Password Policy Management
Password Policies ensure that when passwords are set or reset, they comply with your organization's policy for complexity. They can also prevent insecure values as well as prevent unwanted characters. There are two types of policies: Default Password Policy and Custom Password Policy, which would be any policy that is not the default. If a custom policy is set up with the "Default Policy" box checked, that custom policy will become the new default policy.
Custom Password Policies can be configured to apply to specific groups of users to follow the most appropriate restrictive policy based on their use and access of the system. If a user is does not fall into a custom policy based upon the criteria set, the Default Password Policy will apply.
For details on the settings of the RapidIdentity Default Password Policy, click here.
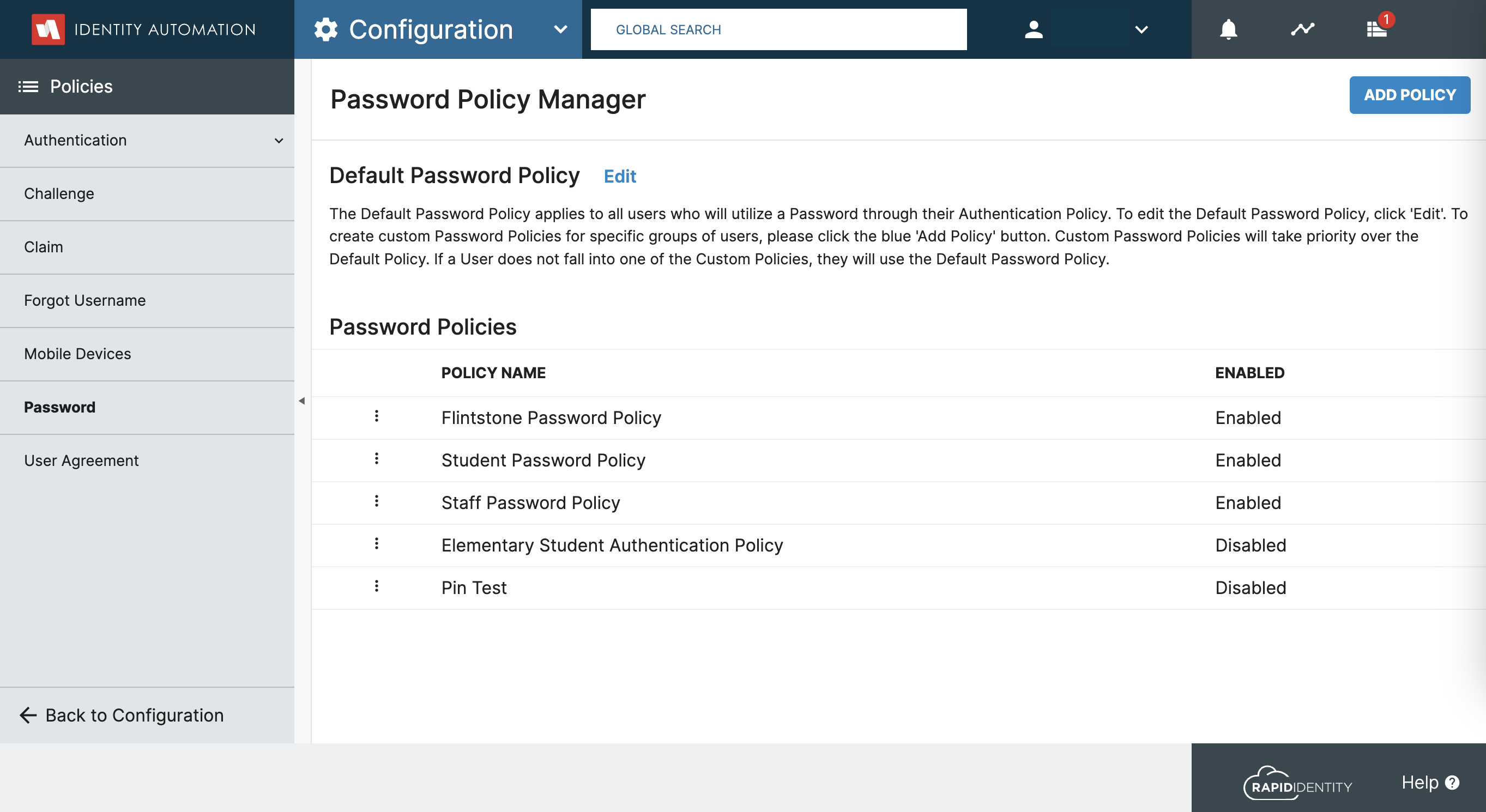
To configure Custom Password Policies for your District's Users, navigate to Configuration > Policies > Password to access the Password Policy Manager.
