- 24 Jun 2025
- 2 Minutes to read
- Print
- DarkLight
Phish Wire - June 24 2025
- Updated on 24 Jun 2025
- 2 Minutes to read
- Print
- DarkLight
In early to mid-June, there was a notable increase in phishing campaigns targeting accounts associated with Amazon, Microsoft, and Netflix. These campaigns utilized sophisticated phishing kits designed to collect extensive personal information, including Social Security numbers and bank access credentials.
Many Microsoft-themed attacks employed advanced evasive tactics, such as heavily obfuscated scripts, anti-scanning measures, and simulated multi-factor authentication steps. Additionally, one particular Amazon phishing kit was discovered that could gather a wide range of personal data beyond just passwords. On the other hand, phishing links related to Netflix included unique identifiers likely intended for tracking campaign targets. Here are some examples and highlights from these campaigns.
loginmicrosoftcommon365authmked1c[.]bdfkfwwgyqon[.]es
xiotecltd[.]com/support/10be73e78
prime-siginauth[.]authecsbeaneyr[.]website
managesecure[.]log-in[.]information-reactivate-statement[.]memberprime[.]vlx[.]yeo[.]mybluehost[.]me
rmuba[.]ewetanign[.]ru
office[.]trustmark[.]cloud
gfmw[.]guestaccessportal[.]com
oneonline[.]chirping[.]it[.]com
Amazon Phishing for SSN, Bank Access Numbers and More
On June 12th, a staff member at a Maryland school clicked on the Amazon phishing attack below on their work device.
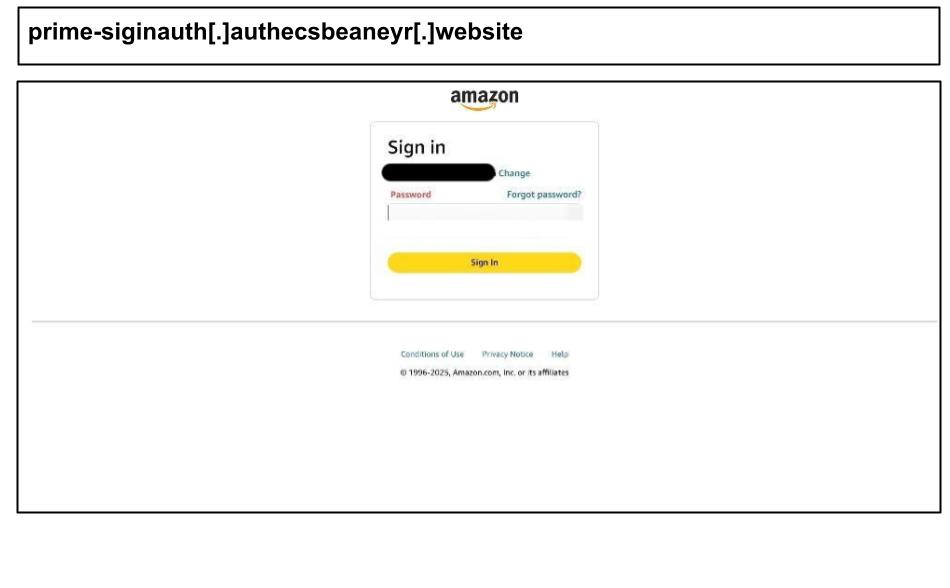
The page contained a data filtration configuration embedded deeply in its JSON:
This indicates a configurable phishing kit capable of requesting sensitive identity and financial data, including:
Social Security Number (SSN)
National IDs
Bank Account Numbers
Online banking access numbers
Passport & civil IDs
Mother’s maiden name (MMN)
On June 12, a similar Amazon phishing attack was clicked by an employee at a Virginia organization, also targeting their personal account on their work device.
