- 18 Aug 2025
- 4 Minutes to read
- Print
- DarkLight
Phish Wire - August 19 2025
- Updated on 18 Aug 2025
- 4 Minutes to read
- Print
- DarkLight
During the first half of August, there has been a significant increase in Microsoft support scams that utilize keyboard locks and other techniques to encourage users to contact specific call centers. Additionally, other Microsoft phishing attacks during this time employed aggressive device fingerprinting, MFA relay tactics, and delivery methods through event invitations and PDFs. We have also noticed similar tactics being used in phishing attempts targeting customers of financial services such as Chase and US Bank. Here are some examples and key highlights.
vdus28firf[.]z13[.]web[.]core[.]windows[.]net/win[.]html
enumeducomebachtorenewjouly[.]one
cb2732788f444a6eacc7e2c468dd4577[.]gloweverse[.]com
alternative-creations[.]com
dd53985e595c41068224351932364cd6[.]shedthelightnepal[.]org
adsfd2gyj[.]z19[.]web[.]core[.]windows[.]net
login[.]welvz[.]com
peachpuff-turtle-958085[.]hostingersite[.]com
signlepolnt[.]uspank[.]today
onedrive-microsoft[.]scene[.]com[.]de
securecenter09[.]com/x0/pc
Microsoft Support Scams and Paperless Post Delivery
This period saw an uptick in support scams that target users with their IP, geolocation, and device details while locking their keyboard to get them to call a scam support number.
On August 1, a mental health professional at a Kentucky organization clicked the phishing page below.
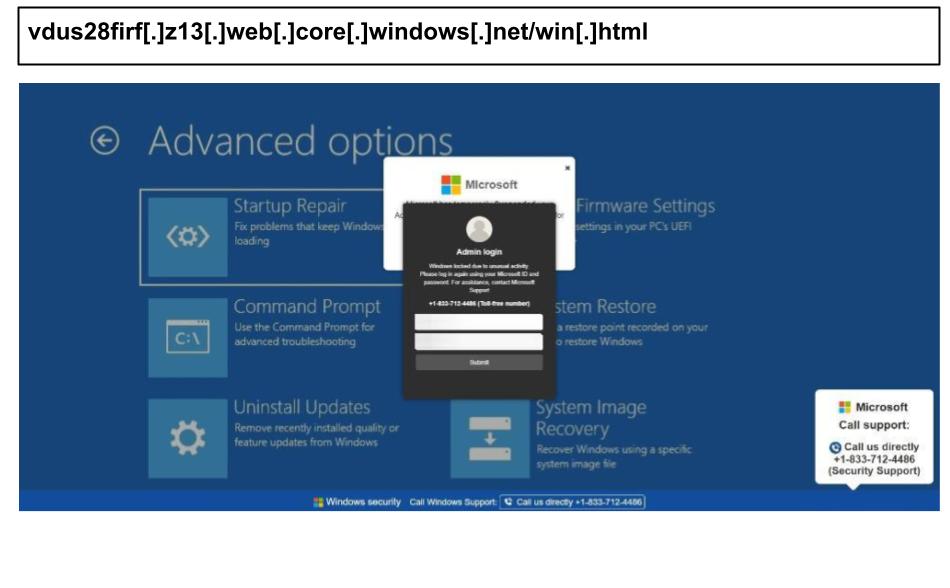
This phishing page customizes itself according to the target's IP address and uses URL parameters to change the phone number, directing different recipients to various call centers. The page also locks the device's keyboard, creating the impression that calling the support number is the only way to exit.
Similar attacks have affected employees in several states, including Illinois, Texas, and Georgia. One example occurred when an administrator accidentally clicked on a phishing link on August 12th.