Password Policy Manager
To create a new Custom Password Policy, click on the Add Policy button in the top left corner:
There are five configuration tabs to consider when creating a Custom Password Policy.
General Tab
The first part of the General Tab focuses on the initial configurations for the policy.
- Enable - This toggle can be used to enable and disable this policy. This policy will not affect users until it is toggled ON.
- Name - Provide the policy a name that is easy to identify for its purpose. This should be unique among all other Password Policies.
- Set Up Instructions - This section includes a rich text editor. The content you input here will display during the user's Password Policy and provide them directions on how to create their passwords.
- Affected Users - For custom policies, you must define the criteria for the Users that will be affected by it. The options are Role Based and Attribute Based.
The second part of the General tab controls Password Reset options for the policy.
- Allow Password Reset to Attribute Value - When this is checked, a new field will appear where the Administrator can select the Attribute Value to use in this situation.
- Allow Random Password Generation - When checked, this allows a randomly generated password to be used for an Admin Triggered password reset.
- Administrative Password History Override - With this toggled ON, the Password History will not be enforced when an Administrator resets a password on a User's behalf.
- Password Expiration - There are two settings included for Password Expiration:
- PASSWORD MAXIMUM AGE: This value determines the maximum amount of time that a password will remain valid for a user. Once this duration has elapsed, the user will be forced to reset their password according to the policy settings.
The Default value for this is None, which signifies that the password will not expire. Leaving this value as None ensures that the currently user experience will remain in place. - EXPIRATION WARNING: This value determines the number of days in advance that a user will be notified that their password will be expiring.
