- 24 Feb 2025
- 1 Minute to read
- Print
- DarkLight
Phish Wire - Feb 25 2025
- Updated on 24 Feb 2025
- 1 Minute to read
- Print
- DarkLight
There has been an increase in phishing activity recently, focusing on platforms such as Instagram, Microsoft, and Chase Bank. Attackers leveraged sophisticated tactics, including hosting phishing pages on legitimate cloud platforms and enabling them to bypass traditional detection mechanisms. We also saw a massive surge in malware hosted on Azure infrastructure. Below are key highlights and examples of recent phishing activity.
azureserv[.]com/?__cpo=aHR0cHM6Ly93d3cuaW5zdGFncmFtLmNvbQ
wittrams[.]com
skspofficelogin[.]richargest[.]cloud/?QvZli=YQbr&sso_reload=true
screetru[.]es/?auth&apitoken=rylae2be63wttzu
superdemolink00010[.]z13[.]web[.]core[.]windows[.]net
mexapvpqbu[.]life/script/iprp[.]php?t=1
track2.111cvm51-s9z-19[.]com
e-connexioninfosclients[.]duckdns[.]org/
seashell-app-eigd4[.]ondigitalocean[.]app/
orca-app-9mwg9[.]ondigitalocean[.]app/
king-prawn-app-3aosz[.]ondigitalocean[.]app/
securiti009[.]z13[.]web[.]core[.]windows[.]net
securitu014[.]z13[.]web[.]core[.]windows[.]net
securitl111[.]z13[.]web[.]core[.]windows[.]net/?gad_source=5
securitj107[.]z13[.]web[.]core[.]windows[.]net
securitj105[.]z13[.]web[.]core[.]windows[.]net
Instagram Zero Day
Recently, a school employee clicked a zero-day Instagram phishing page. Even weeks after we discovered the issue, the URL remains 100% clean on VirusTotal.
.jpg)
What often makes social media cases like this difficult to report is that they are often clicked via native messaging apps like Facebook or Instagram Messenger, which are outside the scope of traditional email-based security architecture.
We further saw a streak of Microsoft credential harvesters clicked at organizations across Washington and Kentucky, like the example below.

Microsoft and Apple Support Phishing
In the second half of January, we witnessed a massive surge in malware sites impersonating Microsoft and Apple support like the example below.
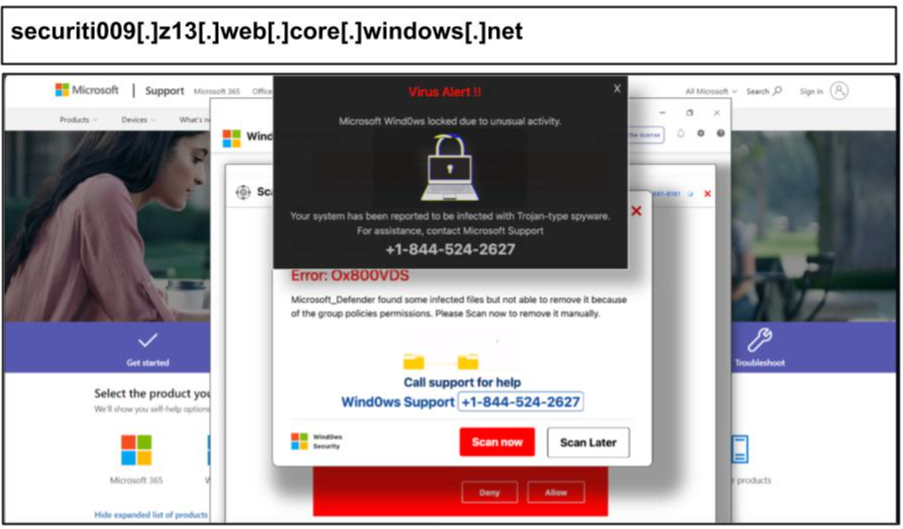
In a matter of 2 weeks, twenty-three different users at a Texas organization clicked on phishing links hosted on windows.net or redirected to phishing pages on that domain. Sneakily, phishing attacks masquerade as support, prompting users to call a phone number or install malware. They adapt the displayed logos to match either Apple or Windows, depending on the device accessing the URLs.
Mitigations
Add the specified domains to your block lists.
Focus awareness efforts on high-risk credentials.
Educate users that social media phishing can pose serious organizational risks, particularly when accessed on work devices.
Remind users never to dial a support number received via an email. Instead, search Google for the intended support number.