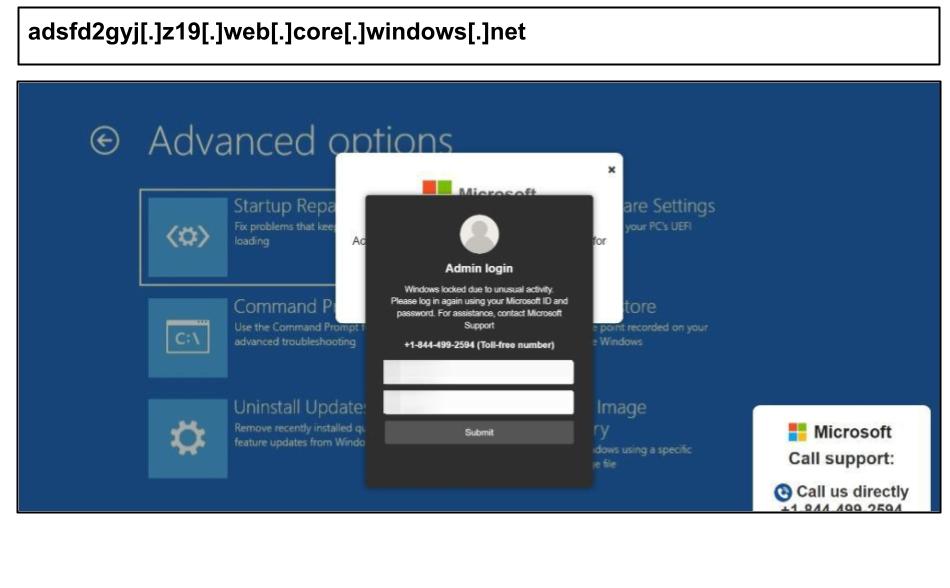
Hackers are targeting more than just credentials. They use social engineering tactics to persuade users to call a support number. During this call, users are tricked into installing fake remote desktop software, which can enable the attackers to steal sensitive data and install malware, such as keyloggers and ransomware.
Additionally, there have been several Microsoft attacks distributed through unconventional channels, such as invitation platforms and document sharing services. For example, an Outlook phishing page was accessed through a Paperless Post invitation by a mental health practitioner from a Kentucky organization on August 11th.
