- 07 Aug 2025
- 3 Minutes to read
- Print
- DarkLight
Phish Wire - August 7 2025
- Updated on 07 Aug 2025
- 3 Minutes to read
- Print
- DarkLight
Phishing attacks targeting users on work devices continue unabated throughout the summer, especially as many employees take their laptops home during vacation months. In the second half of July, there was a noticeable increase in spear phishing campaigns focused on Microsoft and Outlook.
These attacks showcased various sophisticated tactics, such as multi-factor authentication, phishing kits, and phishing content distributed across multiple trusted CDN servers. Additionally, this period saw a rise in phishing pages aimed at consumer banking services like Bank of America and American Express. The MFA phishing attempts included methods to capture SMS verification codes as well as codes from authentication apps. Below are some examples and highlights of these activities.
cure[.]ru[.]com/Gr6t/
jzma[.]izpes[.]es
andrealong0510[.]blob[.]core[.]windows[.]net
amuricanxpress[.]com
login[.]officekeydesk[.]top
secure-en[.]com
my-php-app-production-cf6c[.]up[.]railway[.]app
chyisieaa[.]z20[.]web[.]core[.]windows[.]net
scalper[.]stackengine[.]sa[.]com
Microsoft and Outlook spearphish
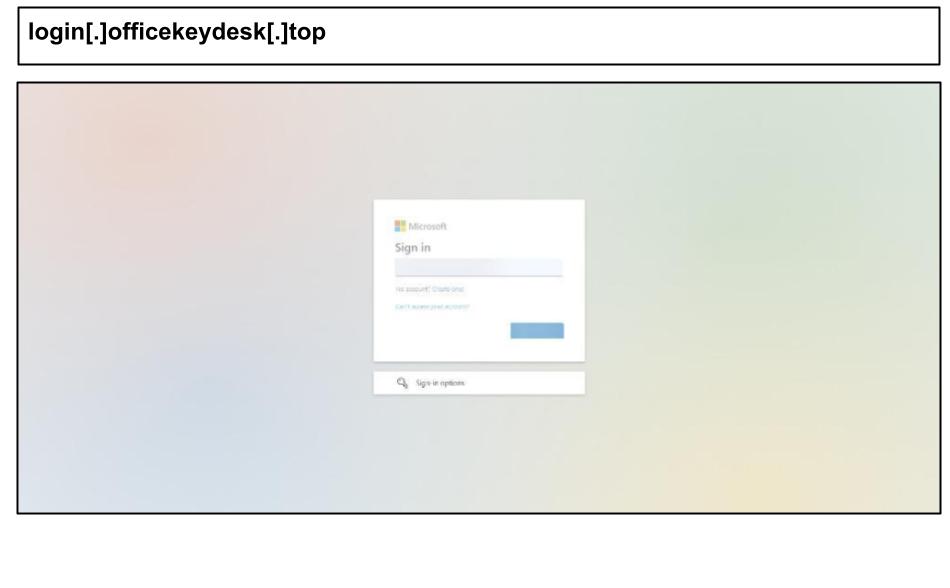
On July 16, a user at a Kentucky organization clicked the below Microsoft spearphish.
The page was hosted on a reputable hosting service, leveraging its good DNS reputation. The page also included a multi-stage credential harvest, offering the victim multiple MFA options like SMS and authenticator code.

On July 18, a Texas user clicked the below Microsoft scareware phishing attack.
