Over the past two weeks, there has been a significant increase in spear phishing attempts targeting Microsoft credentials and personal accounts on platforms like Yahoo, Netflix, and Amazon. During this time, we observed an unusual volume of attacks employing device fingerprinting to track users, along with other tactics such as MFA bypass tools and hosting on legitimate infrastructure. Here are some examples and highlights of these attacks.
punchbolwinvitees[.]de/g/
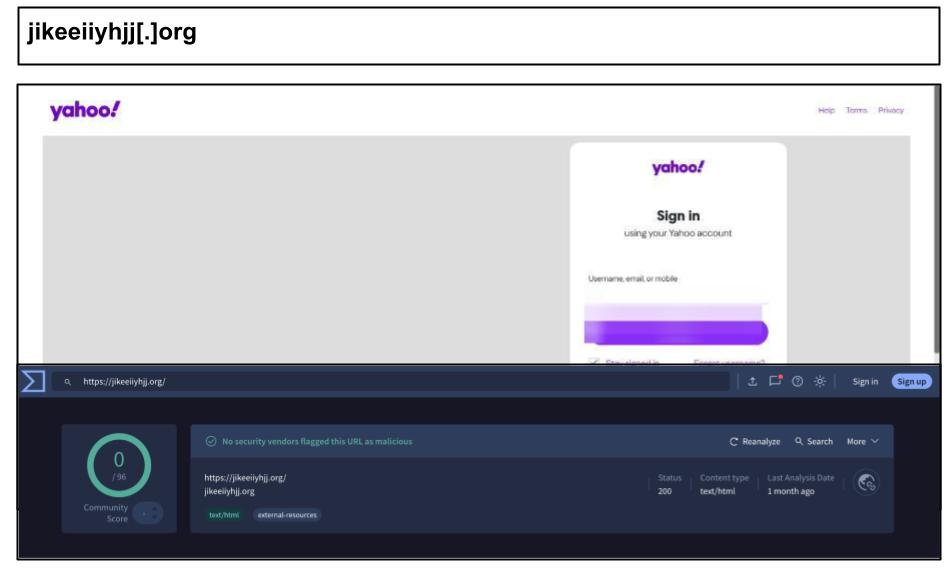
jikeeiiyhjj[.]org/
e9lqcsobfhffcdcp0w1e[.]richotillomaniad[.]ru
resolve-caseauthentification-netflix-id[.]cricketshoe[.]com
