In the first half of May, there was a notable increase in zero-day phishing attacks that utilized highly sophisticated tactics. Beginning on April 25, attackers targeted both school email accounts (Microsoft 365/Outlook) and personal web services, including e-commerce, streaming, and personal email accounts used by employees. Many of these spear phishing pages featured multi-step login processes, fraudulent multi-factor authentication (MFA) prompts, device fingerprinting, and even used legitimate cloud hosting or subdomains to appear credible. As a result, most of these phishing links went completely undetected by traditional security vendors at the time they were clicked. Here are some examples and highlights.
login[.]advancedenergysolutionscorp[.]directory
julinvitepeople[.]es/today/AcrobatN/
upenn[.]it[.]com/index[.]html
bootynugget[.]hitremixes[.]com/a
image[.]landbfashion[.]com/index[.]html
update-billing[.]information[.]homatell[.]com
aeufiebvz[.]oeafiygyaeefn[.]130-51-180-103[.]cprapid[.]com
evitespree[.]info
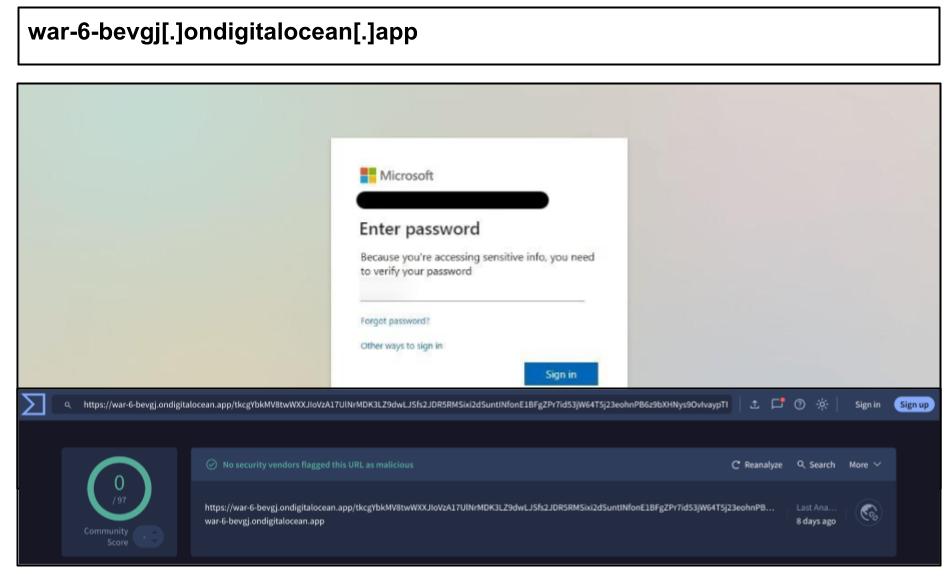
war-6-bevgj[.]ondigitalocean[.]app
h3etffphlwabwkizjrof[.]ewetanign[.]ru
Microsoft and Outlook Credential Phishing
On May 7th, a staff member at a Texas organization clicked the below Outlook spearphish delivered via an online invitation platform.