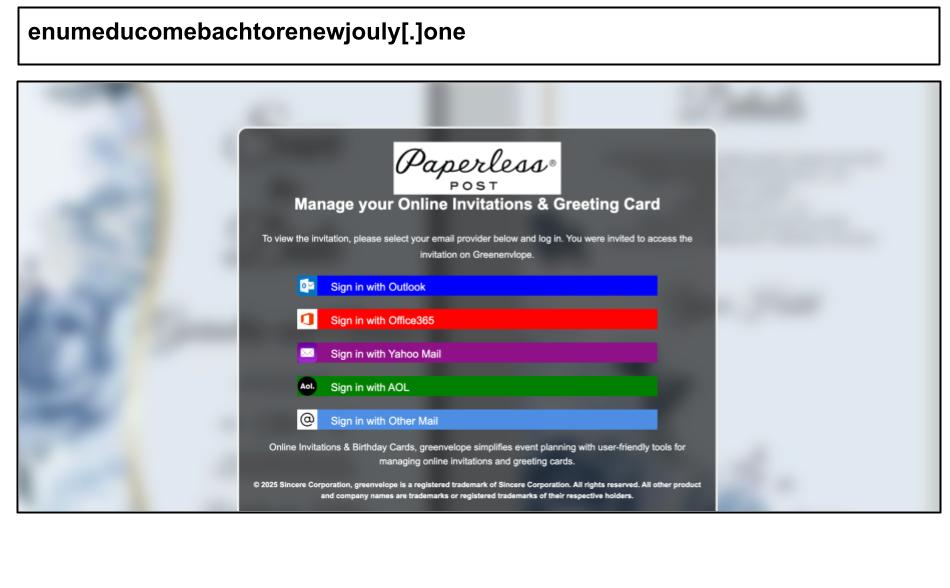
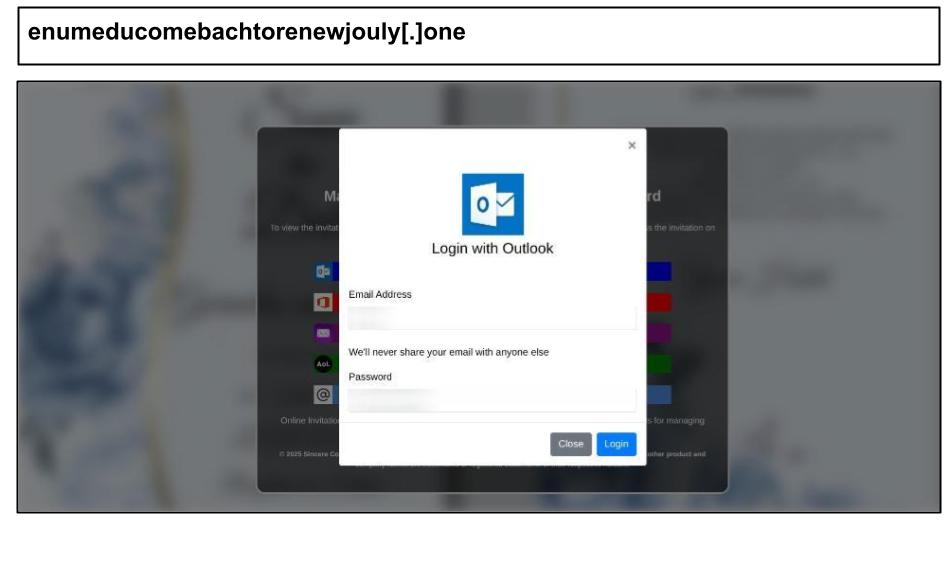
This phishing attack was delivered through an invitation platform and included a Cloudflare CAPTCHA, a fake MFA prompt, as well as options to steal credentials for multiple accounts such as Outlook, Office 365, Yahoo, and AOL.
On August 14th, a user from Kentucky clicked on the OneDrive phishing page through a PDF file share.
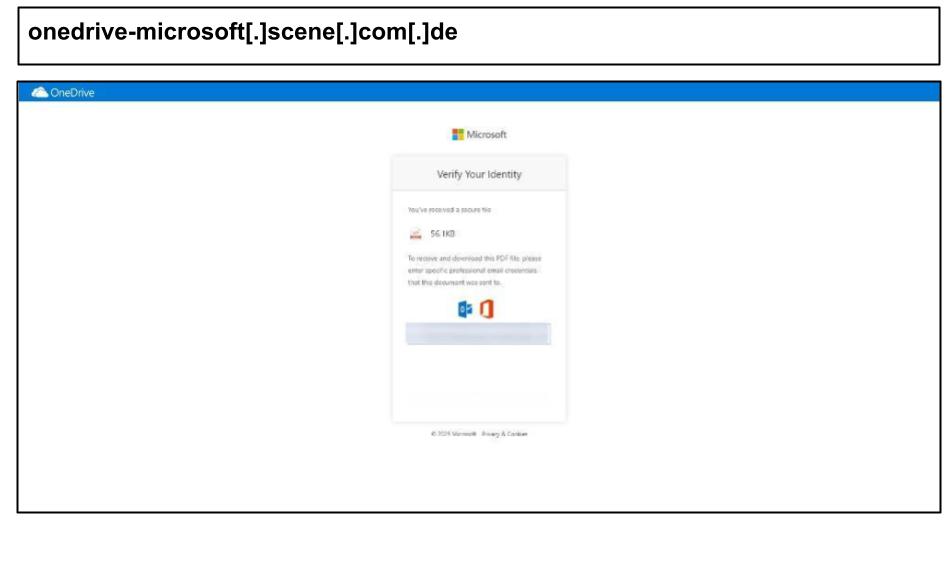
In addition to stealing passwords, the site may also gain long-term access to victims' email accounts by using fake app permissions.