hadewiumimiforlongway[.]com/vic/yio/invite/Yahoo[.]html
behymbleeye[.]online
secure[.]notificationupdate-statement[.]ntflx-en[.]cricketshoe[.]com/
prime[.]20-57-0-20[.]cprapid[.]com
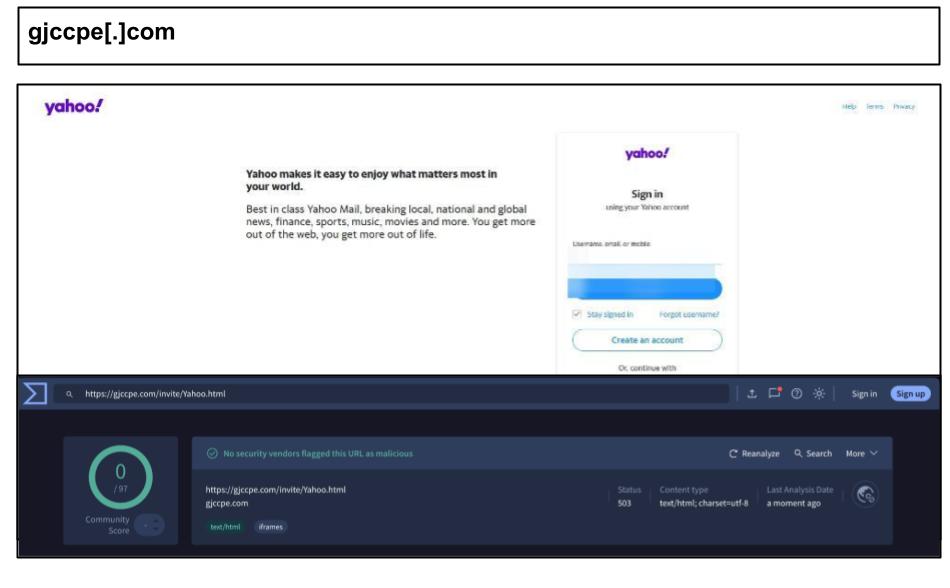
gjccpe[.]com/invite/Yahoo[.]html
108[.]181[.]34[.]45
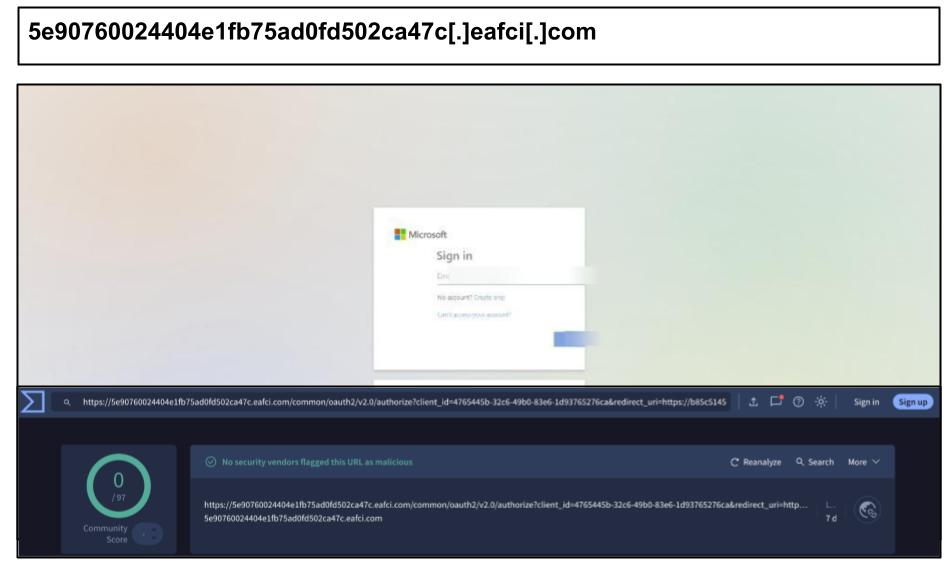
5e90760024404e1fb75ad0fd502ca47c[.]eafci[.]com
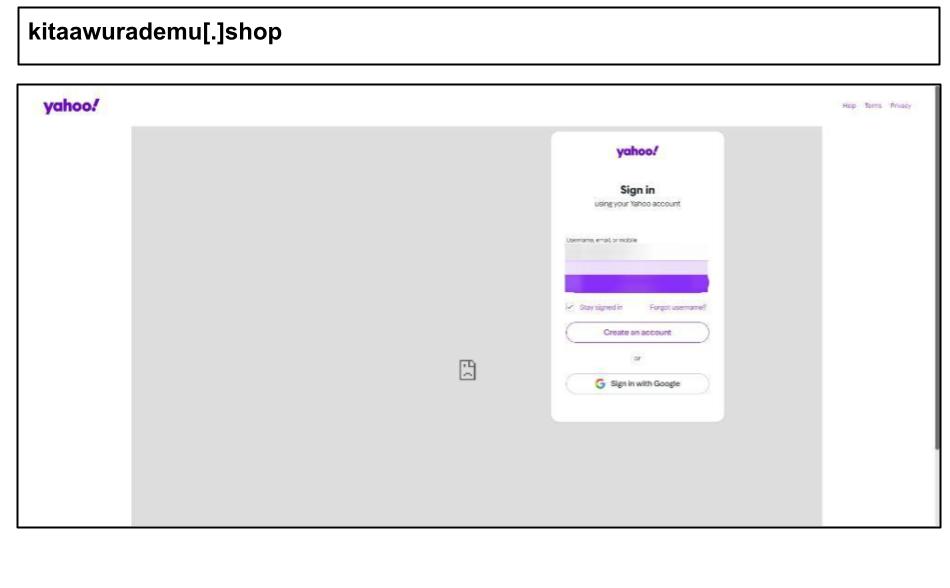
kitaawurademu[.]shop
ameuricoslamnpexjea[.]com/
dkrl[.]idrvlqvkov[.]es
sigmaman-name[.]global[.]ssl[.]fastly[.]net/
Microsoft and Outlook MFA Bypass
On April 11, an employee at a school organization clicked on a spearphishing email that contained an Adobe fileshare link.