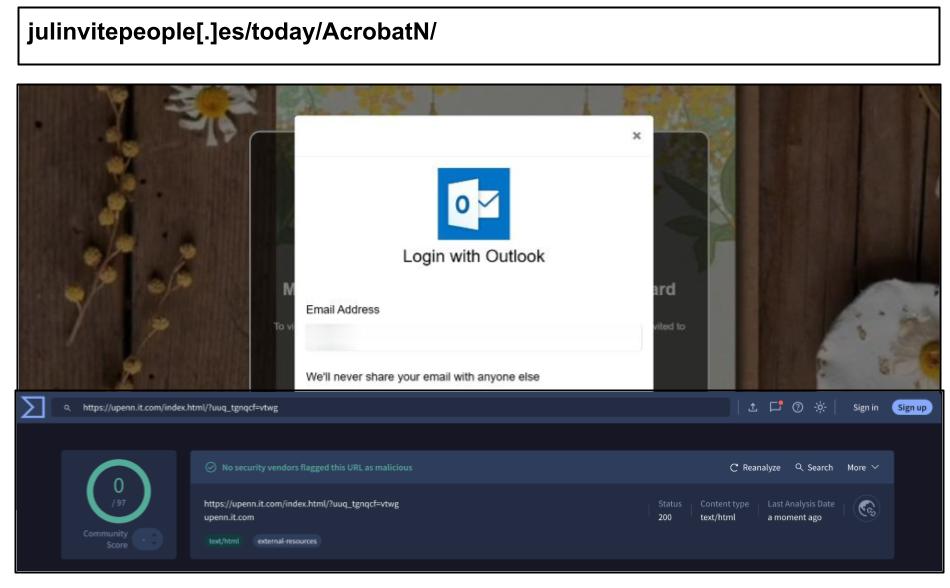
The phishing site employed a multi-step login process that included a fake OTP (One-Time Password) verification step to collect users' email credentials and bypass multi-factor authentication (MFA). The page was not limited to Outlook; it displayed logos from various brands, including Gmail and Yahoo, to capture any login information the victim entered. By using a trusted-looking event invite link and mimicking a legitimate MFA workflow, this attack successfully circumvented traditional email security measures.
On May 6th and 7th, two staff members at an organization in Idaho fell victim to a phishing scam involving an Outlook link sent through a PDF document.
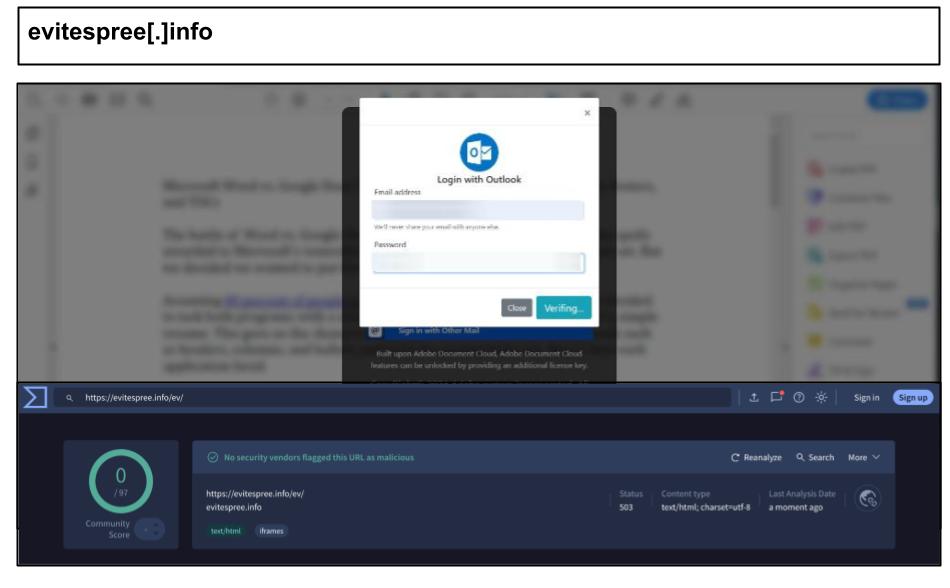
The scam involved a fake file-sharing interface that resembled Adobe or DocuSign, prompting users to log in with their email credentials to access a PDF. If the user entered their login information—often asked for twice for confirmation—the phishing process escalated. After collecting the login details, the scam redirected the victim to download a malicious executable disguised as a PDF viewer. This multi-step attack combined credential theft with malware delivery, significantly increasing the potential damage beyond just account compromise.
On April 29th, another attack targeted a Washington organization using an advanced Microsoft 365 credential harvester.
The phishing page mimicked all major MFA options. It displayed fake prompts for Microsoft Authenticator push approvals, SMS codes, authenticator app codes, and more, complete with interval polling and animated "verifying" indicators to imitate a genuine Office 365 login experience. Additionally, the site included a <noscript> fallback: if scripts were blocked or the page was loaded in a non-standard way, it would silently redirect the browser to a harmless Wikipedia page.
