- 07 Jul 2025
- 2 Minutes to read
- Print
- DarkLight
Phish Wire - July 8 2025
- Updated on 07 Jul 2025
- 2 Minutes to read
- Print
- DarkLight
The last week of June and early July saw a surge in zero-day phishing attacks targeting both corporate Microsoft/Ouook logins and personal web services (e-commerce, streaming, and email) on work devices. Threat actors employed sophisticated tactics – from obfuscated JavaScript and fake OAuth login flows to Telegram-based exfiltration – allowing many of these phishing pages to evade traditional detection measures. Here are some examples and highlights.
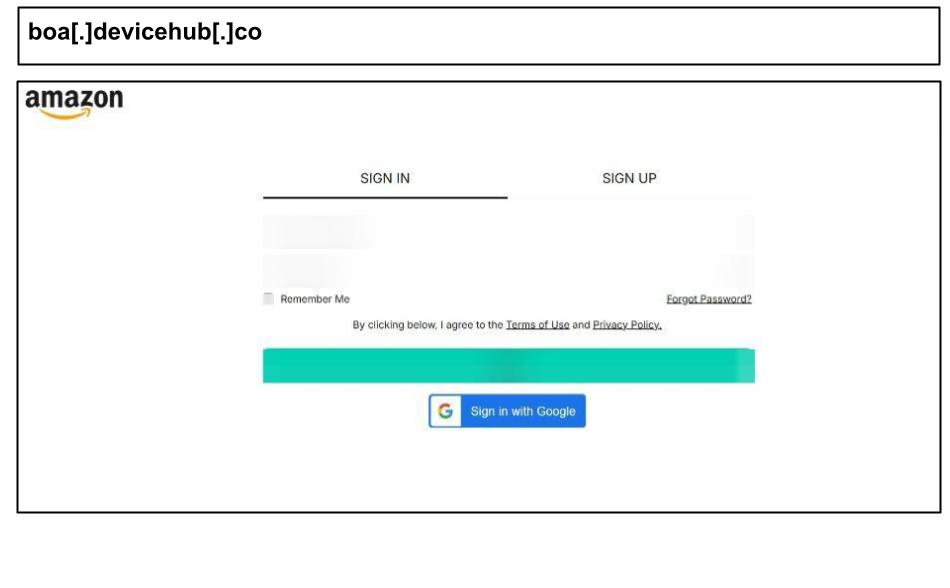
boa[.]devicehub[.]co/login
s3[.]lax[.]sharktech[.]net
ru0[.]eotskyj[.]es
zolotayanora[.]com
nextflyerpub[.]store
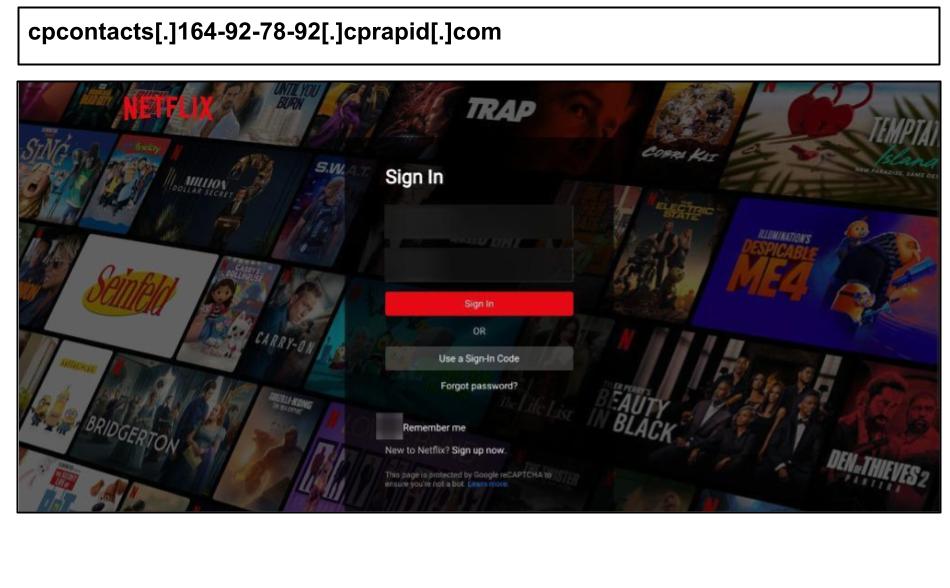
cpcontacts[.]164-92-78-92[.]cprapid[.]com
fhi9o09i5[.]uywpk[.]es
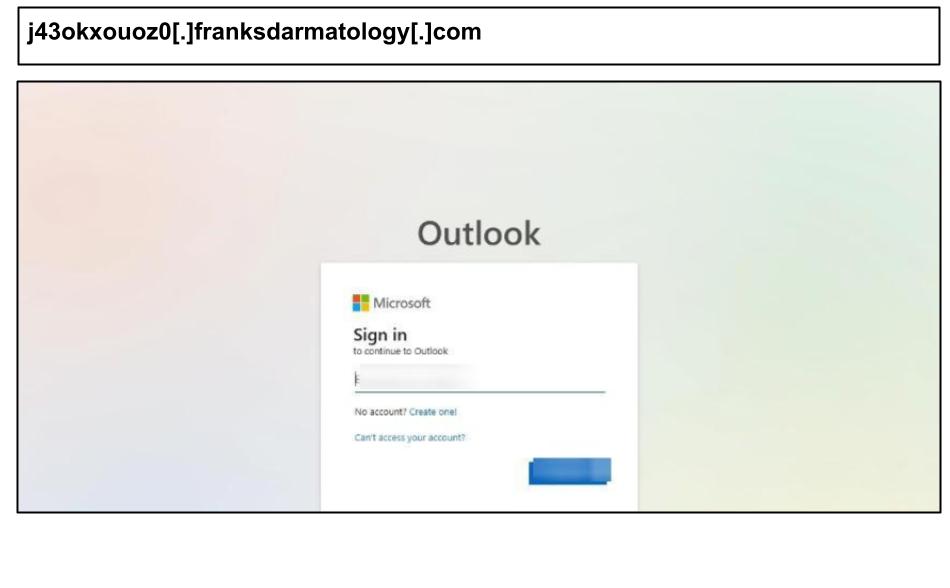
j43okxouoz0[.]franksdarmatology[.]com