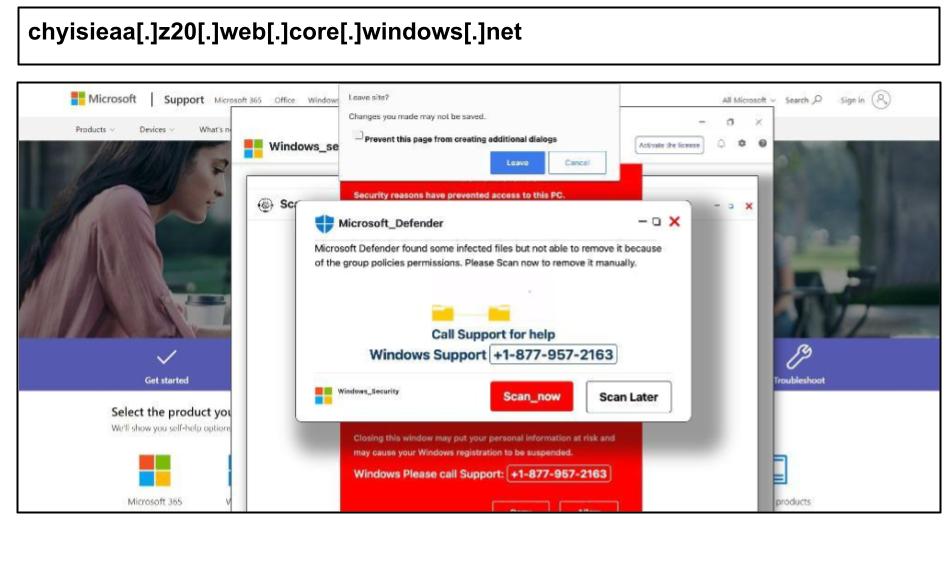
This scam site fingerprints the target device, using their IP, geo-location and browser details, to customize the popup. It then “locks” the browser with coercive tricks, including auto-playing alarm sounds—so the user feels trapped. Finally, a counterfeit Windows-Defender dashboard runs a fake quick-scan and flashes red warnings, all designed to convince victims their PC is infected and prod them into calling the fake support number.
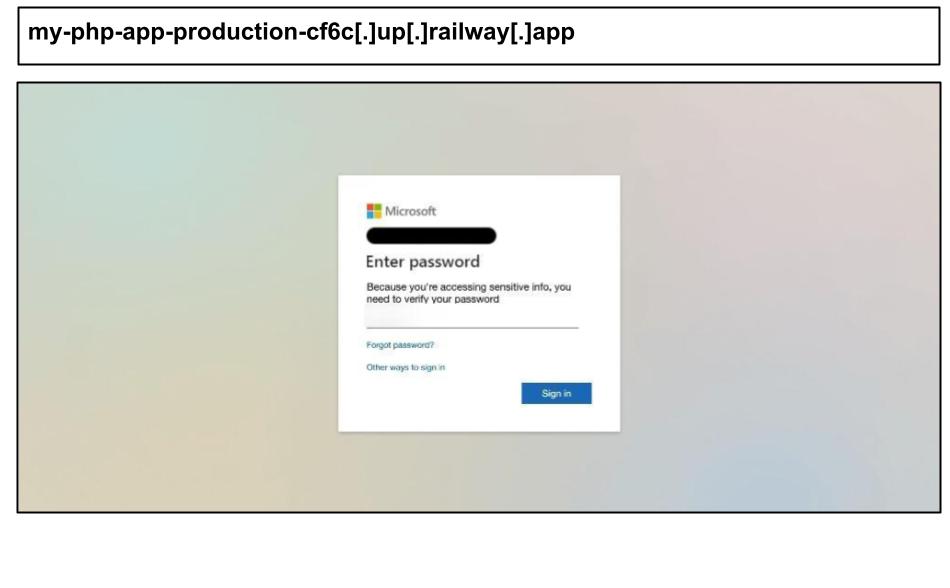
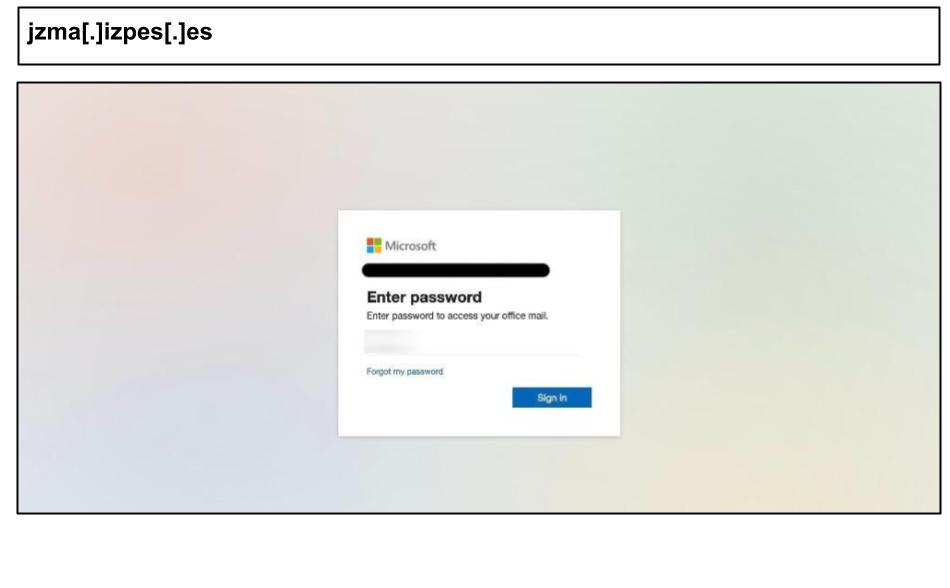
On July 18th, a user at a Kentucky organization clicked the below Microsoft spearphish.