This field will be greyed out if the Password Maximum Age is set to None. Once active, the default value for this field is 7 days.
- PASSWORD MAXIMUM AGE: This value determines the maximum amount of time that a password will remain valid for a user. Once this duration has elapsed, the user will be forced to reset their password according to the policy settings.
When making modifications to the policies, please remember to click the Save button in the bottom right corner of the page to ensure the changes are saved.
If the Restrict Password Reuse and Allow Reset to Attribute Value options are both enabled for a password policy, then it's possible these options may conflict with one another if the user(s) have previously had that RI attribute value as one of their recent passwords.
Password Syntax
This tab focuses on the restrictions placed upon characters and required length of password.
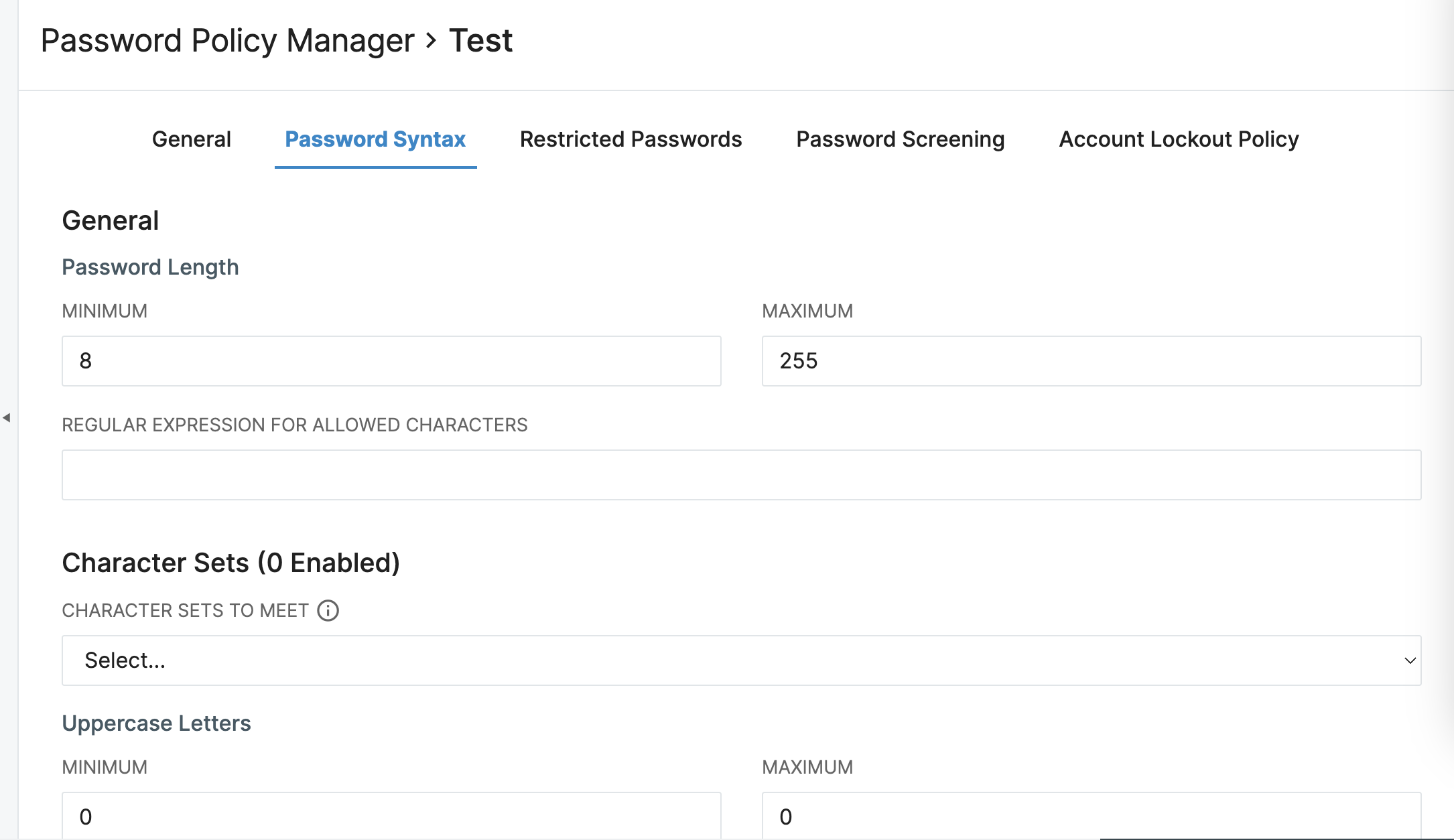
-
Password Length - This setting determines the minimum and maximum amount of characters to be used in a character. For a discussion around Best Practices for Password Length, please refer to this article.
-
Regular Expression for Allowed Characters - This field can support any regular expression pattern that Java can accommodate.
-
Character Sets to Meet - This value determines how many of the Character Sets must be satisfied during a Password Reset.
- Once a number of Character Sets to Meet has been specified, the Character Sets themselves must be customized. For each type of Character, a minimum and maximum number to include must be defined. The number of Character Sets with Min/Max configured must be equal or greater than the number of Character Sets to Meet.
Restricted Passwords
This tab allows for the restriction of letter sequences and words.
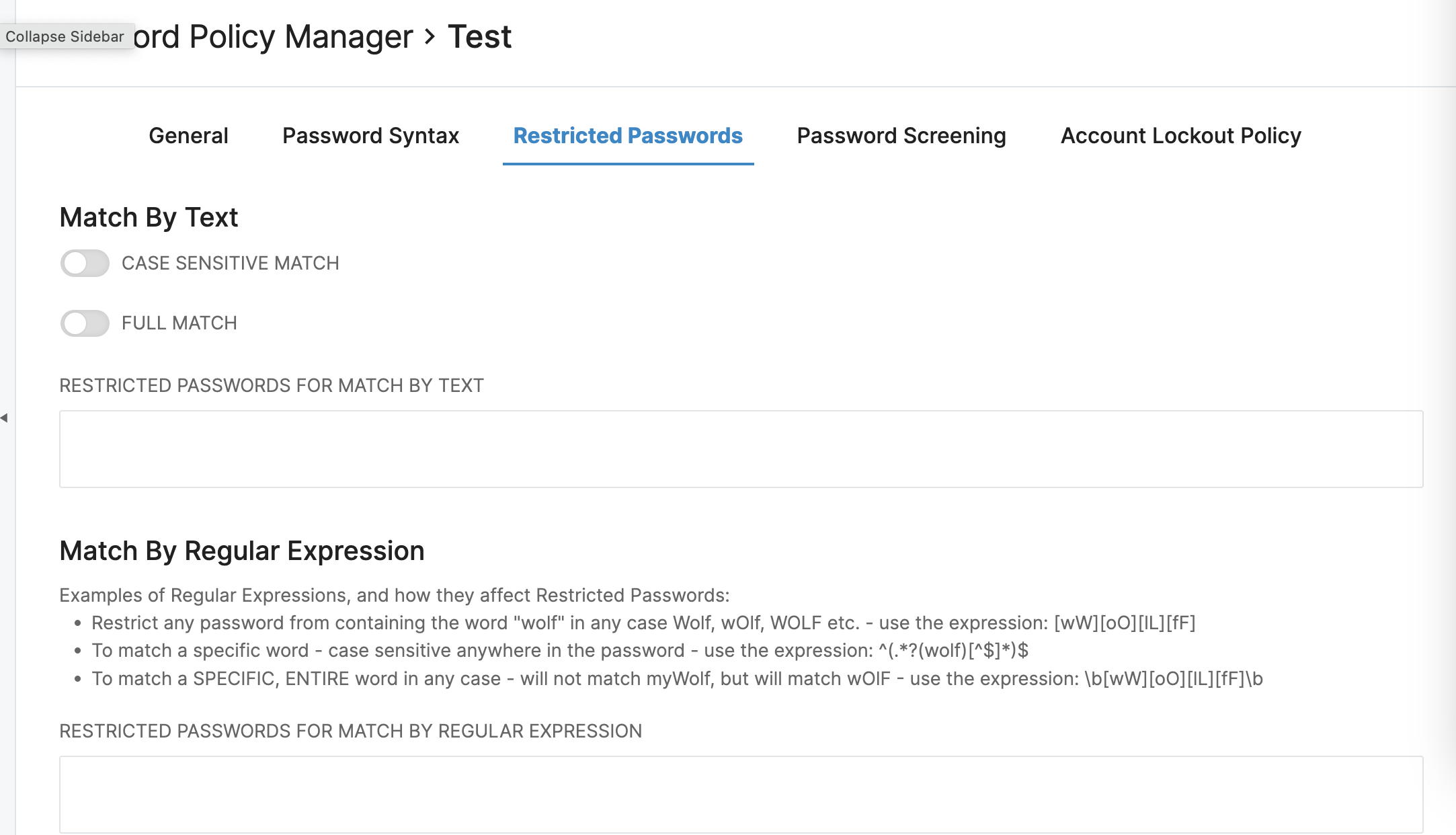
The first section deals with options for 'Match by Text'.
- Case Sensitive Match - When this is checked, only passwords that match with case sensitivity will be blocked from usage.
- Full Match - If only matches of full words is desired, this box should be checked. If left unchecked, usage of restricted passwords in longer sequences will be blocked.
