the password and hit Next.
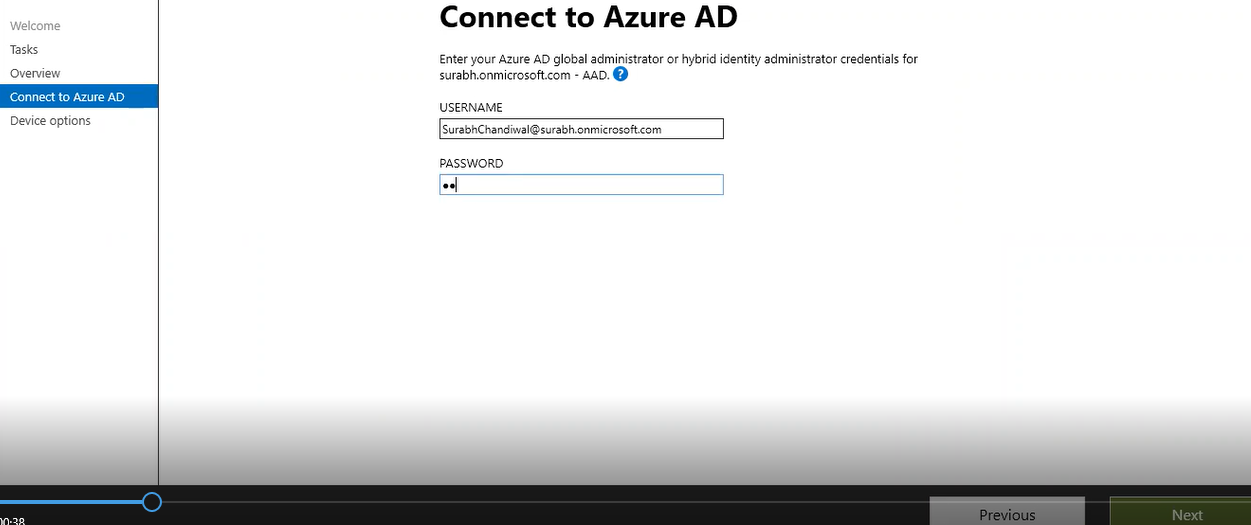
Configure hybrid Azure AD join option is pre-selected and click Next.
.png)
Select what types of devices we intend to join, choose Windows 10 or later domain join devices and click Next.
.png)
Select the check box in front of our forest, click on the drop down arrow, and choose Azure Active Directory for Authentication Service and then click on Add.
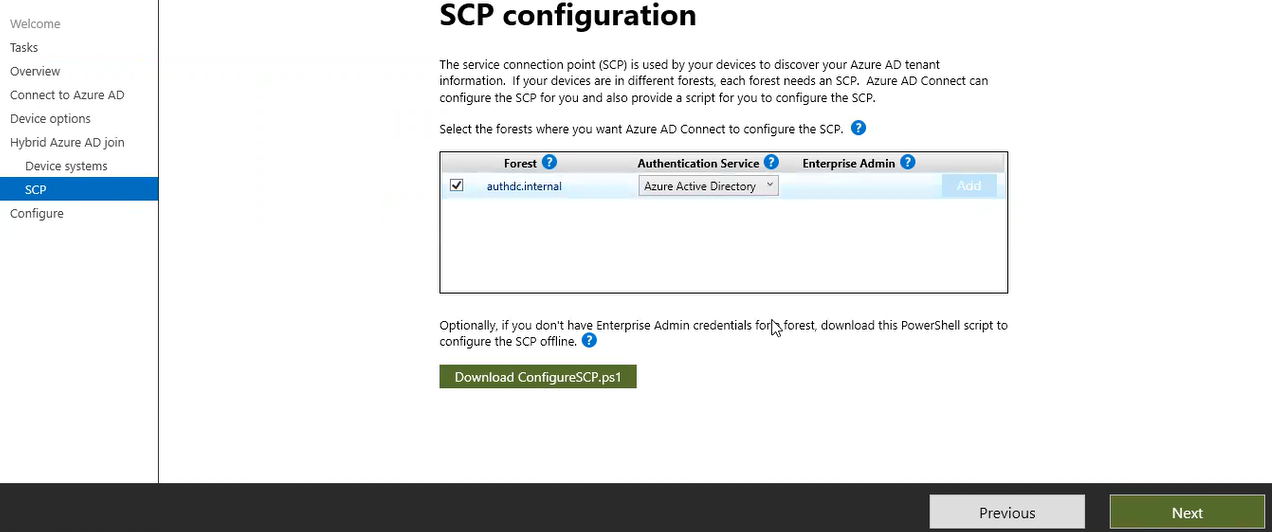
Next, provide credentials for admin account and click Ok and Next.