In order to evade detection, the page source is uploaded across several trusted CDN servers, like AWS, Akamai and Fastly, rather than being hosted on a single phishing server. Adding to its conviction, the page carefully mirrors Microsoft’s authentication flow.

On July 22, an employee at a Florida organization clicked the below MIcrosoft phishing attack.
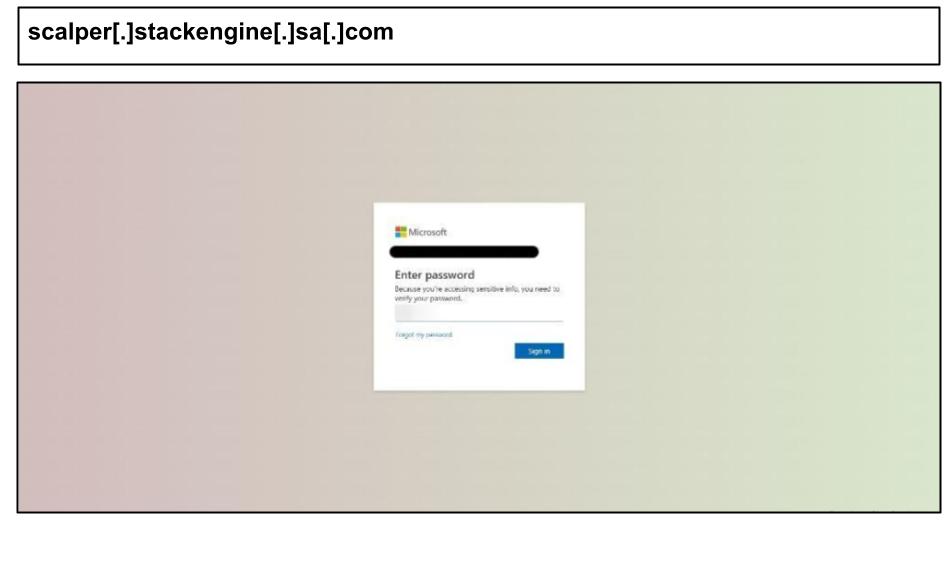
The URL loads behind a Cloudflare Captcha to avoid automated scanners. The phishing server blocks requests from non-browser user agents to further evade detection mechanisms.
On July 21, an employee at a Kentucky organization clicked the below Outlook phishing attack in a document share application.