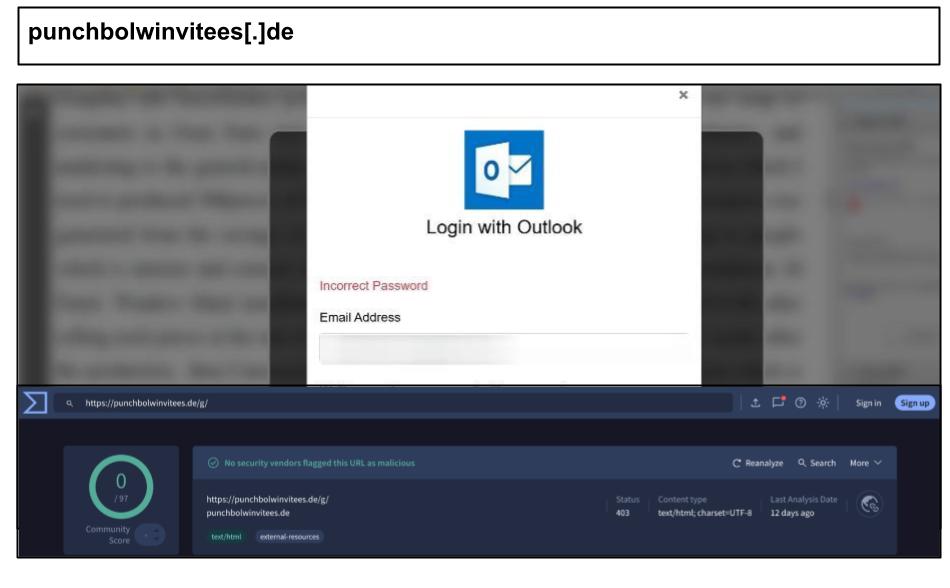
This phishing attack operates in two stages. The first stage prompts the user to enter their email and password, while the second stage requests a one-time password or other additional credentials. The attack features logos that have been customized to resemble those of Adobe, Yahoo, AOL, and Outlook.
On April 14th, a user clicked a Microsoft phishing link hosted on the Fastly CDN domain, a legitimate CDN service that was likely abused to deliver phishing payloads.