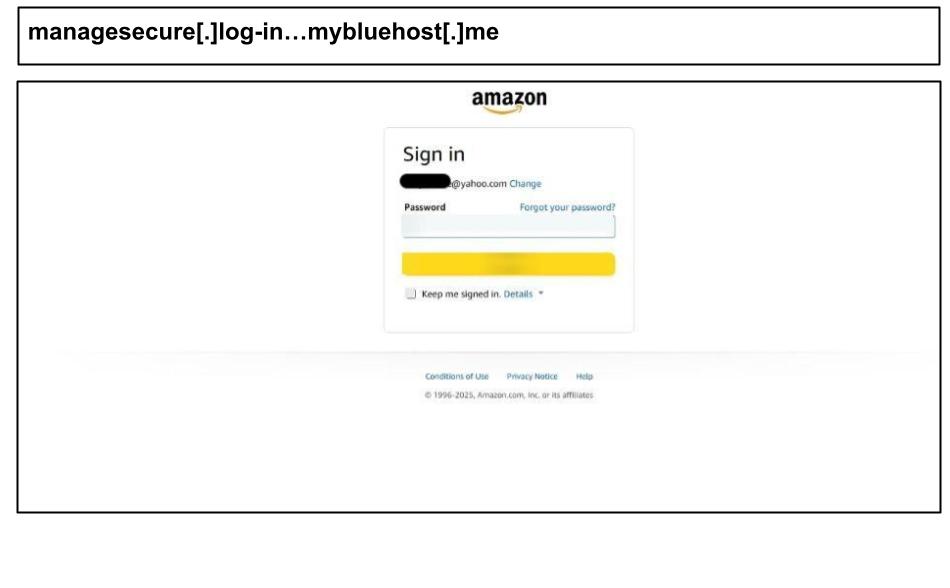
The login UI included an email validation that exactly mimics Amazon’s two-step sign-in process. The mybluehost[.]me domain was also used in earlier Amazon phishing attacks reported earlier.
Microsoft O365 / Sharepoint Phishing
On June 9, a user at a Kentucky organization clicked this Office 365 spearphish hosted on a Russian top-level domain.
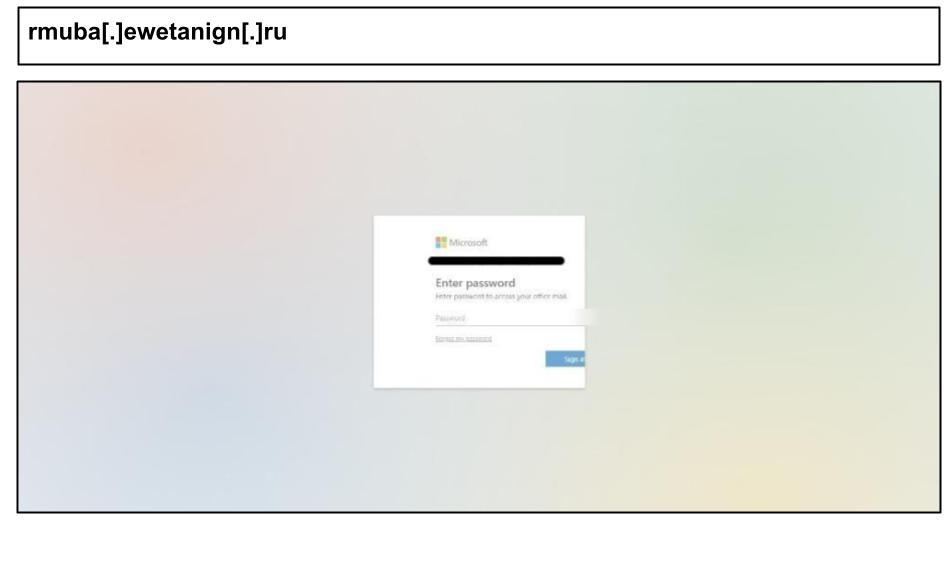
The HTML included tags that prevent web crawlers from caching or indexing the page, and clipboard interference that prevents analysts from copying content. It also included a ~1 million-character JavaScript blob likely intended to thwart static analysis.
On June 10, a staff member at a Kentucky organization clicked this Microsoft phishing link via a voicemail lure.
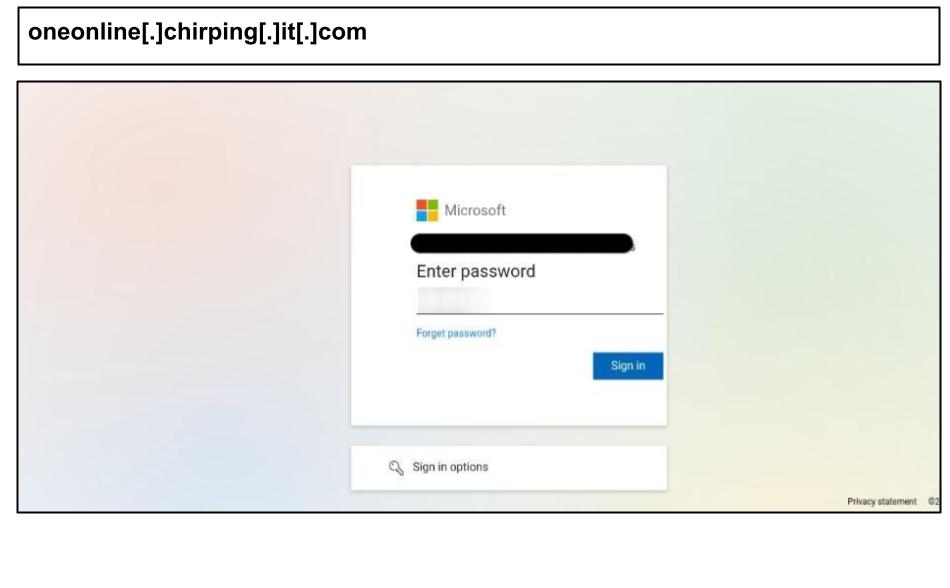
The attack presented the user with multiple sign-in prompts and ultimately displayed a message stating that a voicemail had “expired,” redirecting the user to Microsoft. Voicemail lures like this are commonly used in business email compromise (BEC) campaigns to trick users into clicking malicious links.
