Release 2023.05.0 - What's New
RapidIdentity Cloud has received numerous updates with the 2023.05.0 release with exciting new features, enhancements to existing capabilities and resolutions to customer issues.
Notable Enhancements and New Features:
Password Policy Enhancements featuring Auto Account Lockout
With the 2023.05.0 release, you will see the benefits from a couple of security enhancements that have been built into the Authentication and Password Policies.
-
Exponential Backoff
A malicious user may attempt to gain access to accounts in your District by means of a dictionary attack using a script to automatically attempt to login as a user and using a dictionary list to test all possible passwords.To mitigate dictionary attacks, a new Exponential Backoff feature automatically increases, exponentially, the delay between repetitive login attempts. This feature will automatically apply to all users and authentication methods enabled in your tenant to provide protection against such an attack.
-
Account Lockout
Another Enhancement, Account Lockout Policy, can be found under Configuration > Policies > Password from your Administrator account and enables you to control the number of unsuccessful user authentication attempts allowed within a specified amount of time before automatically locking the user's account for the specified amount of time.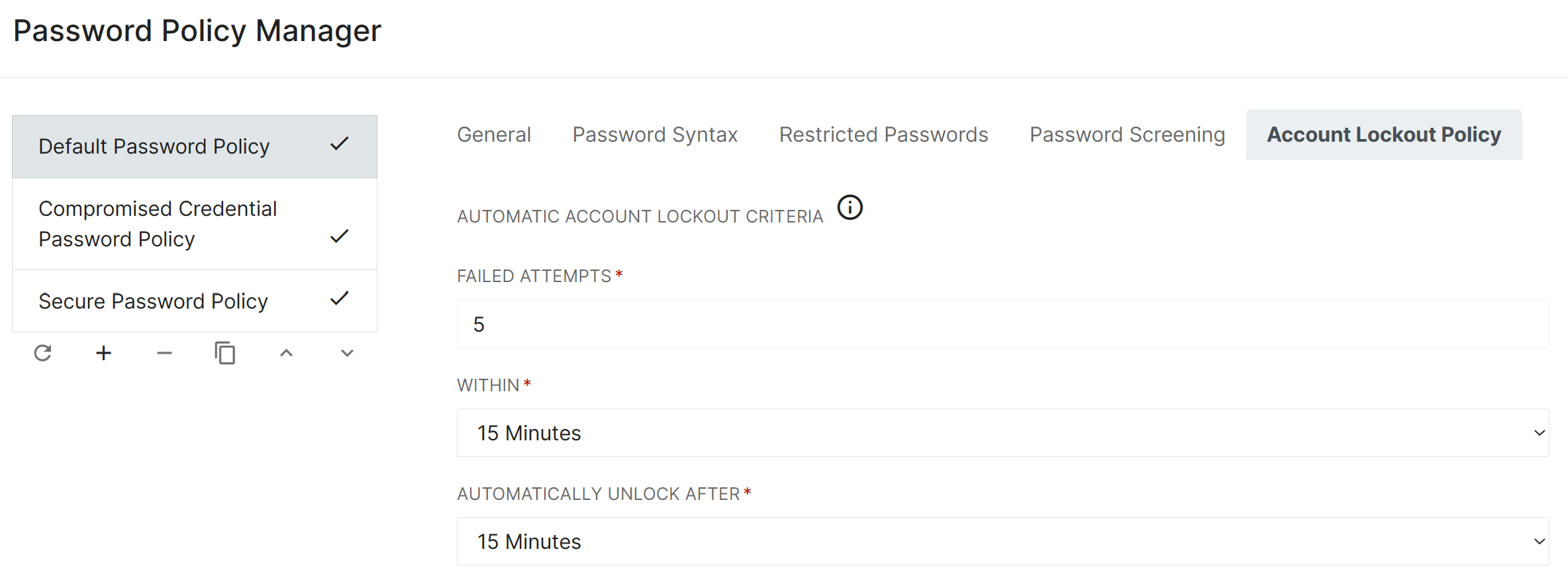
The criteria set under this tab will affect all Users that fall under this Password Policy, and will determine if and when an automatic lockout of an account will occur based upon attempts in a specific length of time.
You can also specify how long a user will be locked out of their account before it is automatically unlocked. Selecting ‘Never’ under ‘Automatically Unlock After’ will force the user to remain locked out until an Admin Manually unlocks their account.
Note:Although Account Lockout is associated with and configured on a Password Policy, the lockout function applies to all types of unsuccessful user authentication attempts in RapidIdentity, not just unsuccessful password authentications.
Supporting the new Account Lockout Policy, RapidIdentity People has a new Account Lockout system delegation in the People module which will be visible to users in the System Admin, Tenant Admin, District Admin, District Manager, Portal Help Desk, and/or Portal Admin system role.