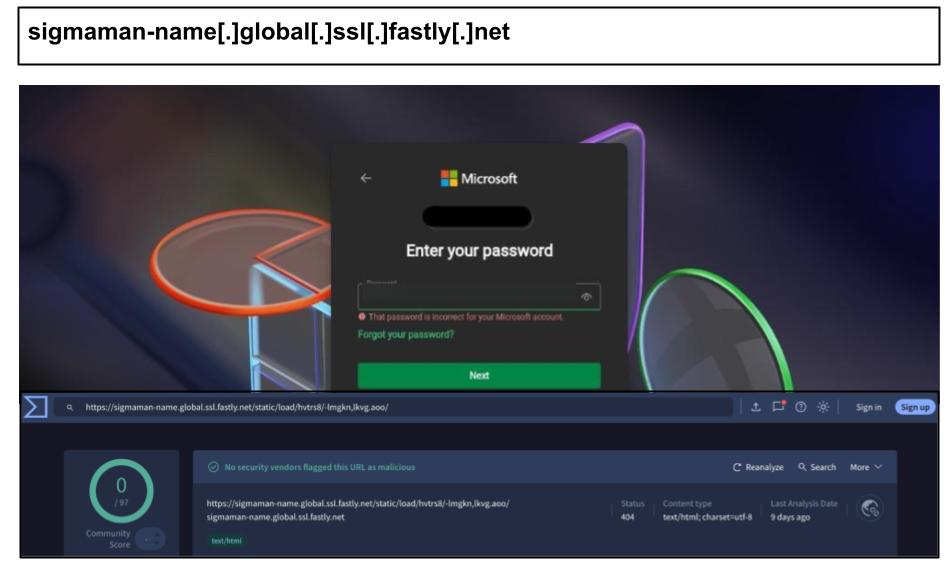
Some additional attacks attributed to Microsoft are hosted on Russian infrastructure. They impersonate Microsoft’s OAuth2 parameters, engage in SSO flow manipulation, and utilize header injection of security controls. Additionally, these attacks contain inspirational quotes sourced from the homepages of their targeted organizations.
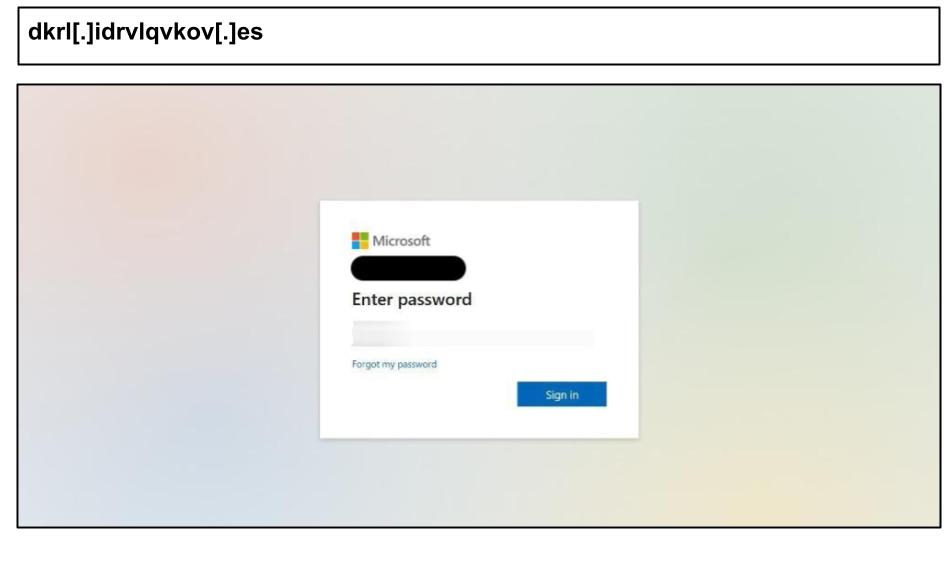
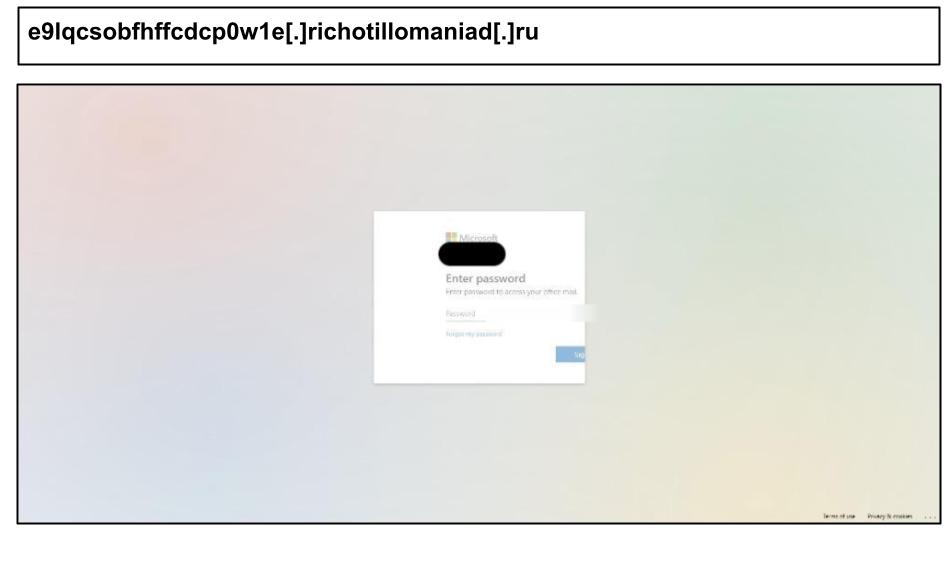
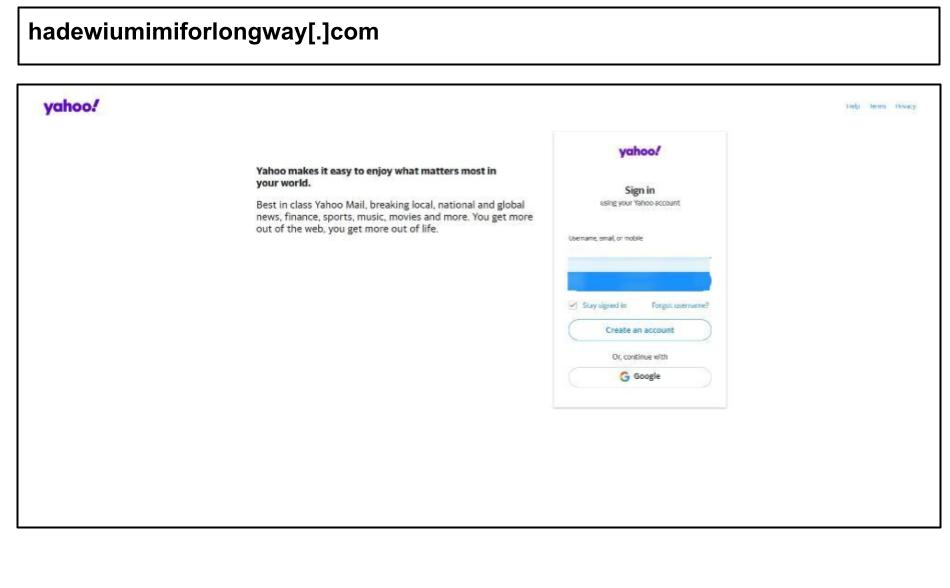
Yahoo Phishing Attacks with Device Fingerprinting
This period experienced a surge of Yahoo phishing attacks that used aggressive tracking techniques on their victims. On April 14th, an employee of a school organization clicked on the Yahoo spear phishing email below.
This attack collects detailed fingerprint data from the browser and device, including information such as device memory, the number of processors, operating system platform, and browser details. Fingerprinting enables attackers to connect stolen credentials to a specific device. As a result, they can replicate the device environment to bypass two-factor authentication using the stolen credentials.
Below are several other Yahoo examples using device fingerprinting, clicked by employees in Florida and Nevada.
Widespread Netflix Phishing
During this period, there was a notable increase in personal account phishing targeting users on their work devices. This included phishing attempts related to Netflix, American Express, and Amazon. A particularly widespread Netflix phishing campaign was hosted on the domain 'cricketshoe[.]com' and specifically targeted users in organizations located in Kentucky, Florida, and Nevada. Below are a few examples of these phishing attempts.