On May 8th, three different users at a Texas organization clicked on a Microsoft spearphishing link hosted on a deceptive subdomain, “upenn.it.com.”
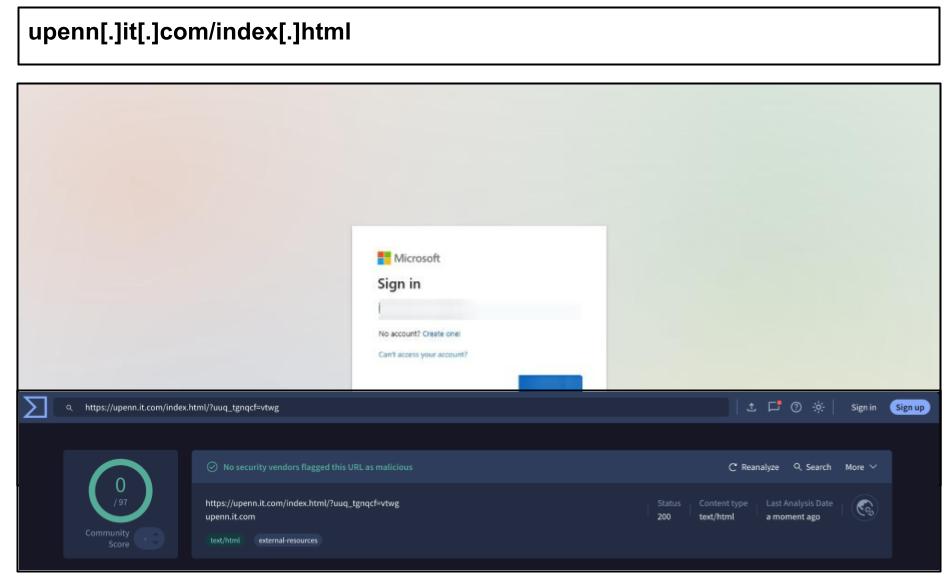
This domain masqueraded as an official University of Pennsylvania IT site, exploiting trust in a respected educational institution. The phishing site itself was extremely polished: it pulled in real Microsoft content from official CDN URLs (e.g. aadcdn.msftauth.net) to load styling and images, making the fake login page virtually indistinguishable from a legitimate Microsoft login. Additionally, hidden telemetry scripts mimicked Microsoft’s own OneDS instrumentation, likely to fingerprint the device and track user interaction in real time. Despite these novel TTPs, none of the security scanners on VirusTotal flagged the upenn.it.com phishing URL at the time (showing a 0/97 detection score), illustrating how well these attacks evaded traditional detection.
Personal Account Phishing
On May 5th, a staff member at a Texas organization was spear-phished with a Yahoo Mail account lure.
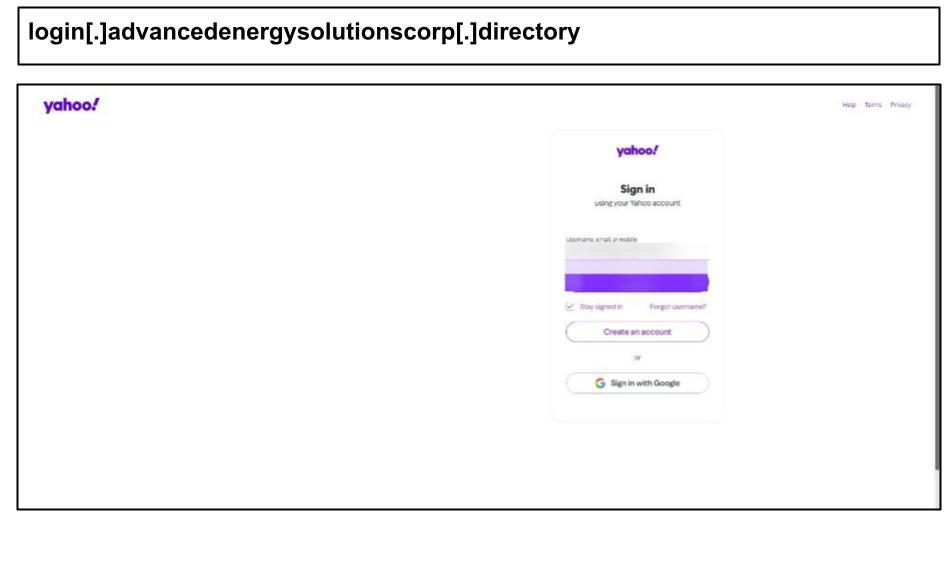
This phishing page employed several advanced evasive techniques: device fingerprinting to tailor the content per victim, per-user unique URLs (so that the link would only work once per target), and heavy obfuscation/anti-analysis scripting to prevent security tools from examining the site. All of these measures enhanced the attack’s credibility and stealth.