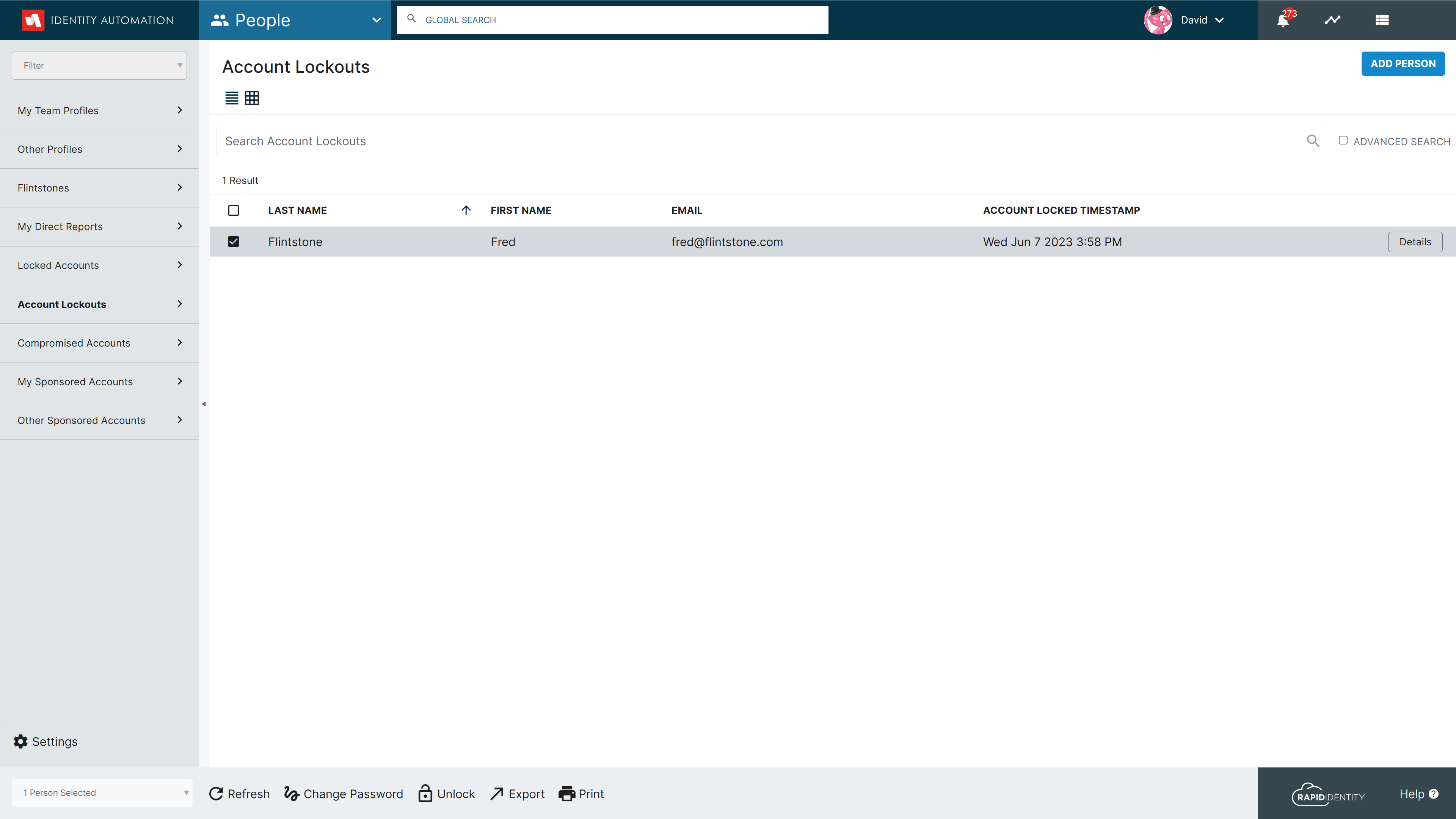
For more details regarding these Password Policy Enhancements, please refer to the Password Policy Enhancement - What's New? article.
Studio Enhancements
In the 2023.05.0 release, you will notice a couple of Studio User Interface enhancements.
