'Proxy As' Security Vulnerability Identified
A security vulnerability has been identified in the Proxy As feature in both RapidIdentity Cloud and RapidIdentity On Premise that potentially allows non-privileged users, users with little to no special permissions, to Proxy As privileged users, users with special permissions, and perform activities in RapidIdentity that require permissions that the user does not have.
For the vulnerability to occur, the privileged accounts must resolve as targets in a delegation where non-privileged users are the sources in that delegation. The delegation must also Enable the Proxy As feature. In this instance, the user with little to no special permissions can Proxy As a user with special permissions and use those permissions.
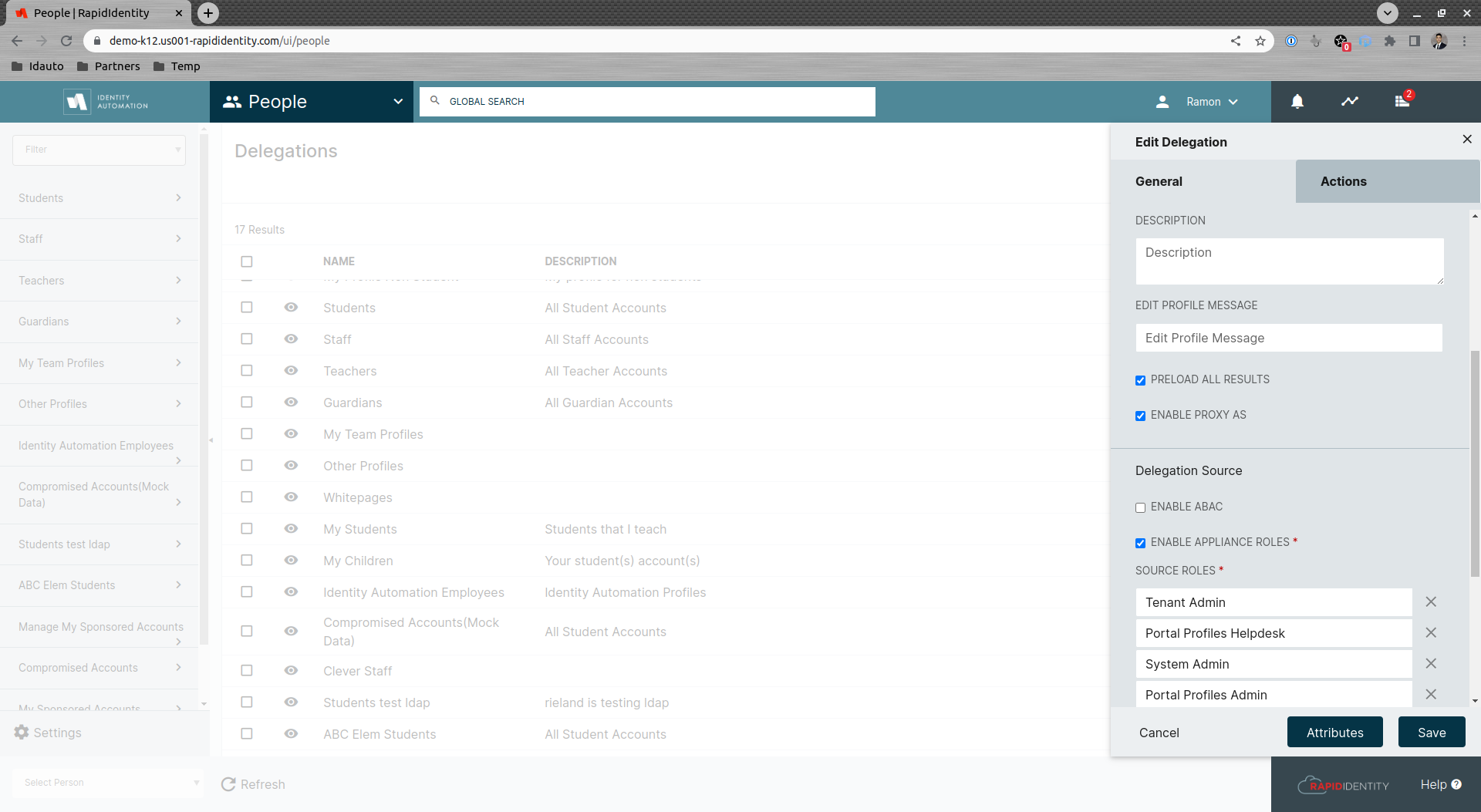
This scenario can occur when Proxy As is enabled on delegations with broad Target ACLs such as but not limited to the Whitepages delegation
To avoid this scenario, customers Must Disable Proxy As on all delegations to ensure that no user is able to proxy as another user with greater permissions.