On April 28th, a staff member at a Georgia organization clicked on the below eBay phishing attack.
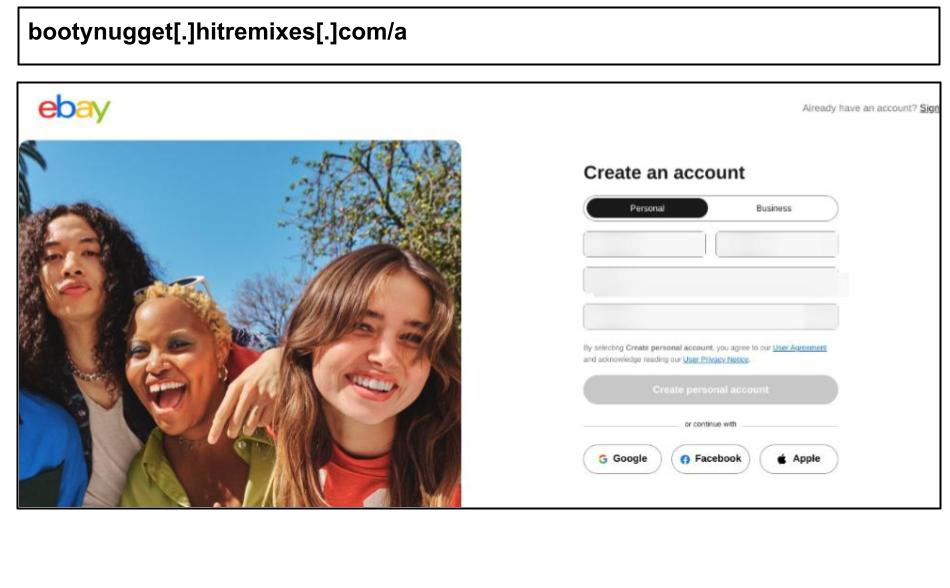
The site displayed fake “Continue with Google/Facebook/Apple” buttons, mimicking popular OAuth single sign-on options. If clicked, these buttons would likely lead the victim through a spoofed OAuth flow to capture OAuth tokens or credentials for those providers as well.