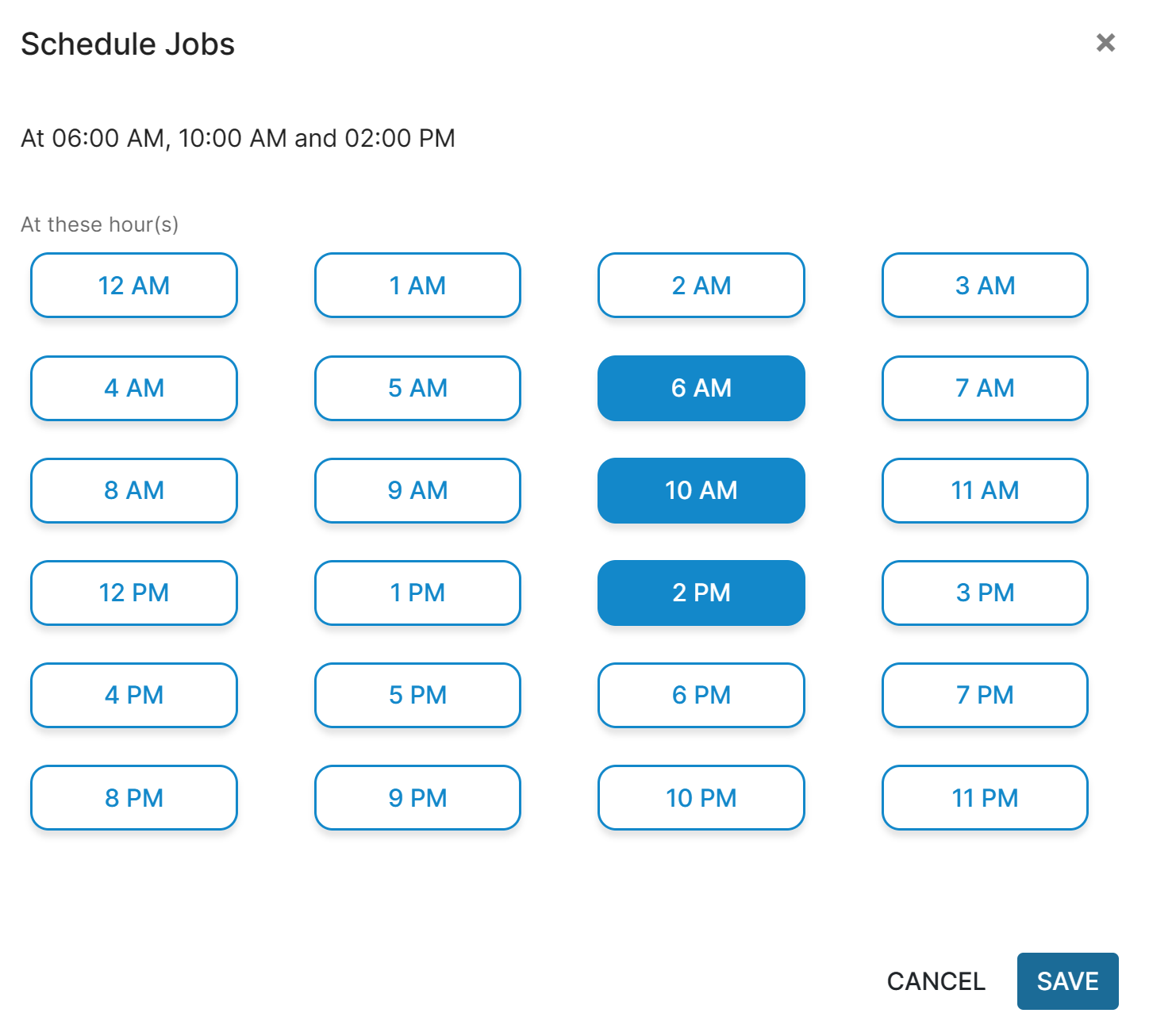
The Job Scheduler has been updated to be more streamlined and simplified. As a Studio Administrator, you will now be able to select multiple times for the sync to run during the day in a pleasing User Interface. Each of these times will be on the hour, but can be run as many times as desired.
Another modification made to the Studio UI is the alignment of terms with other components of RapidIdentity. Previously, Applications were referred to as ‘Provider’ and ‘Consumer’. We have updated these terms to ‘Source’ and ‘Target’ which is consistent throughout RI, and more representative of the purpose of the Application.
A second update towards alignment of terminology is the modification and relocation of ‘IDHub’. This tab provides advanced configuration of internal record and field definitions for imported data and has been relocated under ‘Advanced Settings’ with an updated title of ‘Data Schema’.
Lastly, the database behind Studio was previously referred to as ‘IDHub’ in the UI. We have now retitled this to ‘Studio’, and this is reflected in the Data Explorer Drop Down Menu.
Support for ROPG added to OIDC Federation (Jamf Connect Federation Partner)
Building on the OpenID Connect Federation services available in RapidIdentity, we have added support for Resource Owner Password Grant (ROPG). This is particularly exciting for our Districts who utilize Jamf Connect.
By leveraging both Jamf Connect and RapidIdentity, school districts are able to provide a universal authentication experience across all devices: Windows, Chromebooks, Macs, and iPads. The integration between RapidIdentity and Jamf Connect enables zero-touch deployment of iOS devices and provides iOS users a Single Sign-on experience across all devices and applications.
For more details on how to configure Jamf as a Federation Partner in RapidIdentity, please see the links below:
New Connect Actions for Version Updating, User Passwords, and Disabling Accounts
The new Connect Actions listed below were created in conjunction with the Password Policy Enhancements that are also included in the 2023.05.0 Release.
- ActionVersionSupport
- getRapidIdentityVersion() - returns the current version of RI as the result (return a string)
- ActionPasswordUpdate - implements ActionPasswordUpdate or directly calls AccountPassword implementations if the signatures and desired functionality are present in that implementation (password validation, history checking/storage, etc.)
- adminPasswordReset() - allow setting a user's password without needing to provide the current password - validates that the password complies with the policy for that user and returns an error if it doesn’t.