We also noted a Microsoft phishing attack hosted on a compromised non-profit website. On August 8th, an employee at a Kentucky-based organization clicked on a Microsoft phishing page that was hosted on a website for a charity based in Australia and Nepal.
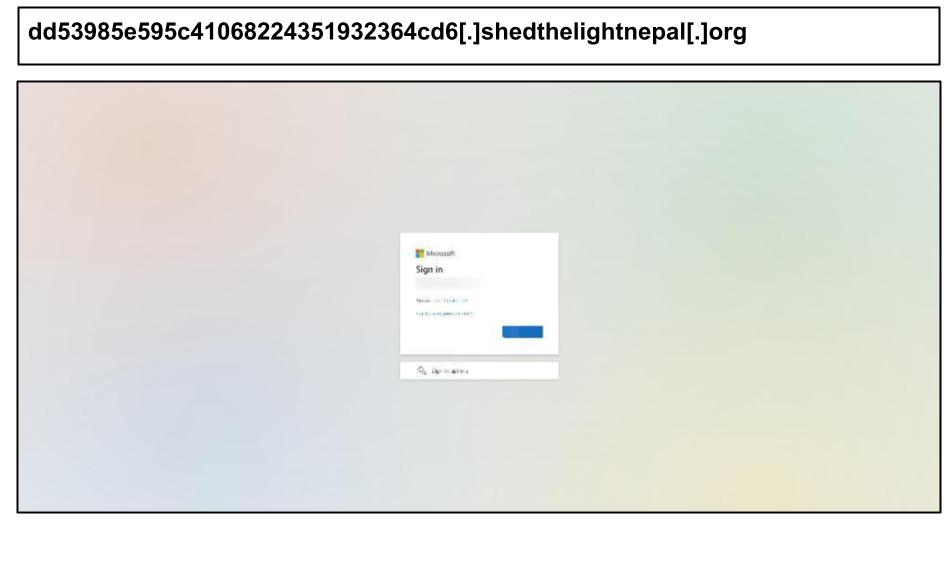
A threat actor set up numerous similar pages consisting of 32-hex subdomains under the domain ‘shedthelightnepal.org’ to function as fake Microsoft endpoints and content delivery networks. The phishing kit is designed to harvest multi-factor authentication codes, one-time password codes, and password credentials.
Other Microsoft phishing schemes demonstrated techniques for device fingerprinting and evasion tactics to bypass various types of security scanners.
On August 14th, another staff member from Kentucky fell victim to a Microsoft phishing attack.
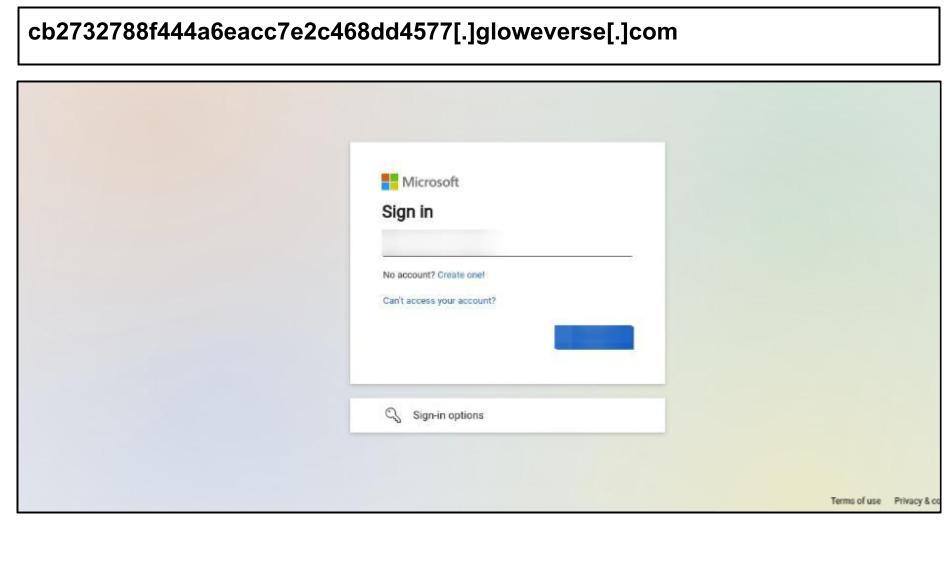
The attack uses aggressive device fingerprinting and includes extra fake MFA steps to phish one-time codes and “pass keys”.