- Restricted Password - To add a restricted password, in the provided text box type the value to be restricted. Once the full password is typed, hit enter to add it to the list. It will now be visible as a 'chip'. Continue that process until all desired values have been added.
The second section deals with options for 'Match by Regular Expressions'.
- Restricted Passwords - This field can support any regular expression pattern that Java can accommodate. Below are a few specific examples of Regular Expressions and how they would affect the policy:
Restrict any password from containing the word "wolf" in any case Wolf,wOlf,WOLF, etc.
(?i)^(.*?(wolf)[^$]*)$
to match a specific word - case sensetive anywhere in the password
^(.*?(wolf)[^$]*)$
to match a SPECIFIC, ENTIRE word in any case - will not match myWolf, but will match wOlF
(?i)wolf
The last section deals with options for 'Match by Attribute Values'.
- Case Sensitive Match - When this is checked, only passwords that match with case sensitivity will be blocked from usage.
- Full Match - If only matches of full words is desired, this box should be checked. If left unchecked, usage of restricted passwords in longer sequences will be blocked.
- Restricted Password - To add a restricted password, in the provided text box type the value to be restricted. Once the full password is typed, hit enter to add it to the list. It will now be visible as a 'chip'. Continue that process until all desired values have been added.
The last section deals with options for 'Restrict Password Reuse'.
- Passwords Remembered - The value selected for 'Passwords Remembered' determines how many previous passwords cannot be reused by a user. For example, if this value is set to 5, then a user will not be able to reuse any of their last five previous passwords. The Default value for this field will be No Restriction, signifying that there is no limit on reusing passwords.
Password Screening
In addition to custom blacklisting capabilities for restricting passwords, RapidIdentity provides automatic Password screening for compromised passwords.