On June 11, a Texas administrator clicked this spearphishing link. The page used advanced evasive scripting with encrypted payloads, anti-analysis techniques, and an obfuscated user interface.
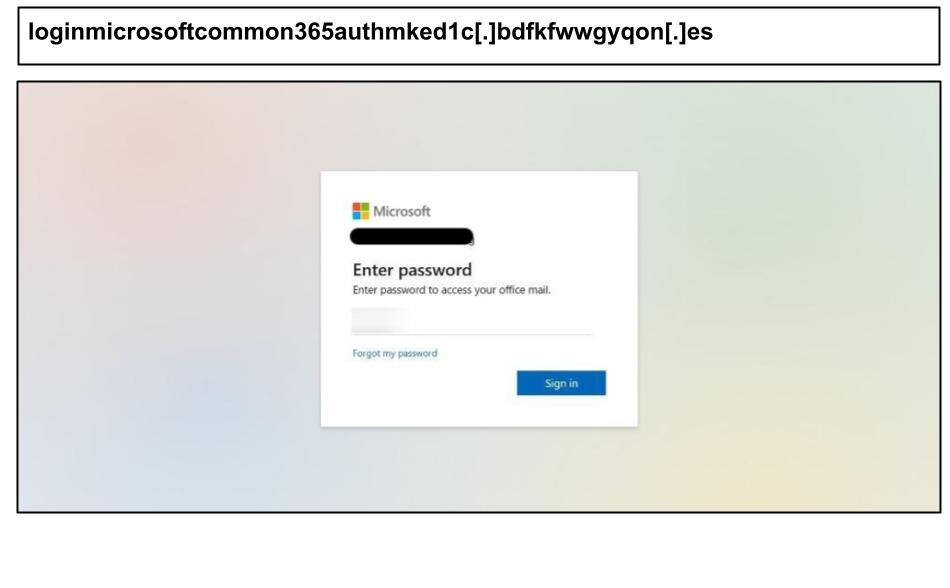
On the same day, an employee at an Iowa organization clicked on this Microsoft 365 phishing link.
The URL structure perfectly mimicked Microsoft’s OAuth flow. The phishing page also employed session tracking and device fingerprinting, perhaps to track the effectiveness of the phishing campaign and gather intel on the user.
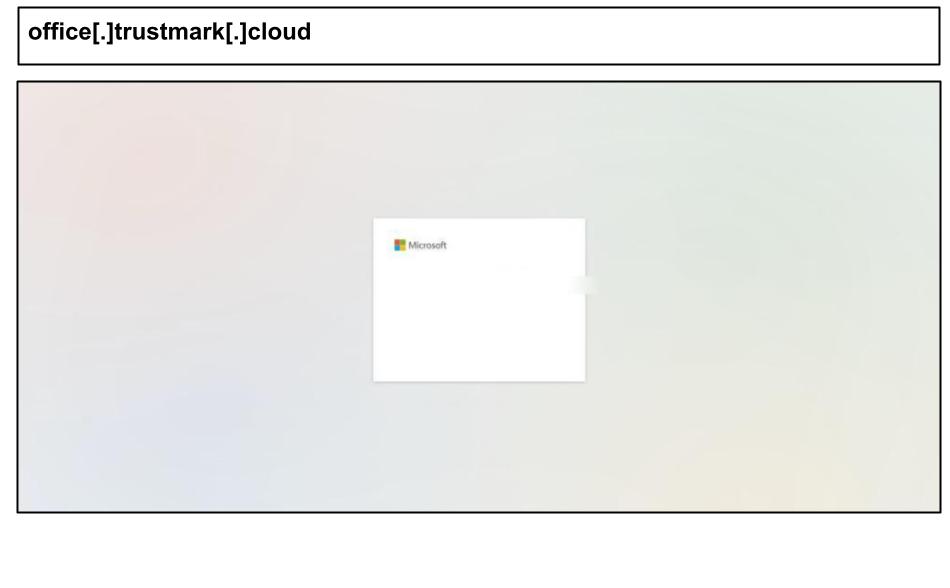
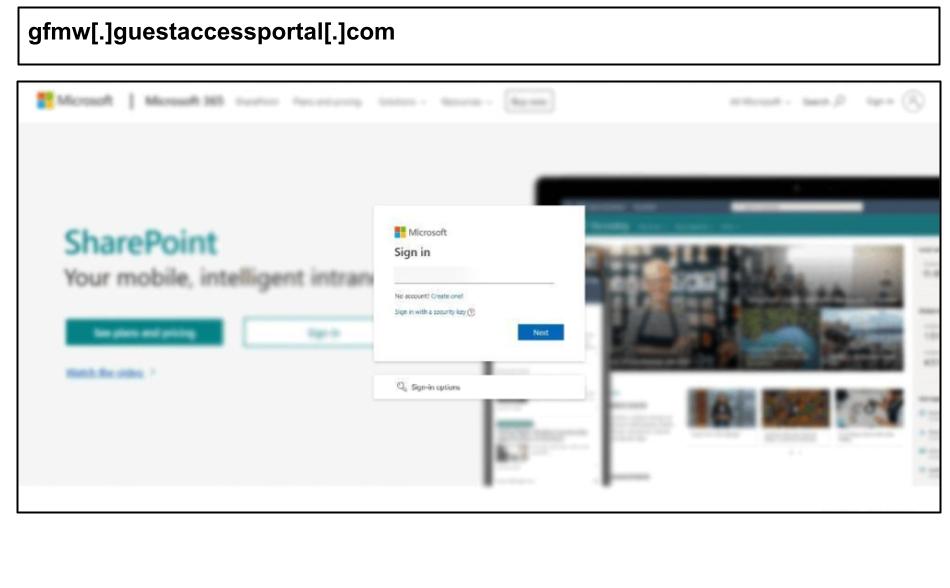
On June 17, a staff member at a Minnesota organization clicked this SharePoint-themed phishing attack, which simulated multiple MFA flows like push approvals, SMS verification, and authenticator app prompts.