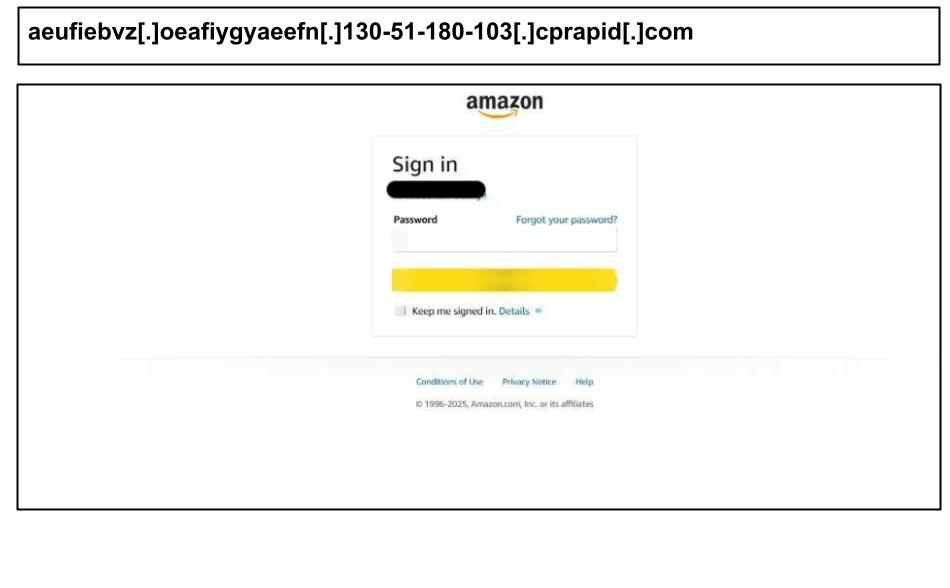
Personal e-commerce and streaming services were targeted as well during this period. On May 5th, a Georgia employee fell for an Amazon account phishing page that included a hard-coded phone number displayed on the site, likely a recycled scam number from a previous lure or breach.
Earlier, on April 25th, an HR staff member in Maryland clicked a Netflix phishing link, which prompted for the user’s Netflix credentials (likely under the pretense of fixing a billing or account issue).
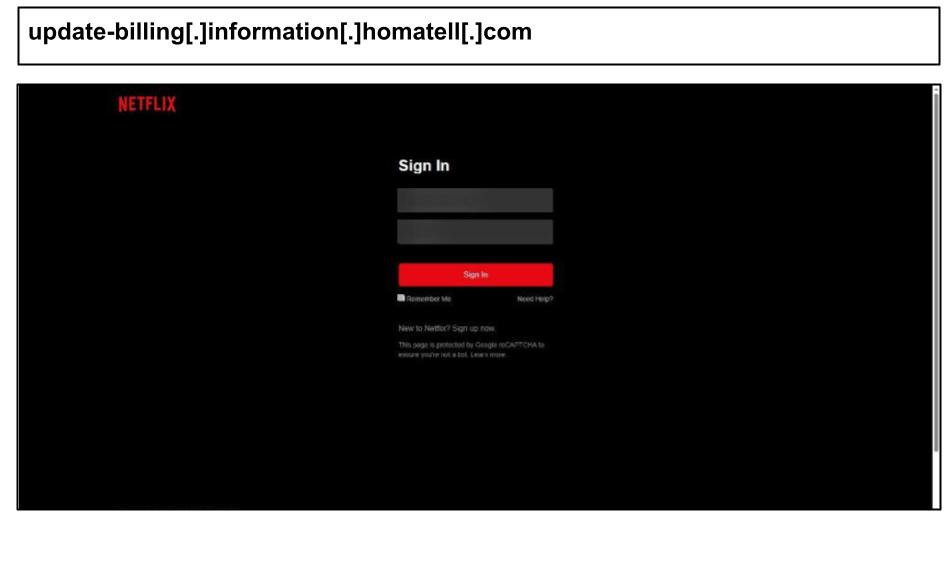
These Netflix and Amazon attacks underscore how employees’ personal services (from shopping to streaming) are being phished alongside their corporate accounts. Such attacks often occur on work devices but outside corporate email, bypassing standard security filters and relying on the user’s trust in familiar brands.
Mitigations
Block the specific phishing domains (listed above) at corporate firewalls, web gateways, and endpoint security solutions to prevent any further access.
Educate users that phishing is not just an email threat – attackers now use file shares, document services, social media, and even fake event invitations to deliver malicious links.
Remind staff that their personal accounts (webmail, shopping, banking, streaming, etc.), when accessed on work devices, are in scope for these attacks. Emphasize that a phishing page can impersonate any service, not only school logins.
Maintain multi-factor authentication (MFA) on all school accounts to mitigate damage from credential theft. While some phishing kits attempt to spoof or bypass MFA, having MFA in place still stops less sophisticated attacks and adds an extra hurdle for attackers.