Click Next and then click Configure on next page to start the process.
Click Exit when configuration completes.
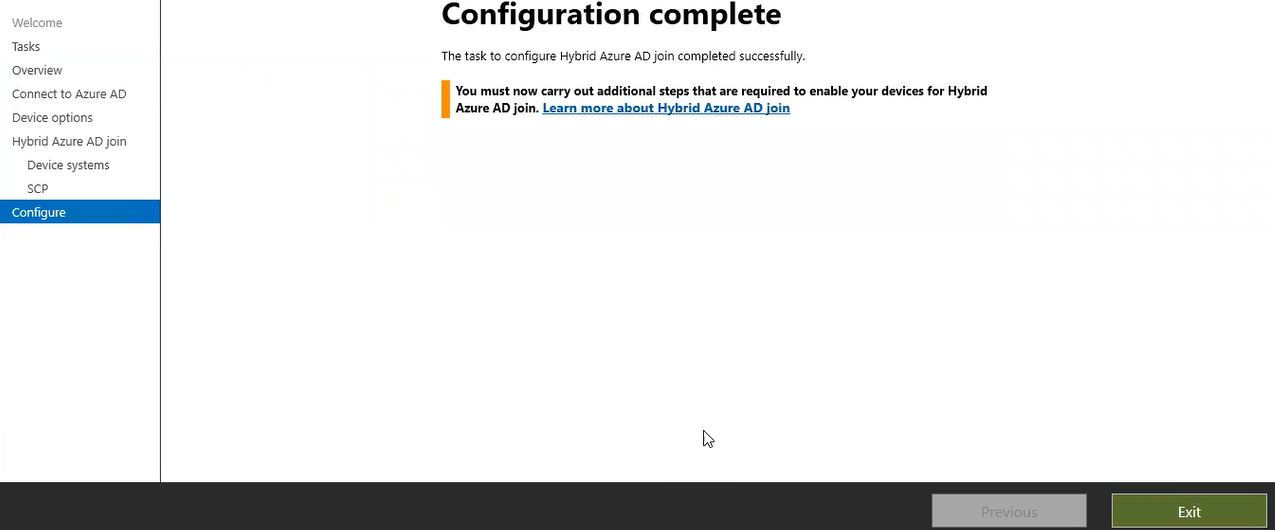
Now run Start-ADSyncSyncCycle -PolicyType delta command on Admin Power shell to manually sync Azure AD to our on-premises Active Directory. If you receive an error when running above comment then check troubleshooting tips.
.png)
To confirm Windows 10 device registration we need to reboot Windows 10 once.
After reboot, sign into Windows 10 computer.
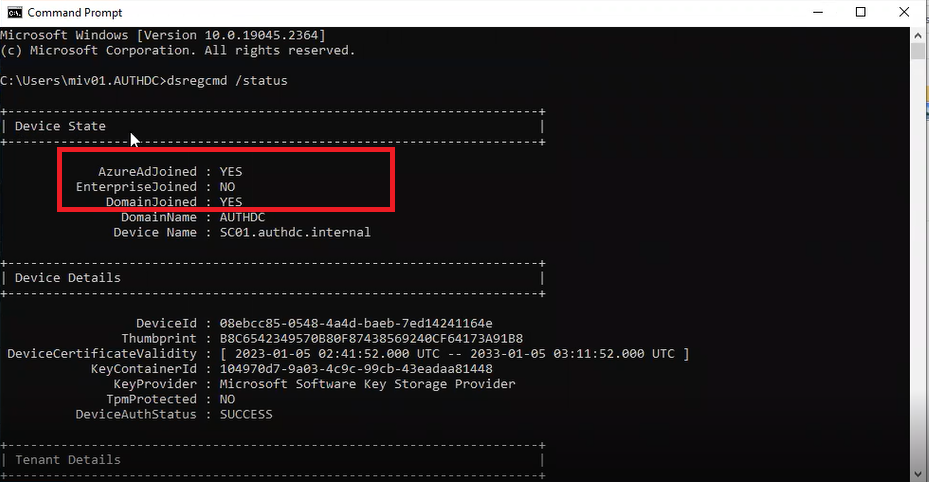
Open Command Prompt and type dsregcmd /status
If you see AzureAdJoined as YES under device state that means the device is hybrid Azure AD joined, as well as joined to our Azure Active Directory, under DomainJoined we can also see YES .