webmail[.]50-6-111-88[.]cprapid[.]com
Microsoft Spearphish and Telegram Bot Exfiltration
This period witnessed a number of interesting attacker techniques like the use of Telegram Bot APIs and clever techniques to conceal page content.
On July 2, a staff member at a Texas organization clicked on a Microsoft Outlook spear-phishing email delivered via a file-sharing link.
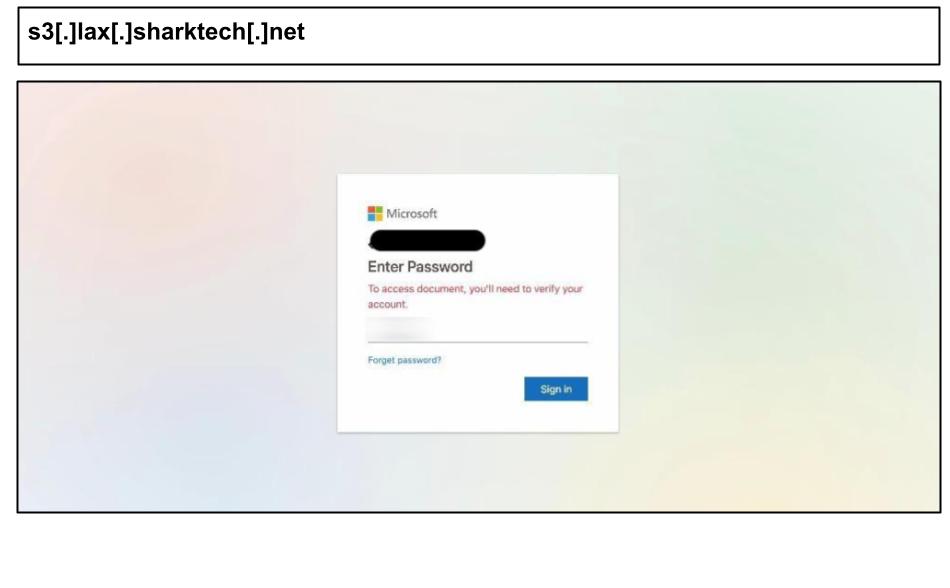
The stolen credentials were not sent to a typical web server; instead, the page utilized the Telegram Bot API to exfiltrate captured passwords and user data in real-time. This tactic provides the attacker with an anonymous, easy channel for data theft while helping the phish bypass traditional defenses. Another Texas employee, on the same day, fell for a similar Microsoft 365 phish.
This page hid a massive block of obfuscated JavaScript in its code, likely to conceal malicious tracking or keystroke logging scripts, making static analysis difficult.
