- 11 Mar 2025
- 1 Minute to read
- Print
- DarkLight
Phish Wire - March 11 2025
- Updated on 11 Mar 2025
- 1 Minute to read
- Print
- DarkLight
There have been record surges in zero day phishing activity via social media and business collaboration platforms, completely flanking traditional security architecture that exclusively protects the inbox.
Here are some examples and highlights.
managepages[.]gsj[.]wax[.]mybluehost[.]me/ap/t5aqg…
filerdcyrus[.]site/?zo51p
youn[.]watchstreamin-tv[.]io/
1ping-tck[.]com/o8iu3/
ctrlrmmlxdoccssecured3d3267893receipt[.]filemanagepro[.]com/jNgE5
g01q[.]dianausil[.]com
www-amzonmembershipserb[.]ampes[.]org/signin
myevitetoyou[.]info/aol[.]html
placevotespotifyprogram[.]ct[.]ws/en/2
busines[.]metaverificationofaccount[.]com/business-help-center
ywnjb[.]ms87569[.]de
Document Share Spearphish
A staff member at a Florida organization clicked on a Microsoft phishing link through a document share.
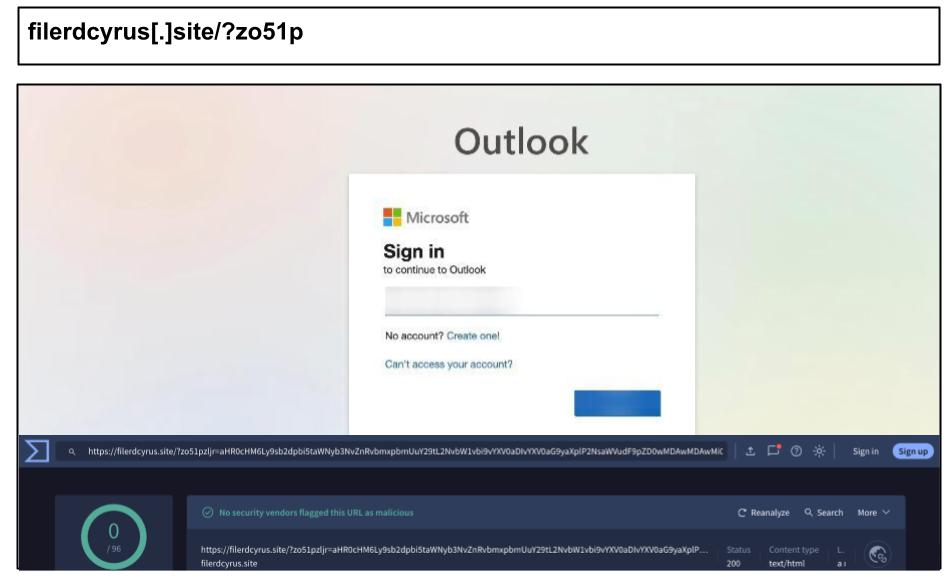
As the phishing link was delivered via a fileshare instead of traditional email phishing, it was 100% undetected by the Virus Total community. The same period saw a record surge in stealthy Microsoft phishing across organizations in Texas, Idaho, Minnesota, Florida, Tennessee, among others.