If you do not see Azure AD joined: Yes then follow the given documents and complete your AD Group policy and MDM Intune Configurations: Document
After configure GPO policies make sure you have done with the given Pre-requisites
Note: Microsoft Entra ID Free license does not support Intune MDM. In order to Setup Intune MDM Azure Global Admin user should have Microsoft Entra ID P1 or P2.
Alternatively one can check if device is enrolled in Intune by logging into Azure portal.
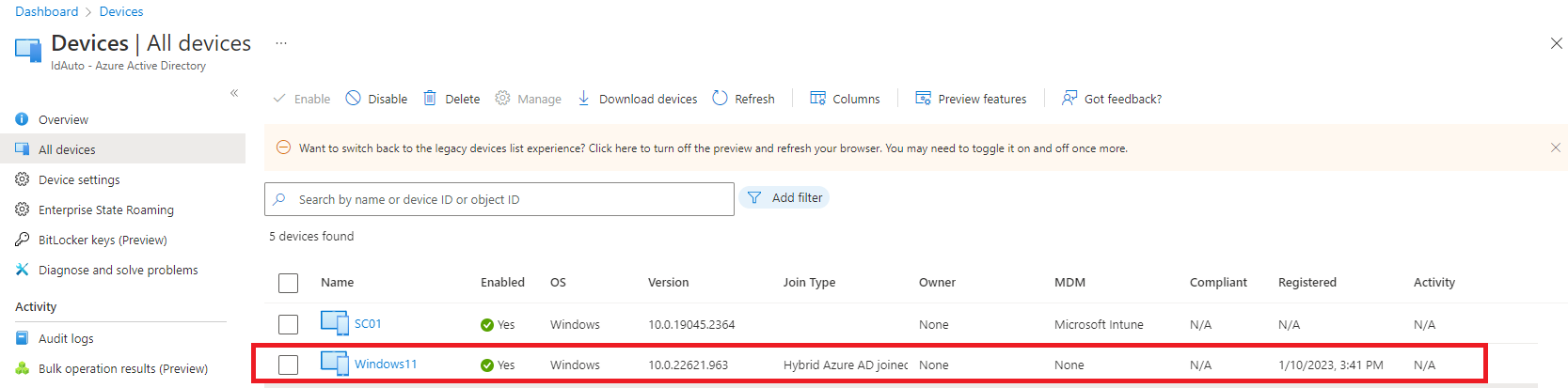
Now go to Device>All Devices and here we can see join type is hybrid Azure AD join.
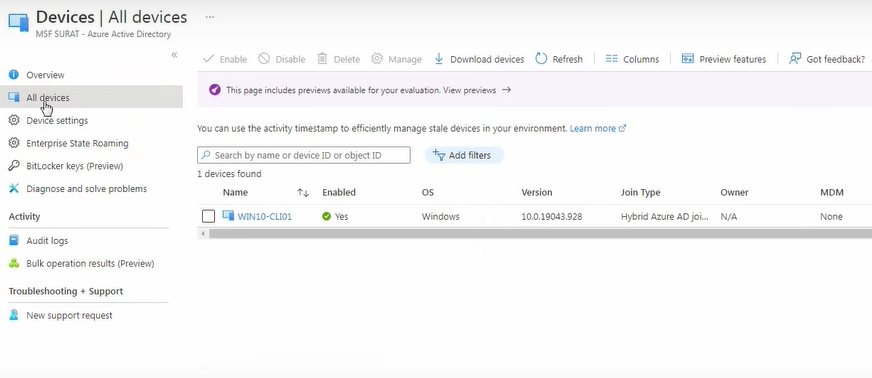
Make sure Owner as well as MDM column is also present in all devices page, if not than follow below steps:
For owner, add UPN Suffixes and update users (2nd point in the document).