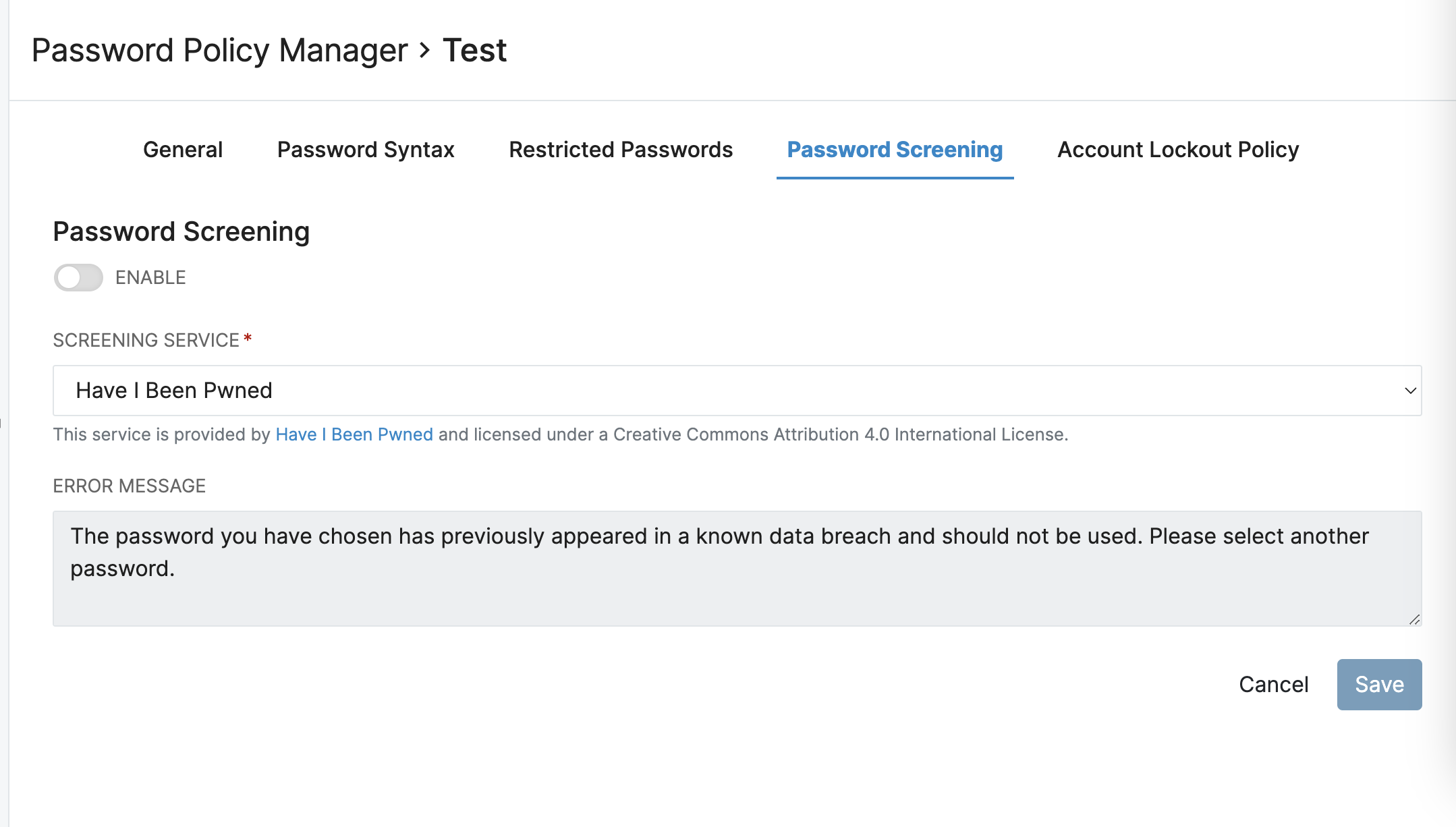
This service is provided by Have I Been Pwned and licensed under a Creative Commons Attribution 4.0 International license.
- Enabled - Check this box to enable Password Screening.
- Screening Service - This field designated the service provider for password screening.
- Error Message - When Password Screening is enabled, the error message shown here will be sent to Users who are identified in the screening process. It can also be customized.
Account Lockout Policy
This tab allows configuration of granular permissions to enforce automatic locking and unlocking of Users who have unsuccessful authentication events.