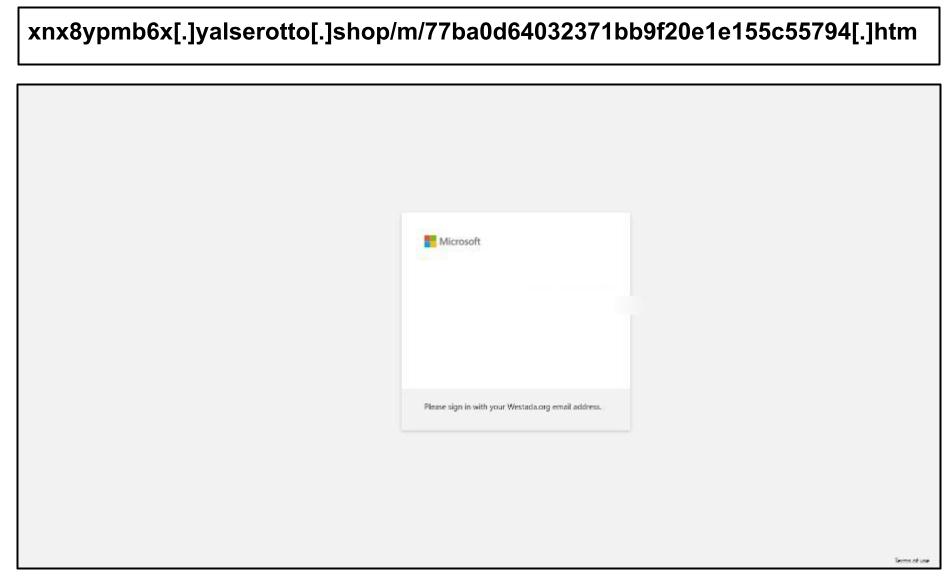
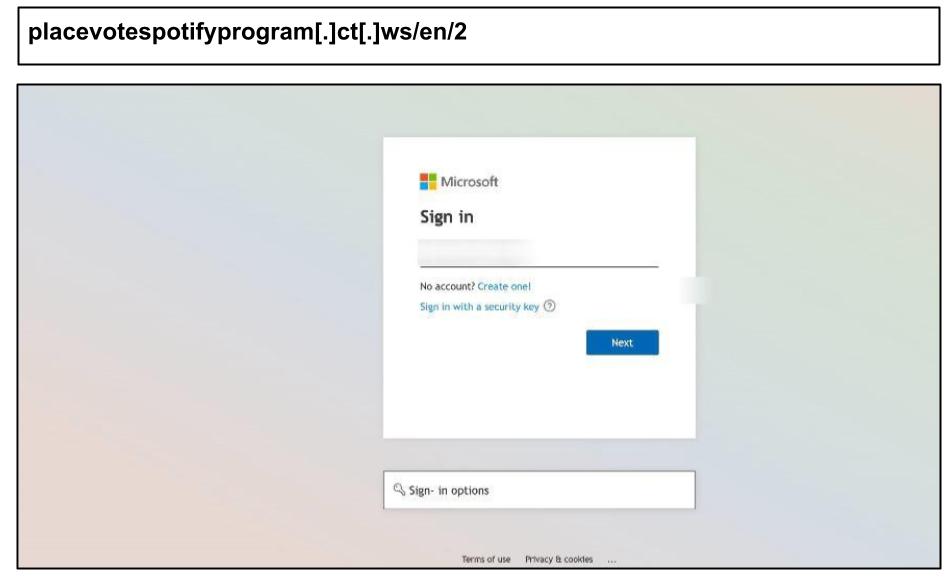
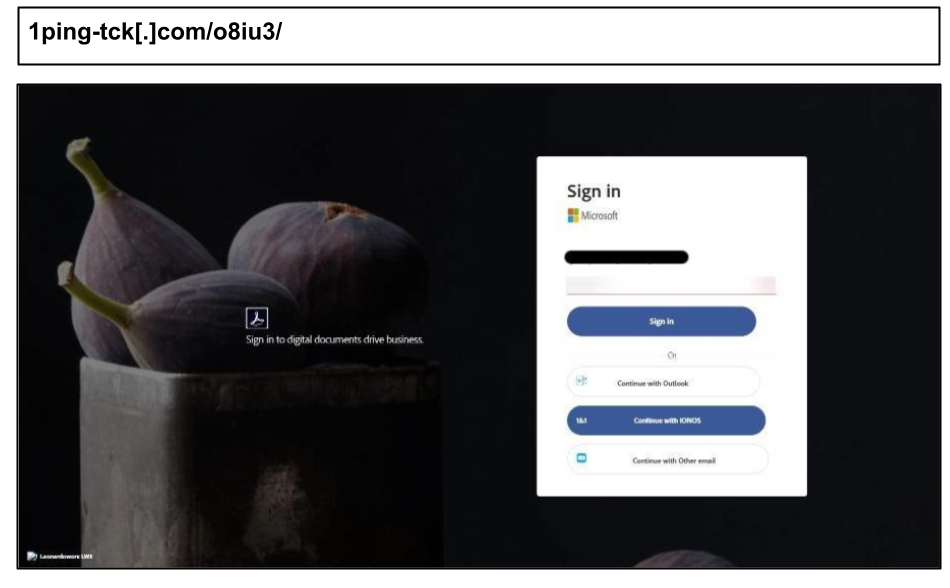
These links reference a number of fileshare and non-email applications like Spotify and Adobe. A notable tactic also included URL parameters that mimicked Microsoft's authentication flow.