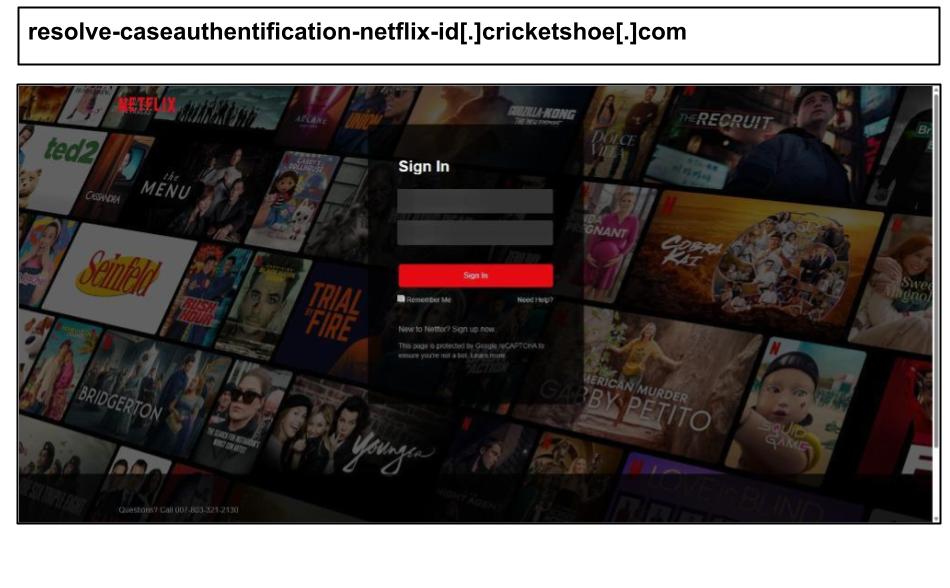
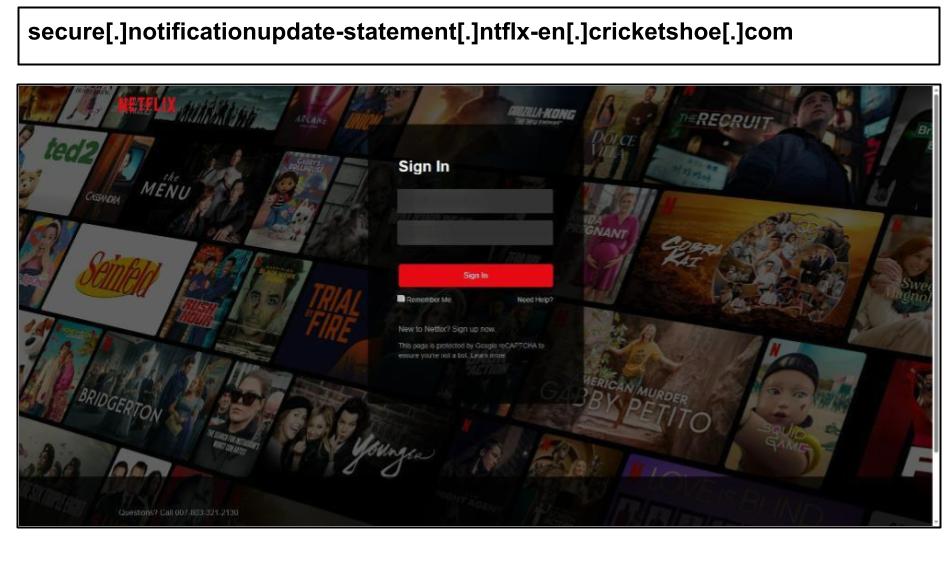
Some of these attacks involved a fraudulent support phone number, likely part of a callback scam.
Mitigations
Block the specified domains on firewalls and endpoint security solutions.
Educate users about phishing risks in file-sharing applications like SharePoint and OneDrive.
Remind users about the phishing risks associated with their accounts, even when accessed from district devices.
Instruct users to verify the support number for their financial service institution through Google, rather than calling a number found on an unverified webpage.
Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.