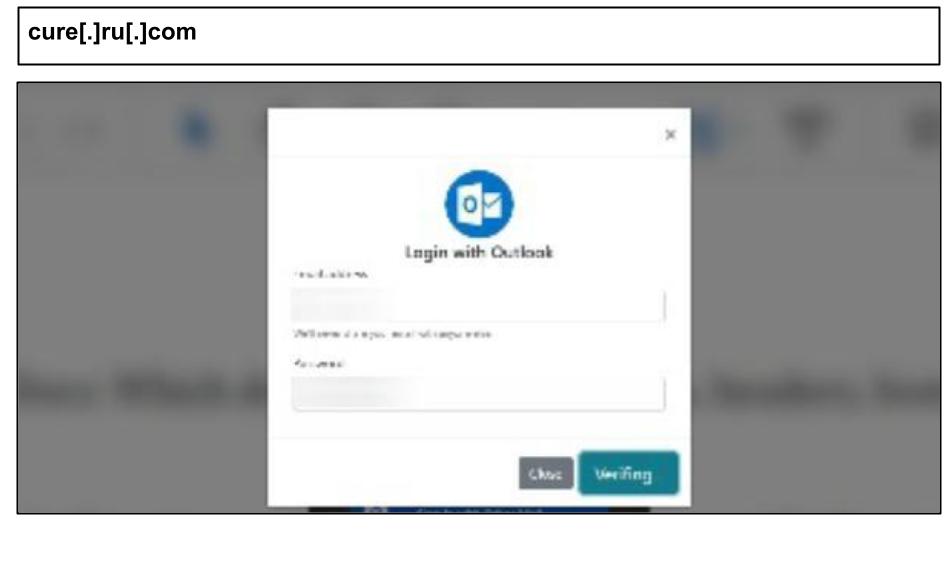
The phishing attack features buttons for Outlook, Office 365, Yahoo, AOL, and an option for "Other Mail." It also includes a pop-up for a one-time password that intercepts a 6-digit SMS or authenticator code in real-time, allowing for a complete session hijack. Later that same day, another employee fell victim to a separate Microsoft phishing attack.
The page included an encrypted payload to hide from static scanners and clipboard hijacking to thwart incident response efforts.
On July 30, an employee at a Georgia organization clicked on the Microsoft phishing attack shown below.
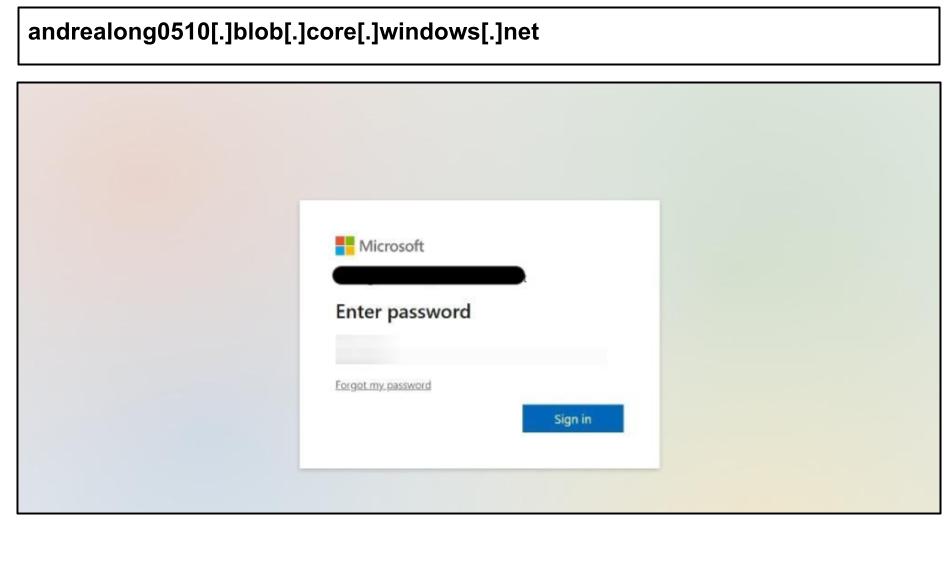
The page also used tools to avoid automated analysis and block manual inspection.
Phishing Targeting Consumer Banking Services
The same period saw a marked increase in phishing attacks targeting Bank of America and American Express customers on their work devices. Below are a couple of examples.
On July 17, an employee at a Kentucky organization clicked on the Bank of America phishing attack.