For MDM column update do linked steps (2nd point in the document).
Troubleshooting tips
If in case you see device state as Pending in Registered column under All devices in Azure portal then to fix the problem follow below steps.
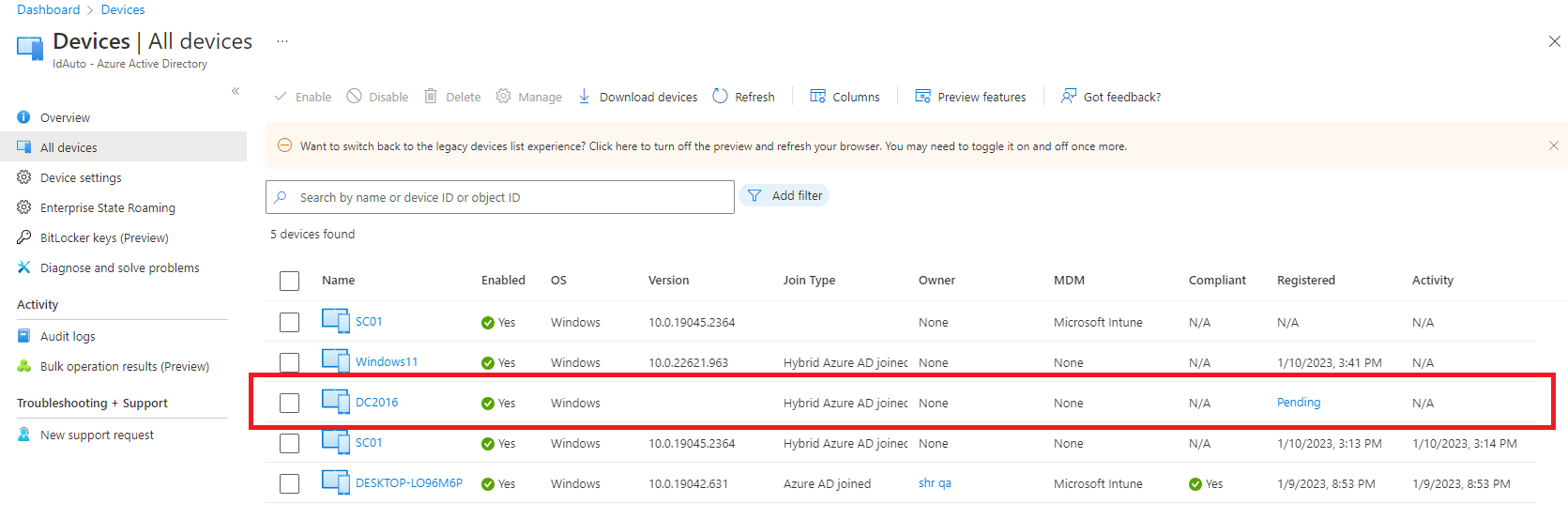
Go to machine which is showing as Pending state
Open Command Prompt and type dsregcmd /leave
The device will get unregister which can again verified by typing dsregcmd /status in Command Prompt
Restart the machine
Again open Command Prompt and type dsregcmd /status , you will see AzureAdJoined as yes
Now again open Azure portal, Go to All Devices
You will see timestamp under Registered column
Running Start-ADSyncSyncCycle -PolicyType delta command on Admin Power shell:
Run command Get-ADSyncScheduler on powershell and check if the value of SchedulerSuspended is True or False, if the same is True than the scheduler is suspended.
Run Set-ADSyncScheduler -SchedulerSuspended $false to change the value of suspended to False.
Now again run Start-ADSyncSyncCycle -PolicyType delta command and the same should be successful.







