Windows Authentication Client Release v1.5.0 - What's New?
Support for WebAuthn - FIDO2 Authentication
Users will be able to login via the Authentication Client utilizing the WebAuthn method when they have enrolled a FIDO2 External Security Key device.
Pre-requisite Administrator Settings
In order to utilize this feature, an Administrator needs to create an Authentication Policy with WebAuthn included as an Authentication Method. Users that fall into this policy will be able to use WebAuthn to log into the RI Portal and the Windows Authentication Client using a FIDO2 External Security Key.
.png)
Note:
The Windows Authentication Client does not currently support the use of Pin Codes associated with Security Keys. If a Security Key has a Pin Code defined, the Windows Authentication Client and RapidIdentity will ignore it.
To ensure the authenticity of the user presenting the Security Key, The Windows Authentication Client and RapidIdentity requires at least one additional Authentication Method to be configured with WebAuthn.
Pre-requisite User Settings
Prior to authenticating via the Authentication Client with WebAuthn, a User must complete enrollment of their FIDO device in their RapidIdentity Profile.

Authenticating with WebAuthN via the Windows Authentication Client
Insert USB FIDO device into client machine and start WAC authentication by entering your Username.
.png)
Select the WebAuthn Authentication method, as shown below.
.png)
If the User has a single external device enrolled, authentication will immediately proceed. Once their device starts blinking, they should tap on device to complete authentication.
.png)
If a User has multiple devices enrolled, they will be prompted to select the appropriate device from a drop-down menu. Once selected, click the arrow to start the authentication process.
.png)
.png)
Once user start authentication device starts blinking, tap on device to complete authentication.
Once a User has authenticated successfully with WebAuthn/Fido, they will then be prompted to authenticate with other available authentication methods.
.png)
A few important notes regarding utilizing this feature:
Fido with MFA is the only option available for WAC users to authenticate through WebAuthn.
Using the Device Tab feature in WAC is the only way to use Fido authentication.
WAC does not offer support for password recovery with WebAuthn FIDO authentication.
FIDO will not perform Account Lockout in WAC.
Support for Disconnect/Offline Desktop Access using Password
With the v1.5.0 Release, devices with the Windows Authentication Client installed will now be able to login with a Password when the device is offline.
Please follow the given steps for the process:
Sync RI users with your AD Server.
Authenticate user at least once with any RI authentication method when client machine is connected with network and AD server is available. This process makes the Password Cache in Windows machine.
Disconnect your client machine from the internet, or switch off AD Server, or Both.
To start authentication enter username.
.png)
5. The user will encounter the tile for Password authentication method. Clicking on this tile will prompt them to enter their password.
.png)
6. After entering their RapidIdentity password, the user gains access to the desktop and is logged into the client machine.
A few important notes regarding utilizing the Offline Access Feature:
For Domain-join users:
To disable credential caching by using a GPO setting, enable the "Interactive logon: number of previous logons to cache (in case domain controller is not available)" setting. To utilize Offline Access we recommend the value for CachedLogonsCount in the Registry Key should be set to this value should be >0 and <=10. Cached logon information is controlled by the following Registry Editor (Regedit.exe)key:
Location:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Value name: CachedLogonsCount
Data type: REG_SZ
Expected values (turn on logon cache): 1 - 50
Value to turn off logon cache: 0
Default Value: 10
Any changes you make to this key require that you restart the computer for the changes to take effect. Windows provides a valid range of values for domain user password cache from 0 to 50. A value of 0 turns off logon caching and any value above 50 will only cache 50 logon attempts. By default, all versions of Windows remember 10 cached logons except Windows Server 2008. Refer Microsoft Documentation to know more about Cache logon count Registry Data:Cached domain logon information - Windows Server
Domain-join & Non-Domain/Local users
WAC provides offline desktop access using only Password Authentication Method.
To use the offline desktop access feature, it is necessary for the WAC user to log in to the client machine once while they are networked.
To perform offline desktop access in WAC, users must sync their AD and RI passwords every time they change their password.
Notable Issue Resolutions
User Account Claim is now supporting user defined questions
Previously, a user attempting to claim their account through the Windows AuthClient was not able to successfully claim their account using user defined questions or help desk questions This has been resolved, and Users can claim accounts using both user defined and help desk questions.
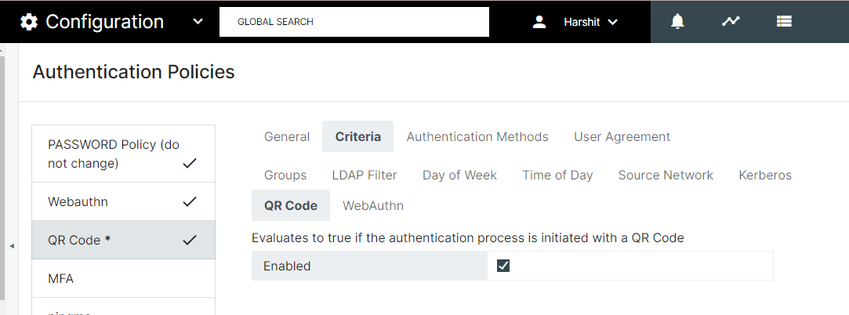
QR Code Authentication Policy Error Message
Users attempting to authenticate with a QR code into the AuthClient was receiving an error message, if QR Code Authentication Policy had Criteria is enabled. This has been resolved, and will no longer block the authentication process.
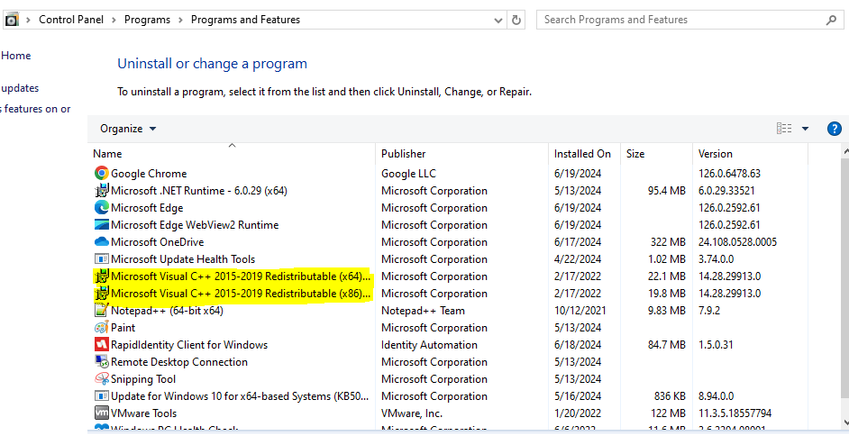
Windows Installation Issue
Affected version: 1.3.0 and above. Users reported attempting to login through the AuthClient with correct credentials, but not being successful. The issue was rooted in the proper package during WAC installation has not installed. The solution has ensured that the installers highlighted in the image below will be installed in client machine.
Forgot Password with Duo, SMS and TOTP not working in some scenarios
The Forgot Password button in WAC is disabled under certain conditions when an admin adds a policy for user password recovery and assigns methods like Duo, SMS, or TOTP. These scenarios are detailed below (see screenshots below for reference):
When the admin configures a Forgot Password policy with a single method such as Duo, SMS, or TOTP.
.png)
.png)
.png)
When the admin configures a Forgot Password policy with multiple methods, and Duo, SMS, or TOTP is listed as the first method in the authentication method sequence.
.png)
.png)