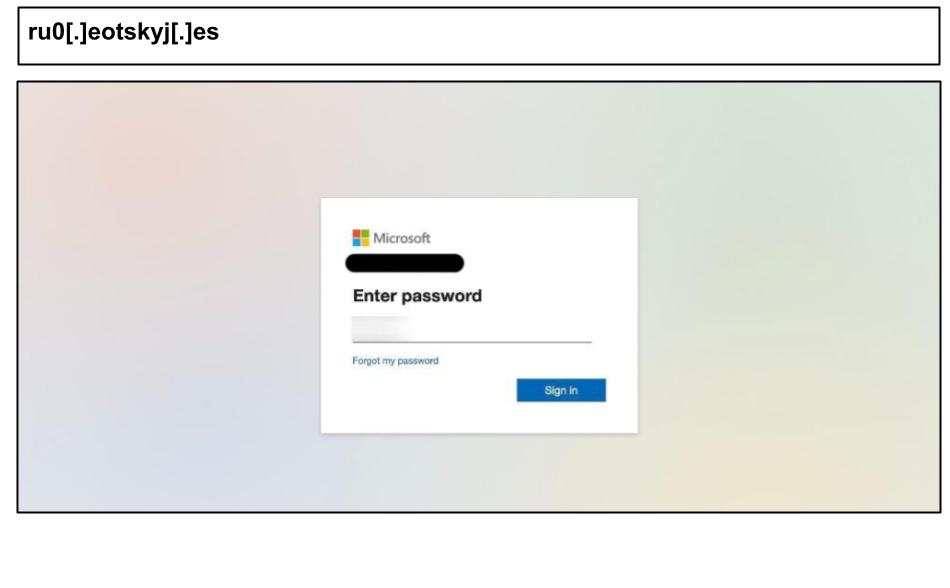
On June 24, a Kentucky employee clicked the link below to an Office 365 sign-in page.
The phishing page’s HTML was entirely encoded into a single string, which was passed to a document.write(unescape(...)) function. This meant the page’s content was only rendered at runtime, helping it evade detection from security scanners that rely on static HTML analysis.
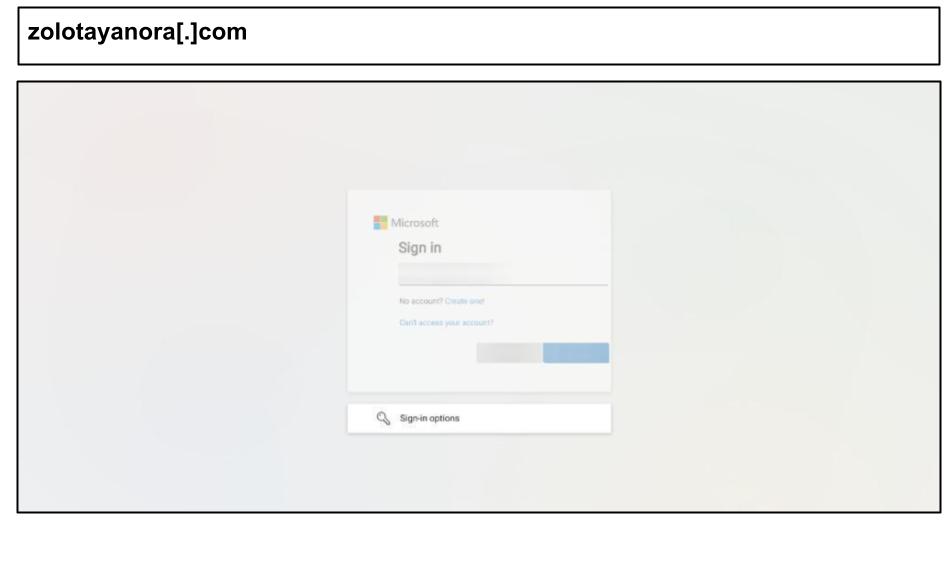
In early July, another Kentucky user was lured to a fraudulent Outlook Web Access page that employed multiple evasive techniques.