On August 14th, two staff members at a Washington organization clicked the Microsoft phishing page below.
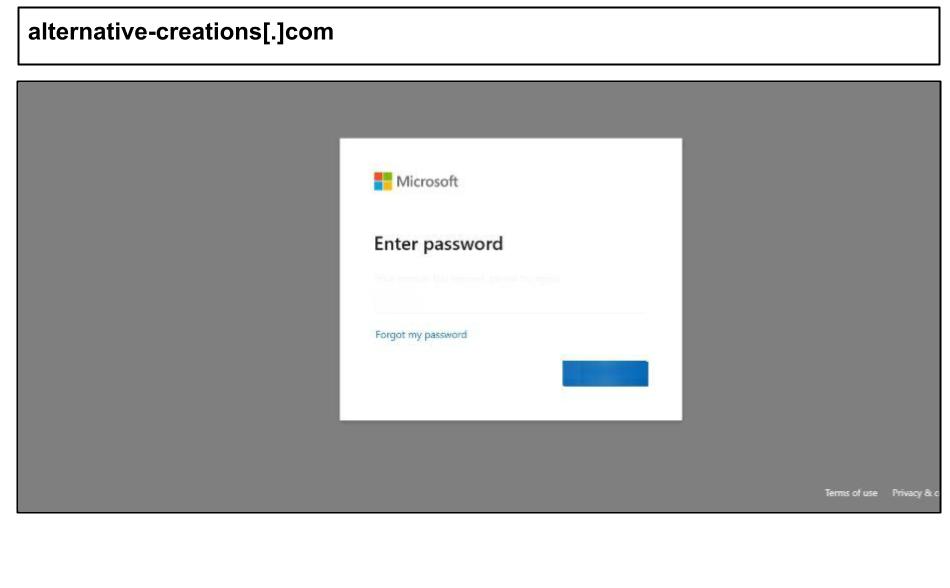
The HTML body is filled with irrelevant, human-like event summaries and random token strings, while the page title claims “Sign in to your account”—a common tactic used to deceive scanners and reputation systems that only skim through the text.
Financial Services Customers Targeted on Personal Devices
In early August, customers of well-known banking services such as Chase and US Bank were targeted while using their work-issued laptops. Hackers utilized tactics like device fingerprinting, MFA prompts, and fake Captchas to evade detection.
On August 14th, a staff member from an organization in Minnesota unwittingly clicked on a phishing page that appeared to be from US Bank.