- ActionAccountStateUpdate
- isAccountDisabled() - allow connect actions to test if an account is disabled (Will take a dn as a parameter and return boolean)
- isAccountLocked() - allow connect actions to test if an account is locked (Will take a dn as a parameter and return boolean)
- unlockAccount() - allow connect actions to unlock the account (Will take a dn as a parameter and return boolean)
- DisableAccount() - allow connect actions to disable a user account without needing to know the backing attribute in LDAP that is presently used (Will take a dn as a parameter and return boolean)
- EnableAccount() - allow connect actions to enable a user account without needing to know the backing attribute in LDAP that is presently used (Will take a dn as a parameter and return boolean)
Update Password Validator to account for Account Status Tracking
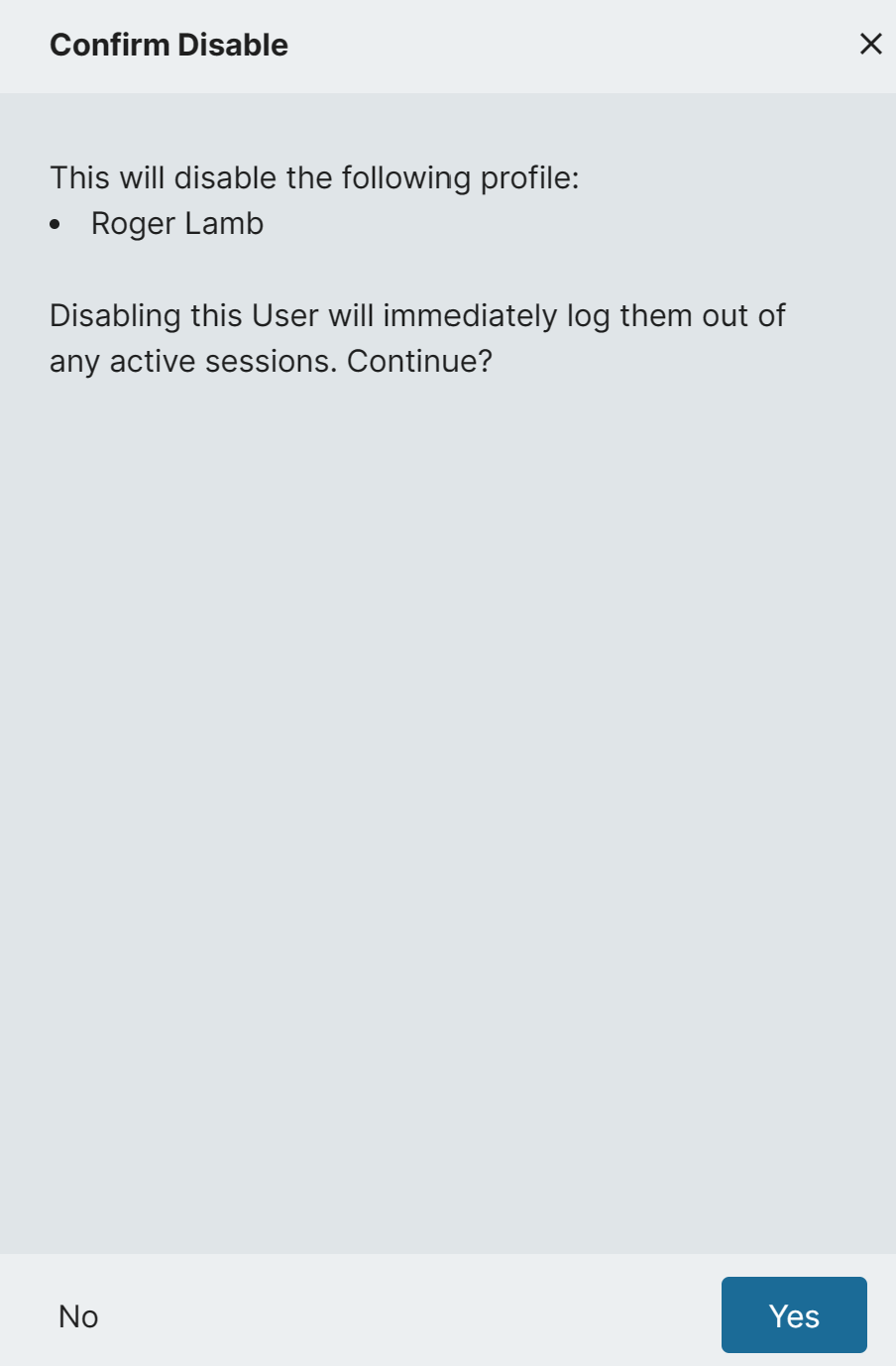
When an Admin disables an account from the People Module, they will now see a message in the sidebar warning them that this action will log that user out of any active sessions.
