In mid-July, there was an increase in spear-phishing attacks targeting users who were working from home. These attacks included MFA relay attacks and phishing links concealed within shared documents. During the same time, hackers also focused on personal accounts, with Amazon phishing campaigns that utilized aggressive user tracking tools for session hijacking and other malicious activities. Here are some examples and highlights.
click-verify[.]net
vly[.]xfsdm[.]es
sidingunlimitedmn[.]cimarch[.]info
hosttinsitoutpatzy[.]nl
login[.]icustyle[.]icu
confirmation-auth-acc-136[.]smtzeventos[.]com[.]br
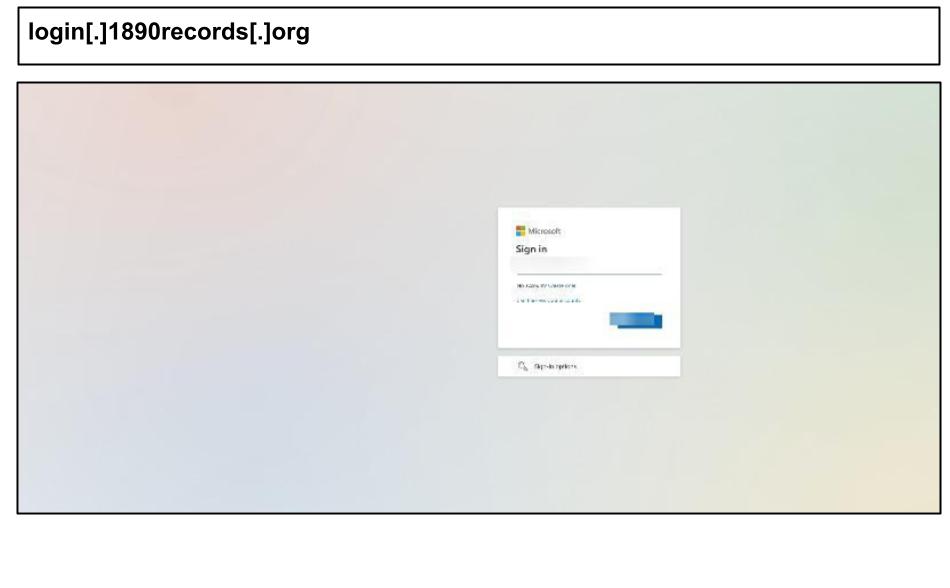
login[.]1890records[.]org
managesecure[.]log-in[.]information-reactivate-statement[.]billed[.]carlyfall[.]com
managesecure[.]log-in[.]information-reactivate-statement[.]billed[.]tinakite[.]com
Outlook and Microsoft Spearphishing
On July 7, a user at a Washington organization clicked the Outlook phishing attack on an Evite platform below.
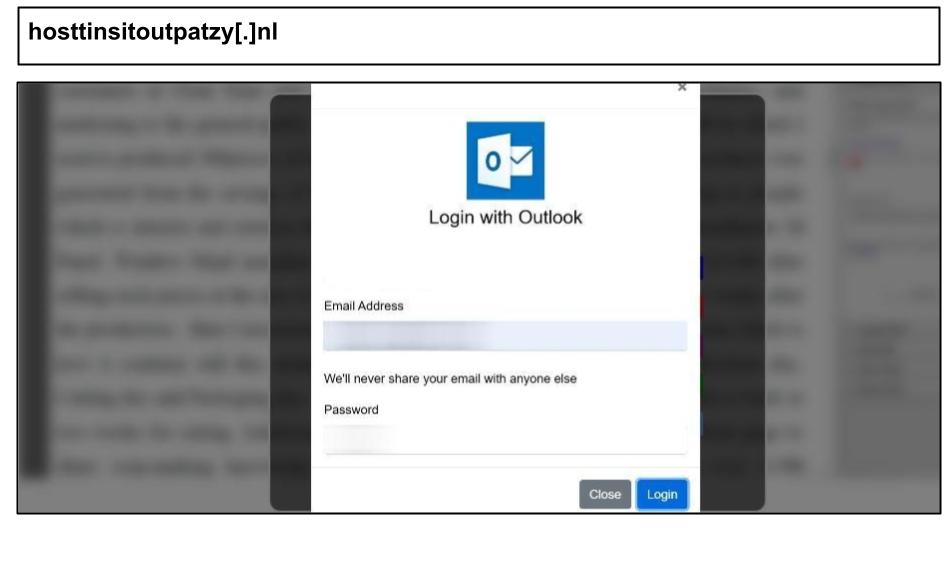
This attack contained assets to exfiltrate credentials for multiple accounts, including Outlook, Office365, Yahoo, and AOL. It includes an MFA relay kit to harvest two-factor codes and bypass multi-factor authentication.