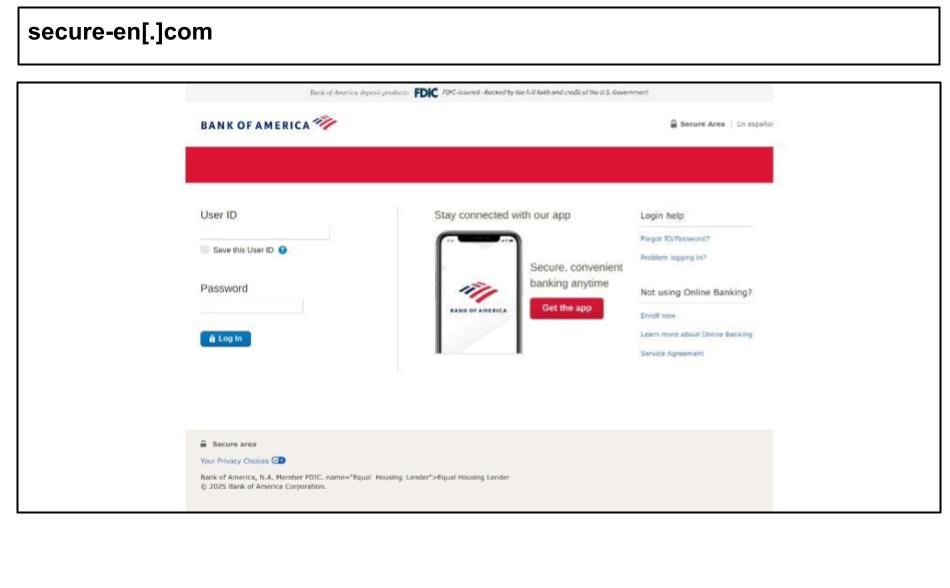
This is a pixel-perfect replica of the Bank of America login page. It included a secondary stage prompting the user for a 2FA code, SSN, or other security questions after credentials.
On July 23, a user at another Georgia organization clicked on the American Express phishing attack below.
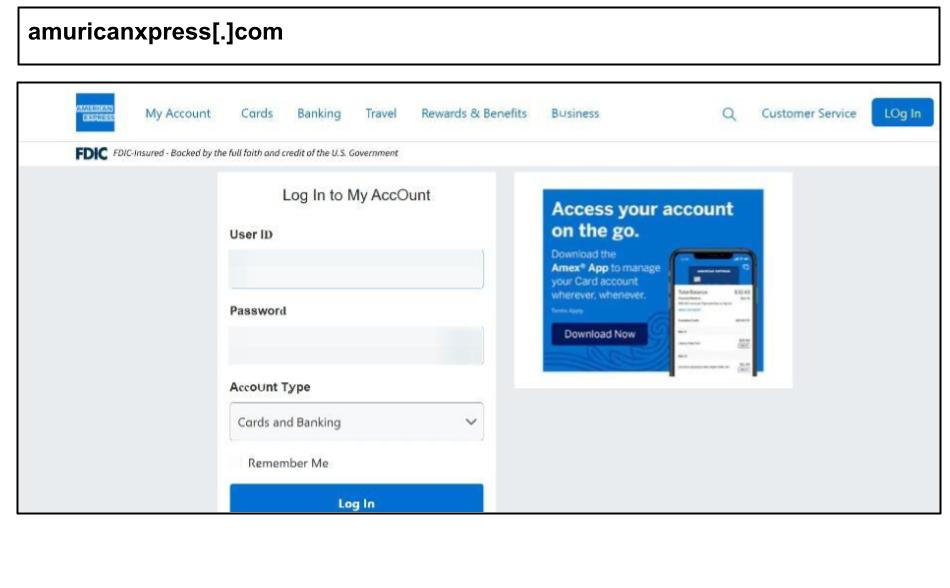
The user was prompted by an email or text message saying “Fraud alert on your Amex card – log in here to verify”. The URL also targets users via typo-squatting and includes user tracking parameters.
Mitigations
Block the specified domains on corporate firewalls and endpoint security solutions.
Educate users about phishing risks even on pages that purport to use MFA
Remind users of phishing risks for their personal accounts that they access, even if they are on corporate devices
Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.