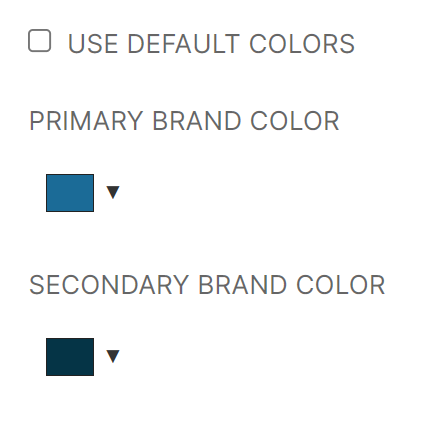
Updated Default Colors and Default Logos in Portal:
Beginning with the 2023.05.0 release, new RapidIdentity tenants will be created with new Identity Automation brand colors as the default. All customer tenants will be updated with new default Identity Automation logos.
Both the default brand colors and default logo updates only apply to customer tenants that have not configured their own logo or color settings.
Affective with the 2023.05.0 release, tenants created with or after this release will have the following default colors:
-
Default Primary Brand Color, #1B6B97, is used in the Module Selector area in the Page Header and Primary Buttons

-
Default Secondary Brand Color, #053446, is used in the Logo, Search and Profile areas in the Page Header

RapidIdentity Tenant Administrators can still set their own Primary and Secondary colors under Configuration > General > Appearance and un-checking the Use Default Colors selection box
Also affective with the 2023.05.0 release, all RapidIdentity tenants will have updated, default, Identity Automation and RapidIdentity Cloud logos:
-
Default Wide Logo

-
Default Narrow Logo

-
RapidIdentity Cloud Logo

-
Only RapidIdentity tenants created with or after 2023.05.0 have the updated default brand colors. RapidIdentity tenants created before the 2023.05.0 release will continue to use the previous default brand colors.
-
All RapidIdentity tenants will have updated default Identity Automation wide and narrow logos as well as the updated RapidIdentity Cloud logo.
-
RapidIdentity Tenant Administrators can configure their own wide and narrow logos and primary and secondary colors.
Role Sync Scheduler Enhancements
Previously, Role Syncs were scheduled using an interval timer. This interval would restart whenever the sync was run, either manually or automatically, and this could cause the syncs to run at unexpected times. Feedback was provided that it would be preferable to be able to schedule the sync at a specific time instead, so it would be consistent.
We have implemented an enhanced Role Sync Scheduler that provides the capacity to schedule a sync at a specific time or multiple specific times during a day. These scheduled syncs will not be affected by a manual sync, and does not remove the ability to run a manual sync when needed.
Current sync schedules will be translated into the scheduling format, and should not be impacted negatively. You will be able to update the Role Sync Schedule using the enhanced capabilities as you see fit.
Portal Navigation Enhancements:
Added kebab menu and context menu support to Configuration (SSO Portal, System, and Security), Roles, and the Reports Module to improve useability.
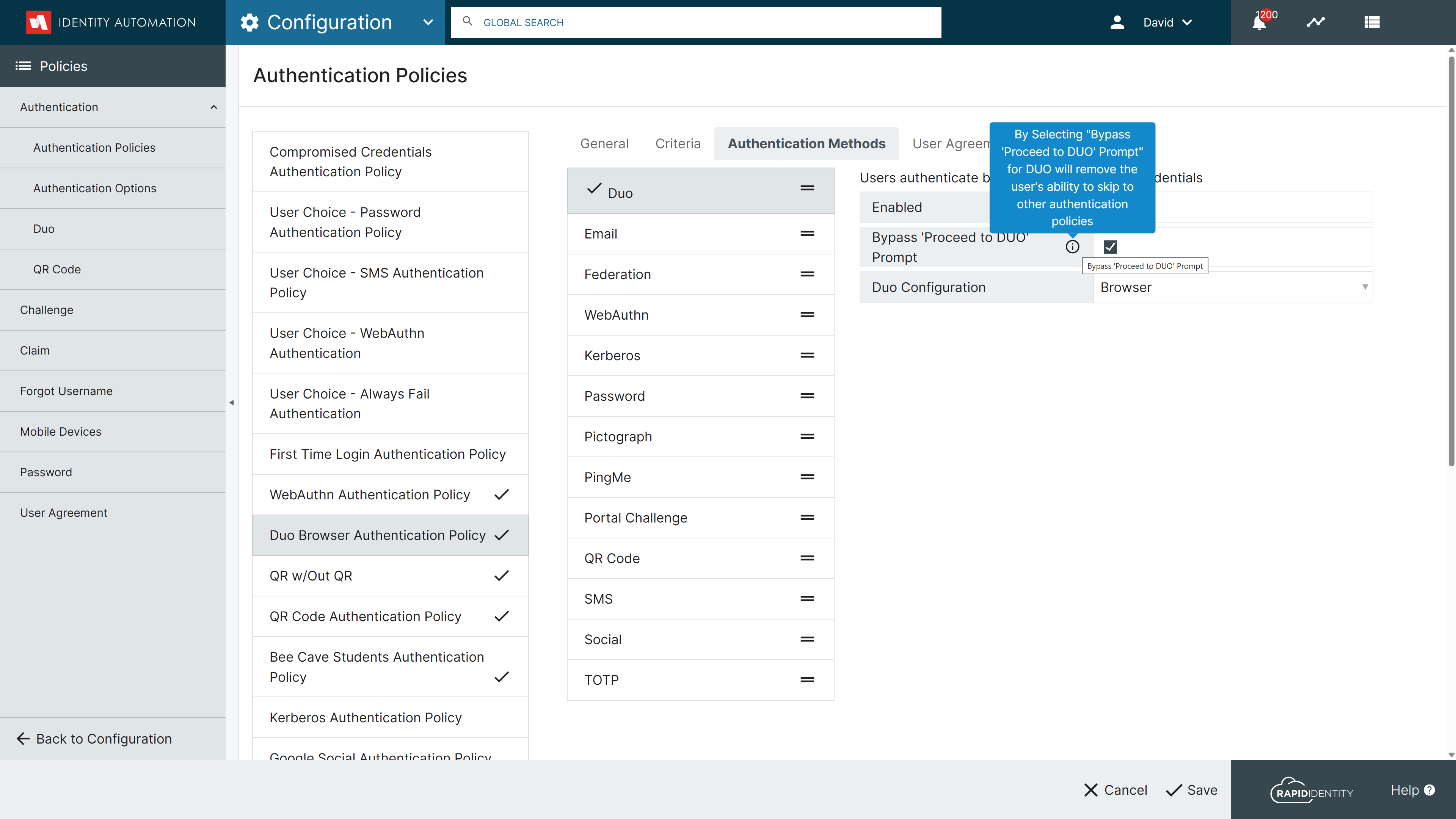
Enhanced Integration with DUO Universal Prompt:
Added option to Bypass "Proceed to Duo" to the DUO configuration in Authentication Policy setup, so administrators can have more control over the user experience when using DUO Universal Prompt as an authentication method.
Security Modification for External Application Launches
When you want to link to an external page from your app, it is very common to use </a href="url" target="_blank"> to make the browser open this link in a new tab. However, this practice has performance problems and also opens a door to some security attacks because the opened page can redirect the opener app to a malicious clone to perform phishing on your users. Adding <rel="noopener noreferrer"> closes that door and avoids javascript in the opened tab to block the main thread in the opener.
SSO Portal Renamed to GO! View:
The SSO Portal configuration area in Portal has been renamed GO! View to reflect the relationship between Personas and the RapidIdentity GO! iOS application for iPhone and iPad devices.
Ability to reuse User Agreement Titles
Previously, when an admin attempted to reuse a User Agreement Title, they received an error message that this title was not unique and could not be saved. This is now resolved, and User Agreement Titles can be reused once the original User Agreement is deleted.
SafeID Scan Summary Reports Enhancement
If a user’s account is compromised (has a value idautoPersonSafeIdCompromisedDate attribute) and is deleted from the directory, the SafeID scan summary email will no longer account for the user when reporting the number of compromised accounts.
We have also added a 'processed' field to 'CompromisedAccounts' so that records are not processed multiple times from a single scan. These enhancements will ensure that compromised users will only appear in the Summary scan for the week they are identified.
Additional Information Displayed on Request Approval Task Card
Additional information has been added to task notification cards for Entitlement Requests. With this enhancement, the following details will be visible so Administrators will have the information necessary to approve/deny the request without opening the request.
Entitlement Type
Requestor has requested Entitlement Name for Target in OU/Group.
This request will expire in Entitlement Request Expiration
Approve or Deny
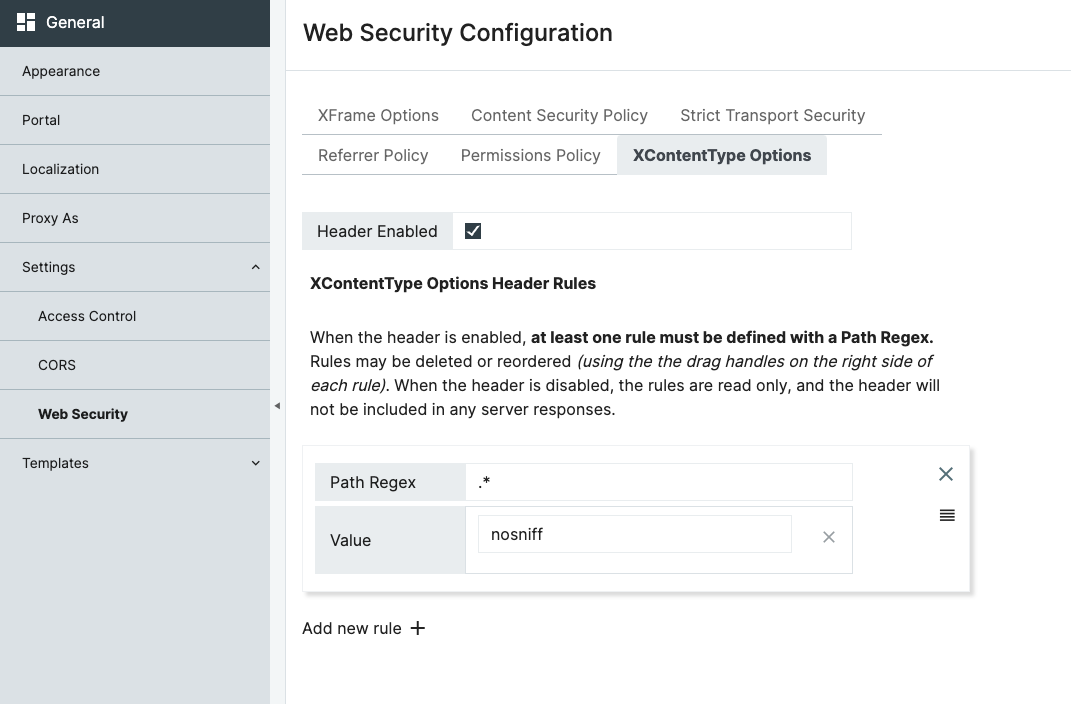
Web Security Configuration Updates to Improve Security Rating
We want to implement a strong Content Security Policy (CSP) significantly to reduce the risk of cross-site scripting (XSS) attacks. To support this effort, we have added a series of HTTP Response Headers to ensure we receive the highest security rating. These HTTP Response headers are enabled by default, and can be viewed and modified under Configuration > General > Web Security.