A similar attack, perhaps using the same phishing kit, was clicked by an administrator at an Illinois organization on July 14.
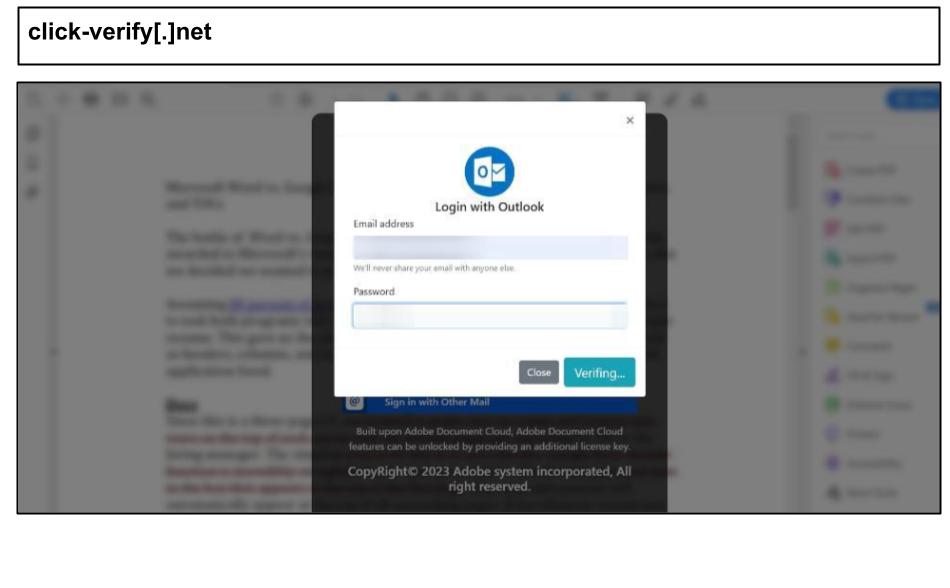
Both of these attacks not only stole emails and passwords but also returned a JSON field labeled "details" to indicate the type of credentials that were taken, such as Outlook, Yahoo, AOL, Office365, and Gmail. The phishing pages displayed the message "invalid credentials" three times before redirecting users to google.com, likely to ensure that the correct login information was captured.
On July 8, two employees at a Texas organization, including a procurement manager, clicked the Microsoft spearphish below.
The page included variables pointing to multiple legitimate Microsoft login/logout URLS.
"urlMsaSignUp": "https://login.microsoftonline.com",
"urlMsaLogout": "https://login.live.com/logout.srf",
"urlOtherIdpForget": "https://login.live.com/forgetme.srf"
These can build trust with users while confusing security analysts. On July 14th, a phishing attack likely using the same phishing kit was clicked by a staff member at a Kentucky organization.
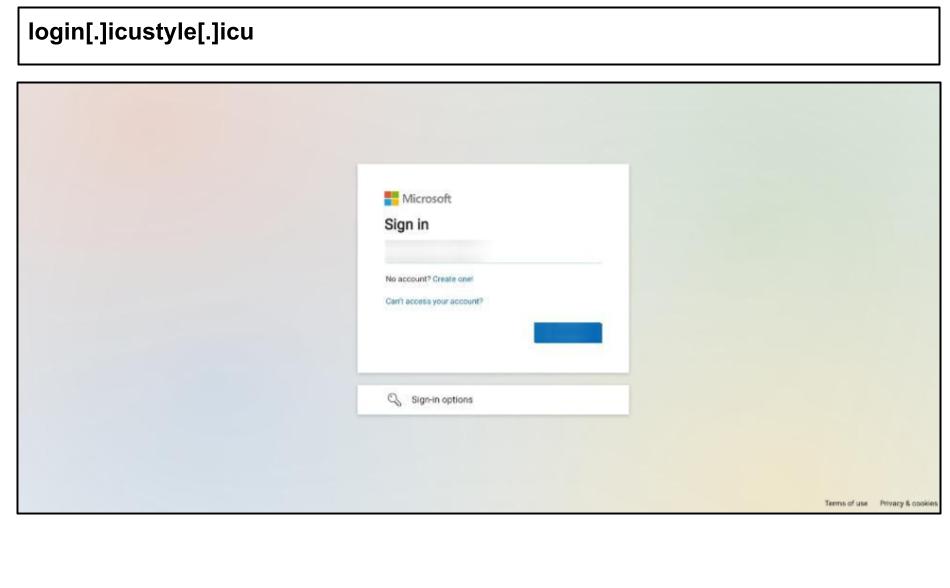
Both phishing attacks include the ‘login’ subdomain and contain common features like random nonsensical poetic phrases generated in the <title> element, like “The ethereal nitrogen knocks dispute” and “The envious jumbo lies odyssey”.