Social Media Phishing Through Policy Violations
Multiple users were targeted via Meta’s Facebook and Instagram platforms. For example, a staff member at a Texas organization received a message about a Facebook policy violation that warned them of an imminent account suspension pending an appeal. The phishing link itself led to a fake appeal page.
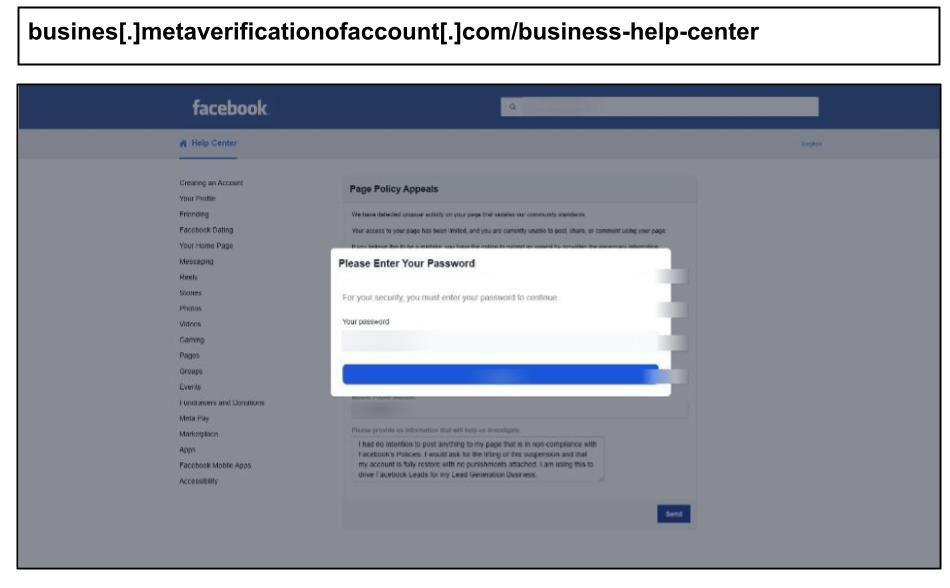
Fear of social media account suspensions is a powerful driver for many people, particularly if there is a livelihood based on a social following. Another staff member at the same organization fell for an Instagram phishing attack the day before.
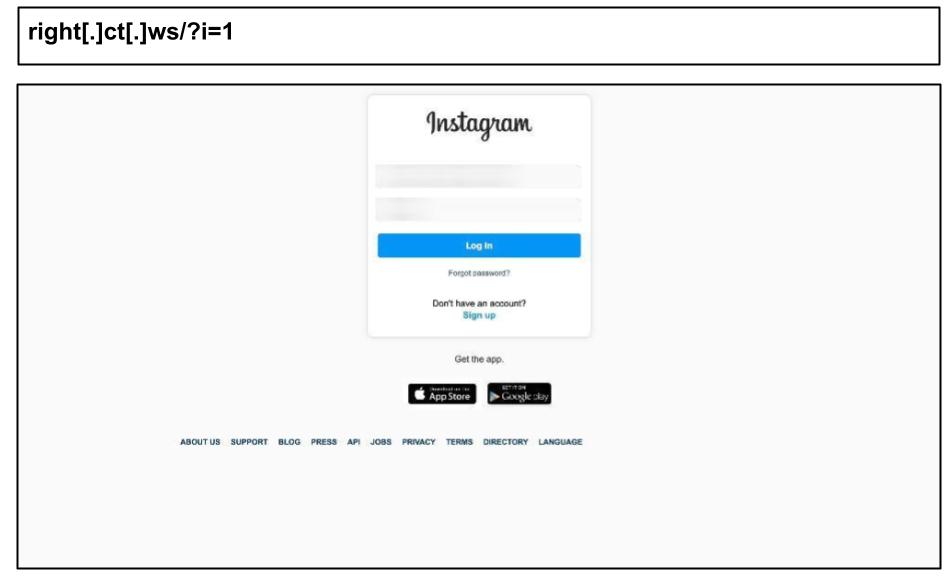
As these phishing links tend to be delivered via native messaging apps, they completely flank typical corporate protections.