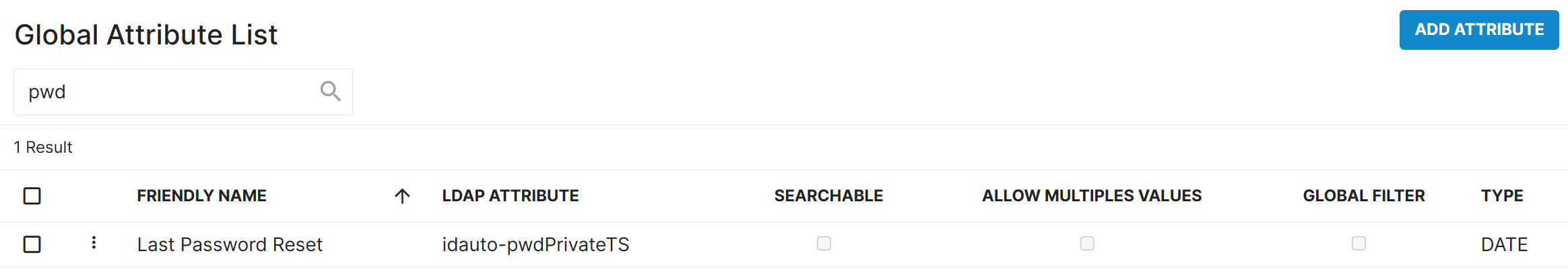
Directory Updates
-
Added the Last Password Reset date attribute to the directory so it can be displayed in delegations.
-
Added Preferred Name and Preferred Last Name attributes to the directory.
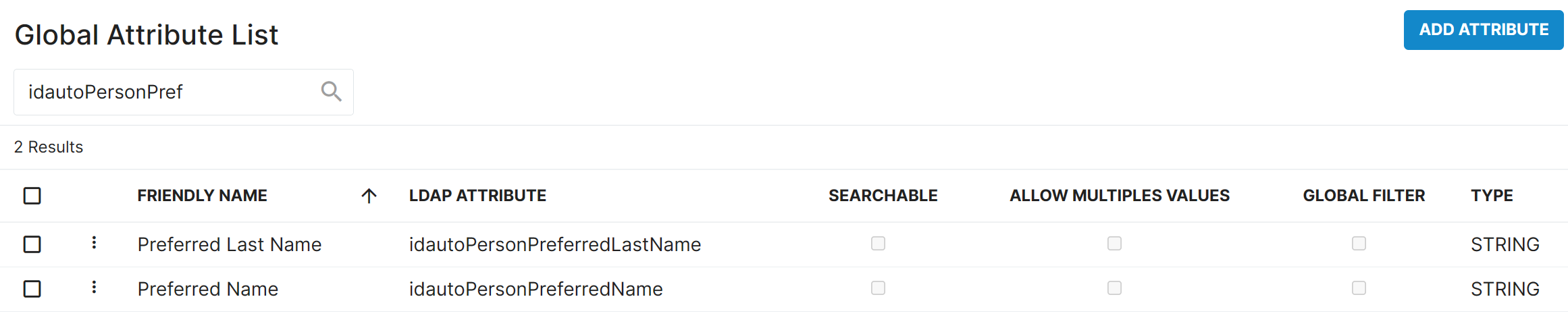
Improved Self-service Password Reset
When performing a self-service password reset in RapidIdentity, users are required to input their current password and choose a new password that complies with an associated password policy. Within the core self-service password reset process, RapidIdentity then validates the password provided by the user against the user’s actual password and, if valid, updates the password accordingly.
However, if RapidIdentity is configured to use a Connect Alternate Change Password Action instead of it’s core processing, often times used to provide custom processing required by the institution, RapidIdentity passes the user provided password and associated password policy information to that Connect Alternate Action to process in conjunction with it’s custom logic.