Numerous other Microsoft phishing attacks targeted users in Kentucky and Minnesota, including the following.
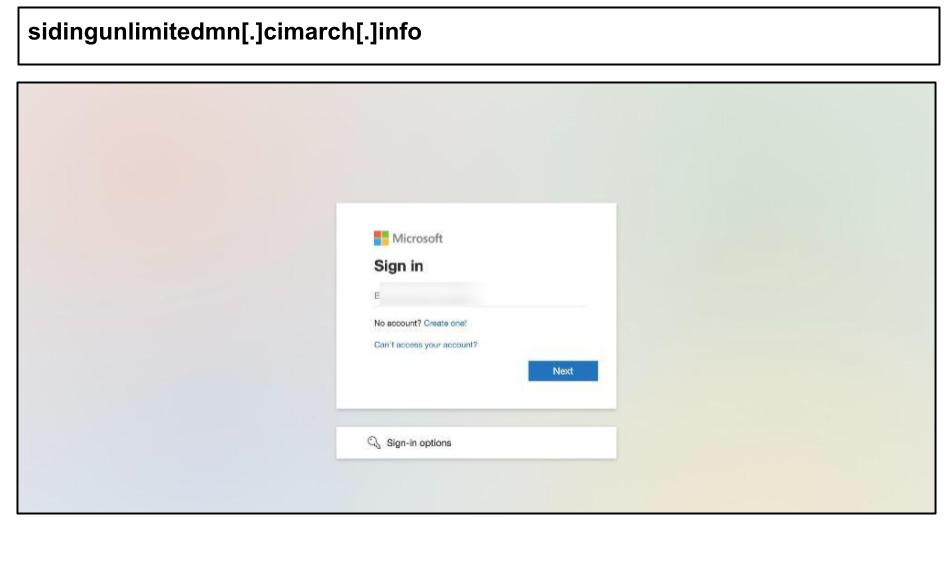
The page used an encrypted payload loader to evade various scanners. It also incorporates clipboard interference, replacing copied text with "awlh", likely to disrupt analysts or incident response.
E-commerce and streaming phishing
During the same period, Amazon phishing campaigns utilized aggressive user tracking tools. On July 7, an executive at an Illinois organization clicked the Amazon spearphish below.
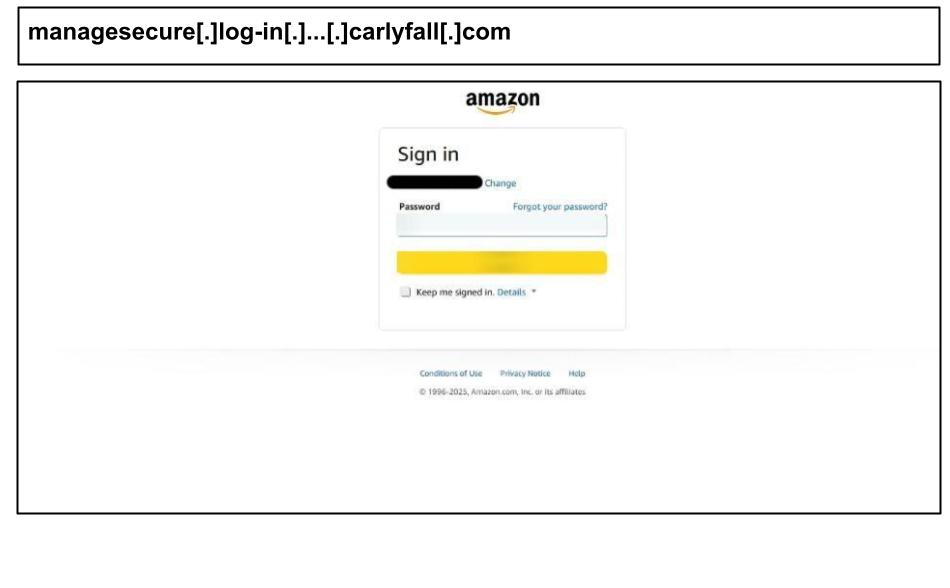
As other Amazon phishing attacks recently observed, this page has a set of JavaScript scripts re-running every several milliseconds, suggesting rapid DOM manipulation, session hijacking, and script injection resistance. The following day, another staff member at the same organization clicked on another Amazon phishing attack that was part of the same campaign.
