New Features and Notable Enhancements
Mobile Device/Small Screens UX Improvements
With this release, users can now expect improved responsiveness in GO! View and Enterprise View for devices with smaller screen sizes. There are two themes for the implemented improvements. The first is focused on the Profile and Profile Menu screens. On mobile devices with smaller screens, the updated experience will feel more native to the user. Examples of the enhanced screens can be seen below.
The second focus for the implemented enhancements is improving the accessibility of the context menus in the GO! View. Various mobile device environments have different methods of accessing the context menus, which can affect the user experience. The GO! View is now able to detect the environment and provide an environment specific experience that is customized for that device.
The GO! view will show kabob menus when accessed on a small screen, that can be accessed to provide full functionality of the Home Screen. Here are example of where these context menus will be visible on mobile devices:
Environment Specific Context Menu Triggers
Windows/Linux/Mac/ChromeOS Browsers: Right Click or Context Menu button on Keyboards will work as before and will trigger Context Menu.
iOS/iPadOS: Kebab icons will appear and clicking on them will trigger Context Menu.
Android OS: Long press generally triggers Context Menu but can be handled with Mouse or Keyboard connected to the phone as well.
Enhanced Application Creation Workflow to Include Personas
In an effort to streamline the Application Creation workflow, Administrators now have the ability to assign a Persona to a newly created application in one place. Previously, Administrators needed to navigate to the Personas Configuration page, but that is no longer needed.
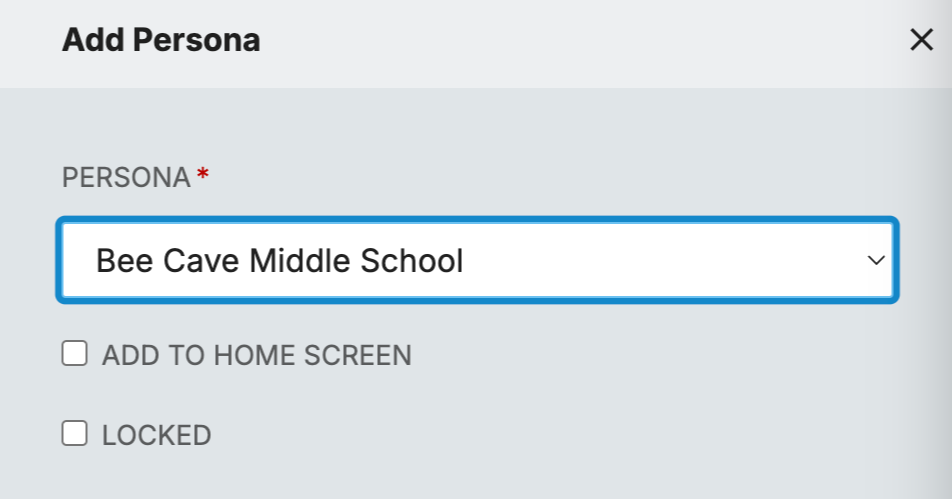
When creating a new Application, Administrators will now see a Personas section in the side menu. To add that application to a persona, click on the ‘Add Another Persona’ tab to open the ‘Add Persona’ menu.

The ‘Add Persona’ menu includes a dropdown that will list all of the current Personas that exist in your tenant.

Once a persona is selected, the options to add that application to the home screen or to lock the application on the home screen will be provided. The options selected will apply to that persona only.
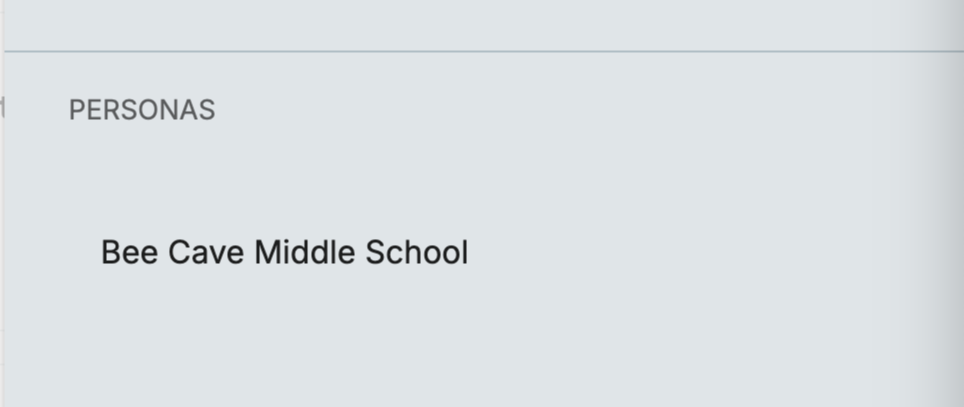
The personas an application is assigned to will be listed in the Details menu of the application.
To add multiple personas, click the ‘Add Another Persona’ tab.