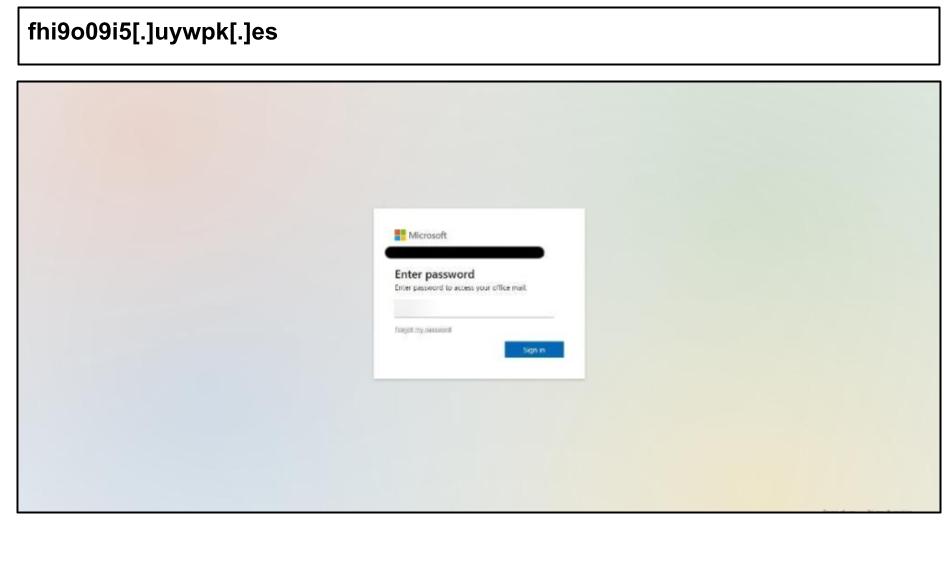
The HTML payload was encrypted and only decrypted in-browser to reveal the fake login form. It also contained scripts to hijack the user’s clipboard and prevent copying of content. It further sets special meta tags to prevent caching or sandboxing by web crawlers.
On June 23, an employee at a Washington organization clicked the spear-phishing page below, which loaded several resources from legitimate Microsoft content delivery networks (such as aadcdn.msauth.net and aadcdn.msftauth.net) and even referenced Microsoft’s own “Watson” telemetry service in its code.
E-commerce and Streaming Phishing on Personal Devices
This midsummer period saw a surge in spearphishing targeting district users on their personal accounts, particularly Amazon account phishing.
On June 30, a Texas employee clicked on a fake Amazon login page on their work device, which included fake “Sign in with Google” and “Sign in with Facebook” authentication flows designed to steal multiple types of identity credentials.
Another Amazon credential harvester was clicked on June 29, targeting a user in Kentucky, and employed a carbon copy of Amazon’s multi-stage login flow.
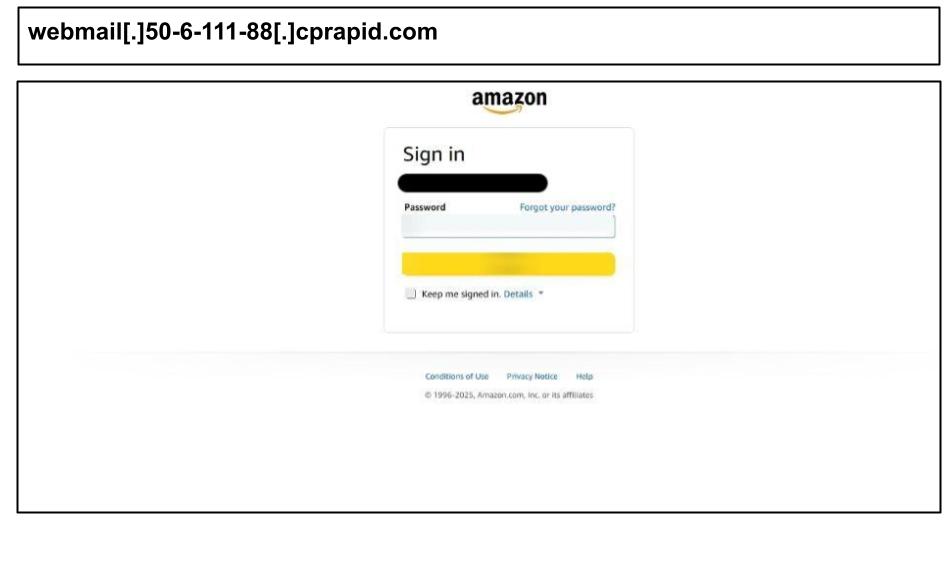
Behind the scenes, a suspicious JavaScript function was executing silently every few milliseconds, sending stolen data back to a remote command-and-control server. This aggressive data-capture mechanism enabled the attacker to extract additional information (potentially including session data or two-factor tokens) beyond just the username and password.
The period also included Netflix and AOL spearphish targeting corporate users in Kentucky, with tactics including aggressive device fingerprinting and fake Google Captchas.
Mitigations
Block the specified domains on corporate firewalls and endpoint security solutions.
Educate users about phishing risks even on pages that purport to use MFA.
Remind users of phishing risks for their personal accounts that they access even if they are on corporate devices.
Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.