Netflix Phishing Campaigns and User Tracking
The same period also saw an increase in Netflix phishing campaigns, which tracked click-through rates and device information. For instance, on June 15th, a staff member at a Texas organization clicked a Netflix-themed phishing link on their work device.
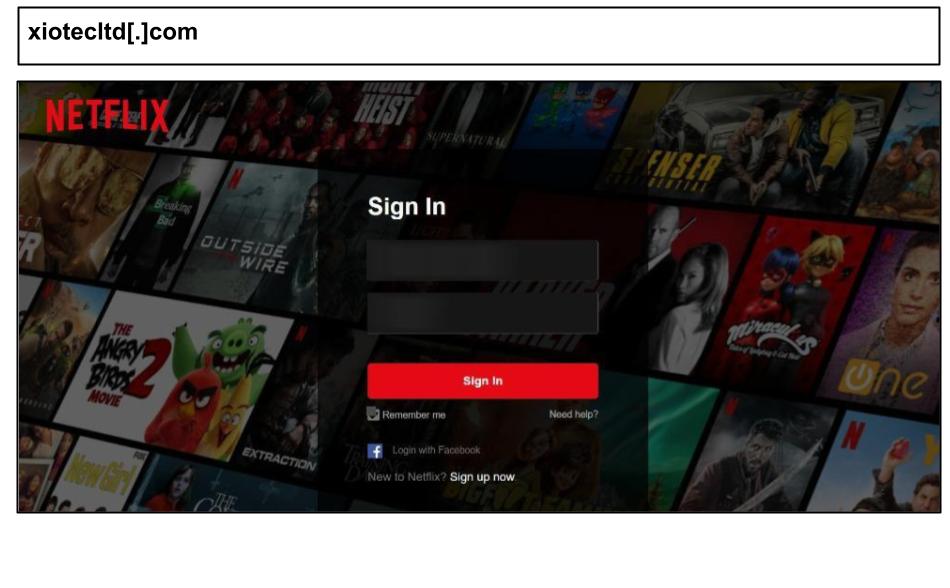
The page included watermarking and campaign identifiers used to track individual campaign deployments or the origin of victims.
Mitigations
Block the specified domains on corporate firewalls and endpoint security solutions.
Educate users about phishing risks even on pages that purport to use MFA
Remind users of phishing risks for their personal accounts that they access even if they are on corporate devices
Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.