All personas that an application is assigned to will show in this list, including those applications previously attached.
Password Vault Enhancement: Administrator Provided Credentials


In the 2024.10.0 Release, a new option has been included in the Password Vault credential sources. With ‘Admin Provided’, administrators now are able to manage credentials for third-party applications securely, offering the following features:
Delegated Credentials per Application:
Admins can assign specific credentials for each application link.
User IDs and passwords are defined by admins and are hidden from end users.
Granular Assignment:
Credentials can be assigned to individual users or groups for specific applications.
Visibility Control:
Delegated credentials are visible only to System, Tenant, and Application Admins—not to Help Desk or Delegation viewers.
Flexible Assignment and Cloning:
Applications with delegated credentials can be assigned to different users/groups or cloned with distinct credentials for separate groups.
Encryption:
Passwords are encrypted in the database for security.
Note: Requires the installation of the RapidIdentity Password Vault Extension to utilize this feature. To learn more, please click the following links:
New Password Policy Controls
Designed to simplify password maintenance for all users without compromising account security, a new Administrative Password Policy Override Password Policy setting has been added that enables delegated password resets to bypass all password policy restrictions while requiring the user to reset their password during their next login. With this new setting, password policies can be configured to leverage information that’s known by users when their password is reset for them without requiring that information to comply with the syntax and complexity of the user’s associated password policy’s restrictions.
.png)
Note:
The new Administrative Password Policy Override setting is mutually exclusive with the existing Administrative Password History Override setting and, when enabled, users will be forced to reset their password during their next login after a delegated password reset, there is no ability for an administrator or delegate to change that behavior.
The Administrative Password Policy Override overrides all Password Policy restrictions, this includes password syntax, specific words or characters and screening for leaked passwords. However, if SafeID is enabled, password values will still be checked to ensure they do not match known compromised passwords.
Compromised Passwords:
Compromised passwords, passwords that have been found in data breaches by SafeID credential monitoring, if licensed, will be checked to ensure that the user’s password is not reset to a previously compromised value. Attempts to reset a user’s password to a compromised password value will return an error message indicating that a different password value must be provided.
To provide greater flexibility and control over when User Must Change Password at Next Login, two additional Password Policy settings have been added to Force Password Reset Default and Hide Force Password Reset that can be enabled to show or hide the User Must Change Password at Next Login checkbox from the delegate when they are resetting a user’s password.
.png)
FORCE PASSWORD RESET DEFAULT defines the default value for the User Much Change Password at Next Login checkbox that is displayed in the modal when a delegate resets a user’s password. When this toggle is enabled, the checkbox will be pre-checked when the reset password modal is displayed to the delegate. If Hide Force Password Reset is also enabled, users will be required to change their password when they login after a delegate has reset their password. Delegates will not have an option to change that behavior. This toggle is automatically enabled when Administrative Password Policy Override is enabled and cannot be changed unless Administrative Password Policy Override is disabled.
HIDE FORCE PASSWORD RESET determines whether the User Must Change Password at Next Login checkbox is displayed in the modal when a delegate resets a user’s password. When this toggle is enabled, delegates will not have the ability to control whether a user must reset their password during their next login. This toggle is automatically enabled when Administrative Password Policy Override is enabled and cannot be changed unless Administrative Password Policy Override is disabled.
Significant Issue Resolutions
Multiple Studio Access Group Filters
Flawed 'Strictest' Password Policy Evaluation