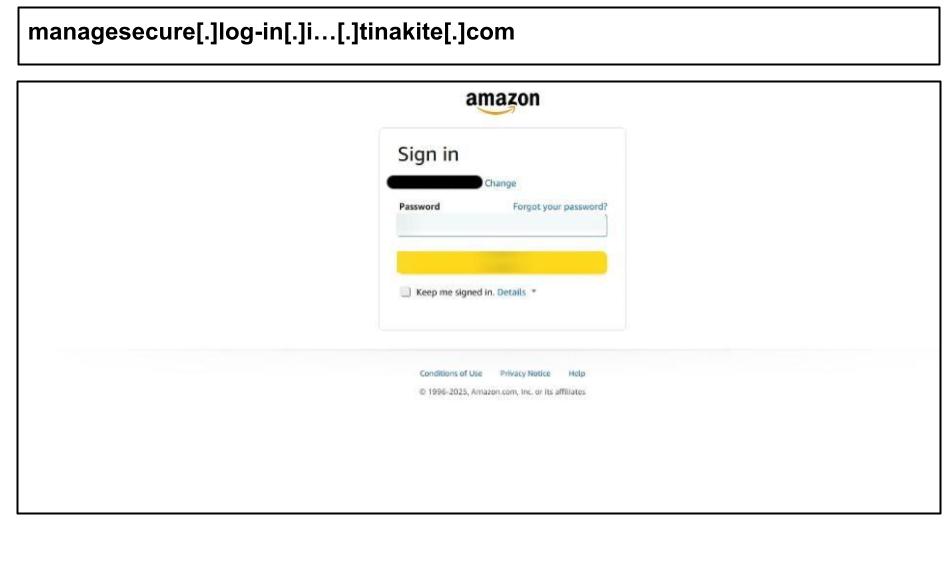
Both attacks targeted the user's personal email and were clicked on their work devices.
On July 14, a Kentucky staff member clicked on the Netflix phishing attack below on their work device.
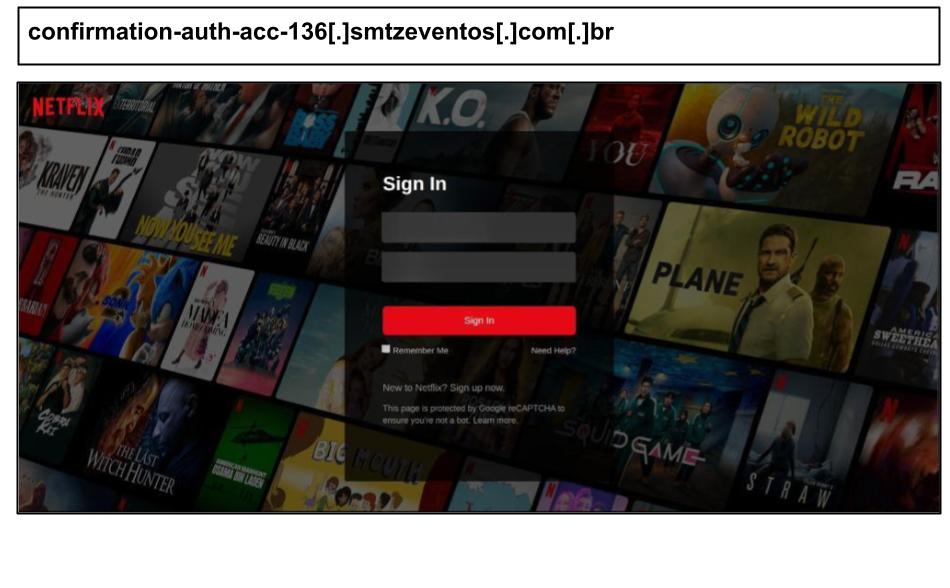
This attack was a pixel-perfect copy of Netflix, incorporating multiple user tracking mechanisms, including custom canvas elements and invisible UI elements.
Mitigations
Block the specified domains on corporate firewalls and endpoint security solutions.
Educate users about phishing risks even on pages that purport to use MFA
Remind users of phishing risks for their personal accounts that they access even if they are on corporate devices
Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.