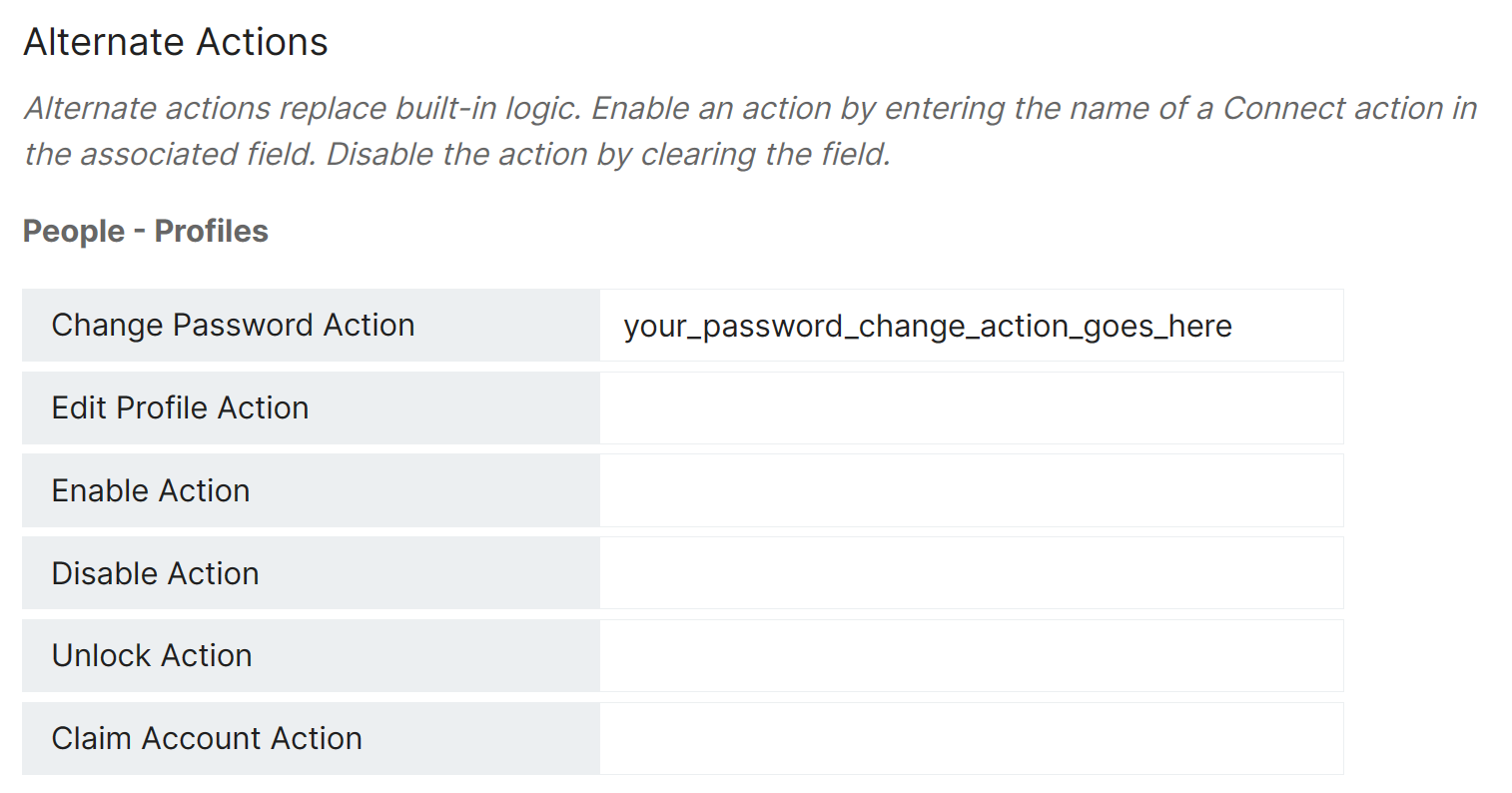
Administrators can configure and/or update Alternate Actions at Configuration > Systems > Integration > Connect
To ensure that password validations are performed consistently, RapidIdentity has been updated to perform the same validation and compliance checks during all password reset actions regardless of an Alternate Change Password Action being present.
No customer actions are necessary for this enhancement.
Identity Automation has verified that Connect Alternate Change Password Actions currently used in RapidIdentity Cloud systems perform the proper password validation prior to updating user passwords.
While this enhancement negates the need for those password validations, it does not impact them and, it assures the continued validation of passwords for new and/or modified Alternate Change Password Actions in the future.
Significant Issues Resolved
-
Layout issue Printing QR Codes on Avery Labels Resolved
- In an earlier release, it was observed that there was an issue with the layout matching up with the Avery Labels during printing. This issue has been resolved, and now the QR Codes will print properly on the Avery Labels regardless of the browser being used to generate the codes.
-
Error Occuring during Workflow Approval Tasks Resolved
-
Manager Team Entitlements Visibility
- As a Manager with Direct Reports, the “Team Entitlements” tab(accessible via the left hand navigation bar) will display any entitlements that exist for their direct reports.