Personal Phishing Attacks on Work Devices
The surge included a wave of personal phishing attacks targeting work devices associated with Amazon, Netflix, Yahoo, and other personal accounts.
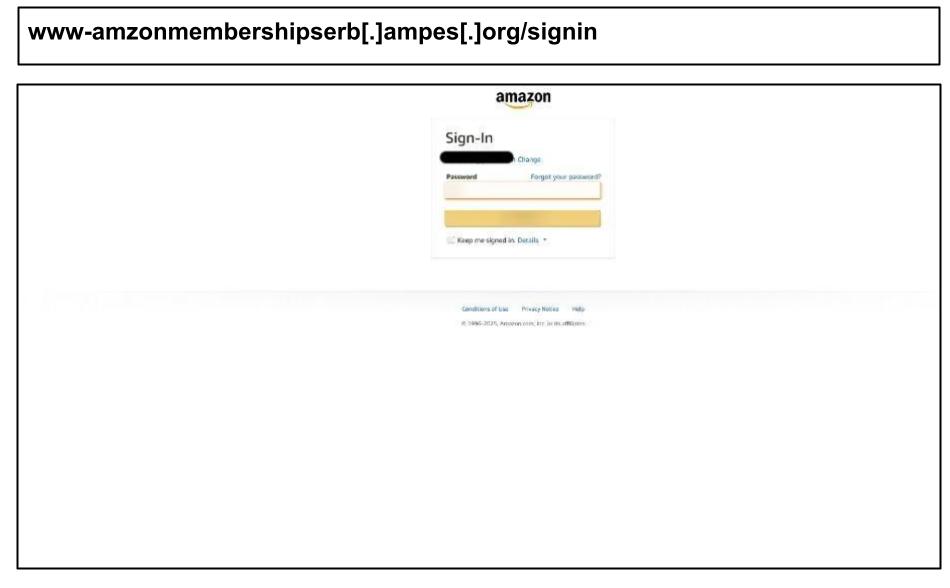
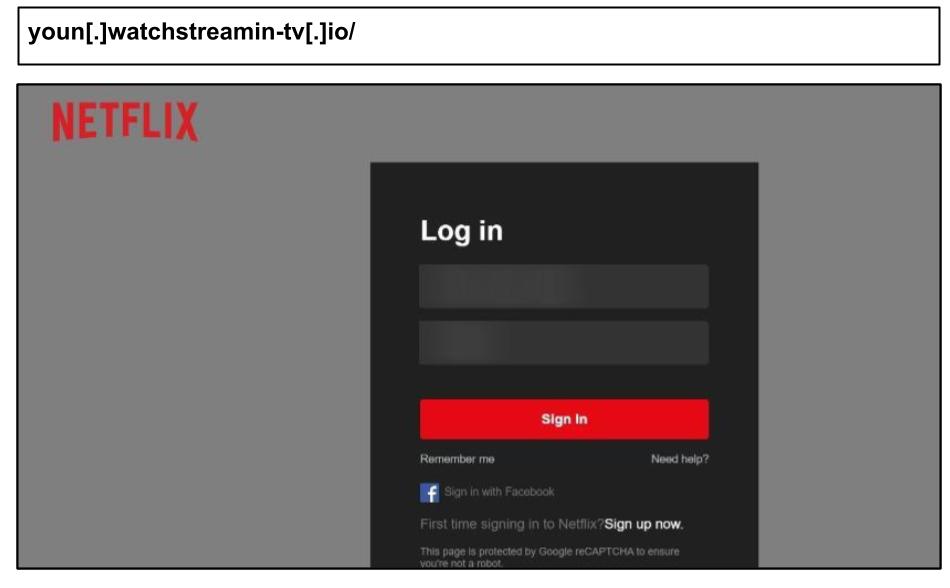
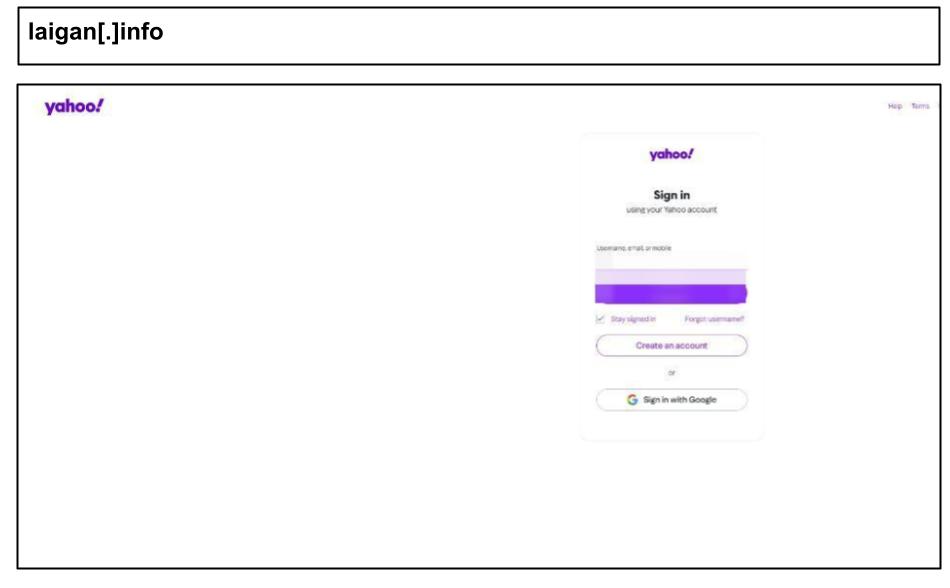
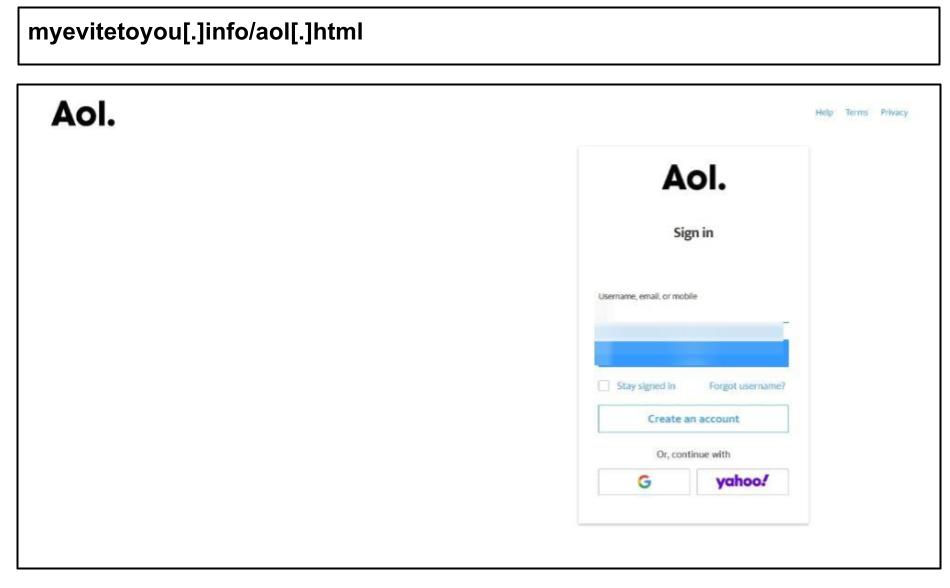
As seen in prior reports, staff are increasingly accessing personal accounts and applications on work devices, which remains a key vulnerability even in otherwise well protected corporate environments.
Mitigations
Block the specified domains on corporate firewalls and endpoint security solutions.
Increase awareness about phishing on business collaboration, personal, and social media platforms. Phishing is not only a corporate email issue.
Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.