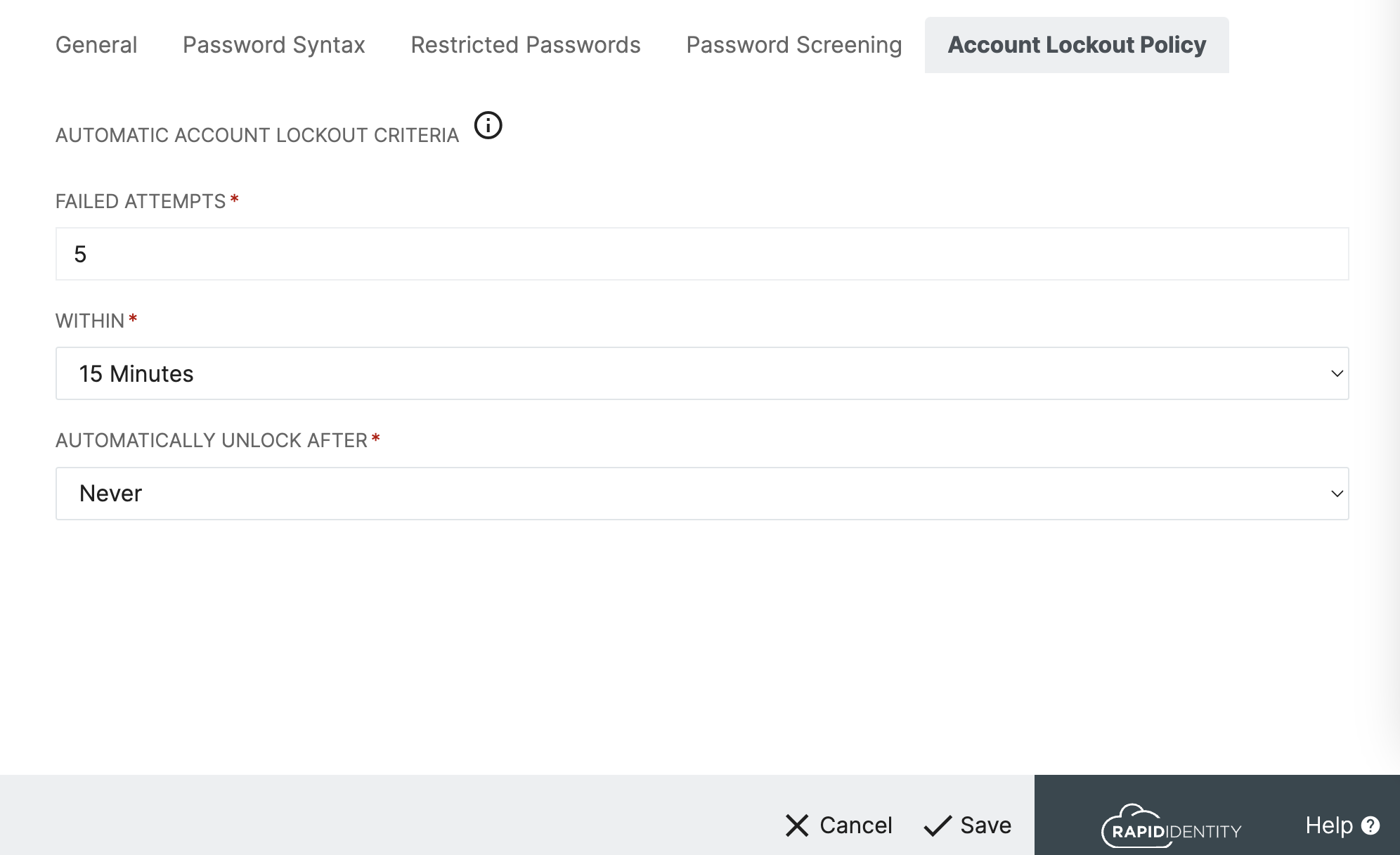
- Failed Attempts - This value determines how many unsuccessful authentication attempts can trigger an automatic lockout. These must occur within the time duration specified in the next field.
- Within - The length specified in this field determines the duration of time the database will be tracking failed authentication events. If the number of Failed Attempts reaches the value set in the first field, a lockout will occur. Once the duration of time lapses, the number of Failed Attempts returns to zero for that user.
- Automatically Unlock After - When a User is automatcially locked out, their account will remain locked for the length of time specified in this field. Once that time has passed the account will still show in the Locked Accounts delegation however a correct password will let the user Login and unlock the account. Selecting 'Never' will enforce users to remain locked out until an Administrator manually unlocks the account.
For more details on these new Password Policy Enhancements, and how they will affect the User Experience, check out this article: Password Policy Enhancement - What's New?
Custom Password Policy Tips
Handling of Criteria for Users that fall into Multiple Policies
Previously, the prioritization of multiple policies determined which criteria would be enforced for a User in multiple policies. This has been updated to enforce the most stringent criteria assigned to a User through multiple policies. For example, if User A is assigned to 2 policies with different 'Failed Attempts' values for Account Lockout. Which ever value is lower will trigger the lockout for that account.