At any time customers can also disable the Proxy As feature globally by going to the general configurations and unchecking the Enabled checkbox.
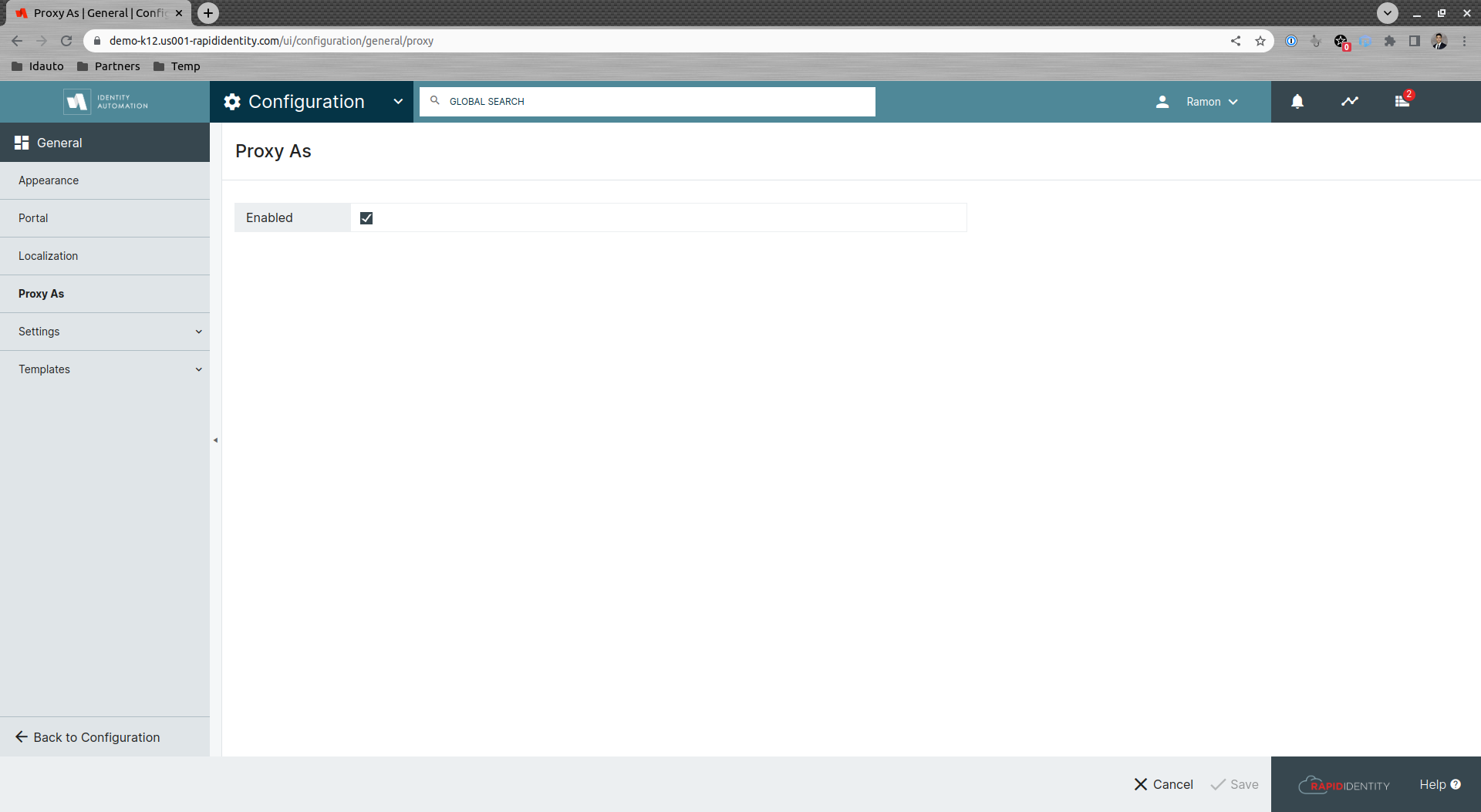
In response to this issue, Identity Automation has developed an update for RapidIdentity Cloud and RapidIdentity On-Premise implementations that removes the Proxy As option from the Profile Menu for all users except Tenant Administrators.
RapidIdentity Cloud tenants will automatically receive the update on Saturday, September 24th.
RapidIdentity On-Premise customers running the 2022.0 version can update their appliances using the following Custom Coordinates
- Filename: rapididentity-2022.0.4-hotfix1.zip
- Timestamp: 2022-09-21T22:42:27.836Z
- Checksum: 170038c186c547c580a4264cf64824b22a54183e