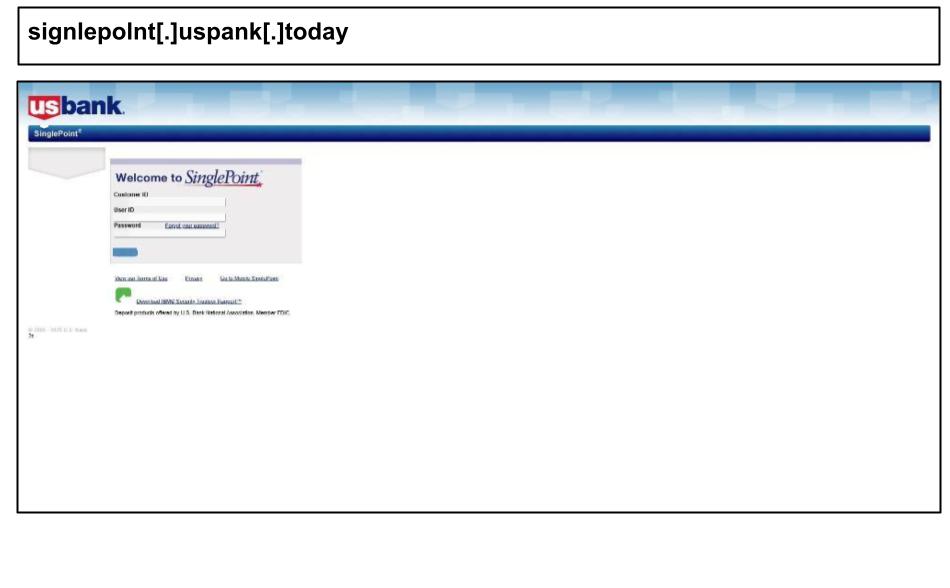
Each visitor to this phishing page is assigned a unique token, enabling the criminals to track which lure was effective. The page employs fake error messages and a "loading" overlay to persuade victims to attempt their login again. When the target clicks submit, the page discreetly collects device fingerprints, such as the operating system, browser, screen size, languages, and even graphics card information. It also attempts to read site cookies—data that can aid them in bypassing defenses or impersonating the victim elsewhere. This is crucial because it allows hackers to exploit personal email accounts of targets to gain access to their corporate-issued devices, thereby circumventing any corporate email protections.
On August 14th, an employee at a Kentucky organization clicked on a Chase Bank phishing link on their work device.
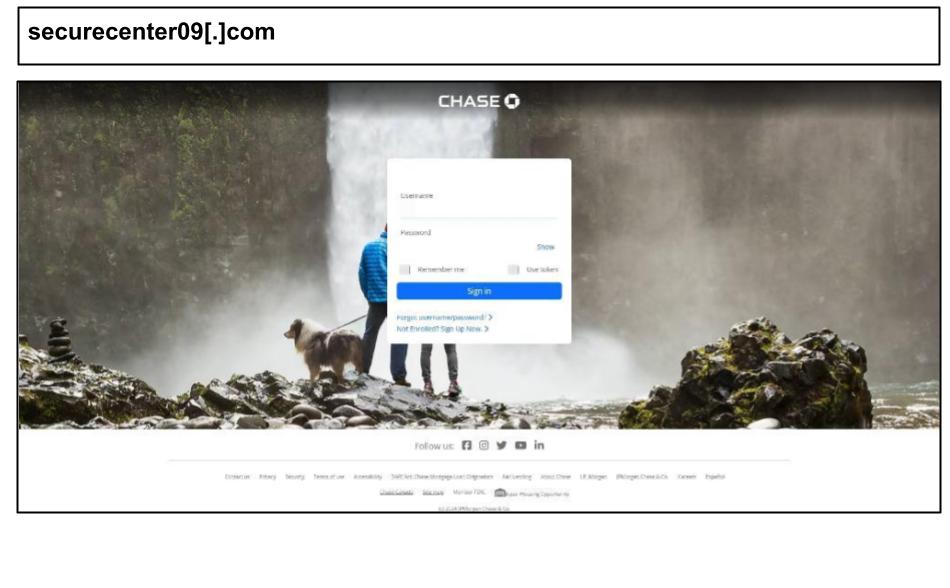
This phishing page also had a two-factor prompt to steal MFA codes. It included a CloudFlare CAPTCHA challenge to evade detection from various scanners.
Mitigations
Block the specified domains on corporate firewalls and endpoint security solutions
Educate users about phishing risks even on pages that purport to use MFA
Remind users of phishing risks for their personal accounts they access even if they are on corporate devices
Enforce MFA on all district logins to reduce the risk of credential compromise


